The Growth of Corporate Data (infographic)
•
1 j'aime•1,379 vues
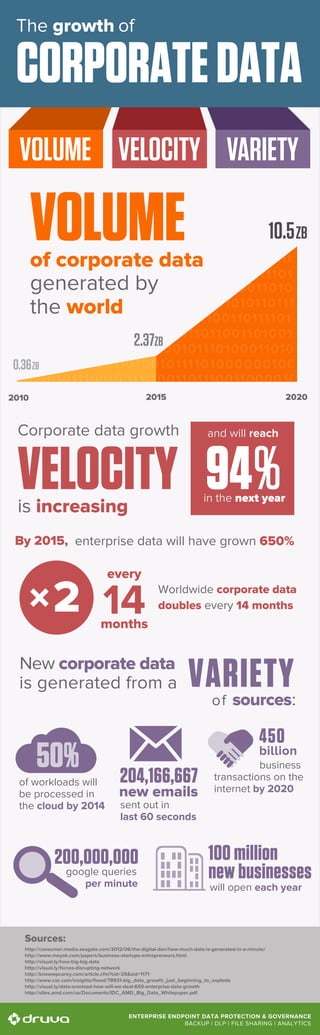
The volume of corporate data is exploding. Worldwide corporate data now doubles every 14 months and will reach 10.5 ZB by 2020. How and why is corporate data increasing so rapidly?
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
The Anatomy of Growth: How a well-implemented CRM system is essential to sust...

The Anatomy of Growth: How a well-implemented CRM system is essential to sust...Business Marketing Association (SoCal BMA)
Recommandé
The Anatomy of Growth: How a well-implemented CRM system is essential to sust...

The Anatomy of Growth: How a well-implemented CRM system is essential to sust...Business Marketing Association (SoCal BMA)
Using Digital Threat Intelligence Management (DTIM) to Combat Threats

Using Digital Threat Intelligence Management (DTIM) to Combat ThreatsEnterprise Management Associates
Dynamics of Cloud and its Impact on Software Development - IT Operations and ...

Dynamics of Cloud and its Impact on Software Development - IT Operations and ...Hasan Basri AKIRMAK, MSc,ExecMBA
Contenu connexe
Similaire à The Growth of Corporate Data (infographic)
Using Digital Threat Intelligence Management (DTIM) to Combat Threats

Using Digital Threat Intelligence Management (DTIM) to Combat ThreatsEnterprise Management Associates
Dynamics of Cloud and its Impact on Software Development - IT Operations and ...

Dynamics of Cloud and its Impact on Software Development - IT Operations and ...Hasan Basri AKIRMAK, MSc,ExecMBA
Similaire à The Growth of Corporate Data (infographic) (20)
Solving The Data Growth Crisis: Solix Big Data Suite

Solving The Data Growth Crisis: Solix Big Data Suite
Using Digital Threat Intelligence Management (DTIM) to Combat Threats

Using Digital Threat Intelligence Management (DTIM) to Combat Threats
Digital transformation and the role of cloud computing Capgemini Mark Skilt...

Digital transformation and the role of cloud computing Capgemini Mark Skilt...
Big Data from idea to service provider from a Consulting perspective - a quic...

Big Data from idea to service provider from a Consulting perspective - a quic...
Dynamics of Cloud and its Impact on Software Development - IT Operations and ...

Dynamics of Cloud and its Impact on Software Development - IT Operations and ...
Clearswift f5 information_visibility_reducing_business_risk_whitepaper

Clearswift f5 information_visibility_reducing_business_risk_whitepaper
White Paper: Internal vs. External Identity Access Management 

White Paper: Internal vs. External Identity Access Management
Bringing Cloud Computing Out of the Shadows: Shine the light on Shadow IT wit...

Bringing Cloud Computing Out of the Shadows: Shine the light on Shadow IT wit...
Event-driven Business: How Leading Companies Are Adopting Streaming Strategies

Event-driven Business: How Leading Companies Are Adopting Streaming Strategies
Plus de Druva
Plus de Druva (20)
Protecting Corporate Data When an Employee Leaves: Survey and Best Practices

Protecting Corporate Data When an Employee Leaves: Survey and Best Practices
New Strategies for More Effective Remote/Branch Office Data Protection

New Strategies for More Effective Remote/Branch Office Data Protection
4 ways to cut your e discovery costs in half-webinar-exterro-druva

4 ways to cut your e discovery costs in half-webinar-exterro-druva
Cut End-to-End eDiscovery Time in Half: Leveraging the Cloud

Cut End-to-End eDiscovery Time in Half: Leveraging the Cloud
Taking a Proactive Approach to Combat Ransomware [Druva Webinar]![Taking a Proactive Approach to Combat Ransomware [Druva Webinar]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Taking a Proactive Approach to Combat Ransomware [Druva Webinar]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Taking a Proactive Approach to Combat Ransomware [Druva Webinar]
20 point checklist : why move backup and disaster recovery to the cloud - druva

20 point checklist : why move backup and disaster recovery to the cloud - druva
Getting a clue: uncovering the truth about your data with mobile forensics

Getting a clue: uncovering the truth about your data with mobile forensics
Where in the world is your PII and other sensitive data? by @druva inc

Where in the world is your PII and other sensitive data? by @druva inc
Black Hat 2015 Survey: The Challenge of Data Sprawl

Black Hat 2015 Survey: The Challenge of Data Sprawl
The state of data privacy with dimensional research 

The state of data privacy with dimensional research
Security and privacy of cloud data: what you need to know (Interop)

Security and privacy of cloud data: what you need to know (Interop)
AWS reInvent: Building an enterprise class backup and archival solution on AWS

AWS reInvent: Building an enterprise class backup and archival solution on AWS
Dernier
Dernier (20)
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
What's New in Teams Calling, Meetings and Devices March 2024

What's New in Teams Calling, Meetings and Devices March 2024
H2O.ai CEO/Founder: Sri Ambati Keynote at Wells Fargo Day

H2O.ai CEO/Founder: Sri Ambati Keynote at Wells Fargo Day
Powerpoint exploring the locations used in television show Time Clash

Powerpoint exploring the locations used in television show Time Clash
Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost

Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
The Growth of Corporate Data (infographic)
- 1. Sources: http://consumer.media.seagate.com/2012/06/the-digital-den/how-much-data-is-generated-in-a-minute/ http://www.moyak.com/papers/business-startups-entrepreneurs.html http://visual.ly/how-big-big-data http://visual.ly/forces-disrupting-network http://knowwpcarey.com/article.cfm?cid=25&aid=1171 http://www.csc.com/insights/flxwd/78931-big_data_growth_just_beginning_to_explode http://visual.ly/data-overload-how-will-we-deal-650-enterprise-data-growth http://sites.amd.com/us/Documents/IDC_AMD_Big_Data_Whitepaper.pdf ENTERPRISE ENDPOINT DATA PROTECTION & GOVERNANCE BACKUP | DLP | FILE SHARING | ANALYTICS VOLUME VELOCITY VARIETY The growth of CORPORATEDATA VOLUMEof corporate data generated by the world Corporate data growth VELOCITYis increasing New corporate data is generated from a VARIETY 94% and will reach in the next year Worldwide corporate data doubles every 14 months enterprise data will have grown 650%By 2015, of sources: 2 every 14months 2010 10.5ZB 2.37ZB 0.36ZB 2015 2020 204,166,667 new emails sent out in last 60 seconds of workloads will be processed in the cloud by 2014 50% business transactions on the internet by 2020 450 billion 200,000,000 google queries per minute 100 million new businesses will open each year
