Contenu connexe
Similaire à CIM_E_24.2.12
Similaire à CIM_E_24.2.12 (11)
Plus de Hemant_Kumar_Setya
Plus de Hemant_Kumar_Setya (18)
CIM_E_24.2.12
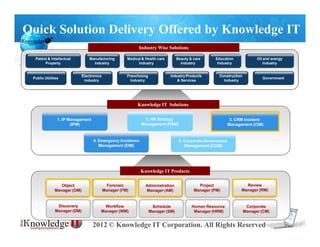
- 1. Quick Solution Delivery Offered by Knowledge IT
Industry Wise Solutions
Patent & Intellectual Manufacturing Medical & Health care Beauty & care Education Oil and energy
Property Industry Industry Industry Industry Industry
Electronics Franchising Industry Products Construction
Public Utilities Government
Industry Industry & Services Industry
Knowledge IT Solutions
1. IP Management 2. HR Strategy 3. CRM Incident
(IPM) Management (HSM) Management (CIM)
4. Emergency Incidence 5. Corporate Governance
Management (EIM) Management (CGM)
Knowledge IT Products
Object Forensic Administration Project Review
Manager (OM) Manager (FM) Manager (AM) Manager (PM) Manager (RM)
Discovery Workflow Schedule Human Resource Corporate
Manager (DM) Manager (WM) Manager (SM) Manager (HRM) Manager (CM)
2012 © Knowledge IT Corporation. All Rights Reserved
- 2. Pick and Use Functions that you Need
With any application, you effectively use only 10% of the application. But with
Knowledge IT’s SaaS applications, you use only those functions that you need.
The Knowledge IT Products
Object Forensic
Manager (OM) Manager (FM)
Review Workflow
Manager (RM) Manager (WM)
Project Administration
Manager (PM) Manager (AM)
Human Resource Discovery
(RM) Manager (HRM) Manager (DM)
Corporate Schedule
Manager (CM) Manager (SM)
Easy Third Party Software
Integration
2012 © Knowledge IT Corporation. All Rights Reserved
- 3. Knowledge IT’s 4 Types of Application
Based on Needs & User Demand
Knowledge IT offers a variety of SaaS applications which do not require initial
investment and installation effort, by providing easy-to-deploy software services at
competitive pricing. The applications supports small businesses and large
corporations, contributing to increasing effectiveness and reducing expenses.
Professional Business Enterprise Ultimate
Individuals・SOHO Small and Medium Small and Medium For large companies
Personal Offices enterprises or Enterprises or looking for full control
or Small Offices Shop owners Enterprise Subcontractors and autonomy
Best for individual Suitable for system ranging Ideal for organizations and Highly specialized set of
use and smaller from two to multiple users. businesses with large groups. administration tools in an
businesses Data access for packaged Security, access privileges as application is ideal for large groups
predetermined privilege based. well as functions can be of people in an organization. This
Typical Usage Secure user access. determined by the customer and Ultimate set comes with the freedom
Size: 1-5 Users Typical Usage set/added per category of users to build a solution view and dig-
Size: 2-100s of Users from Packaged Solution. down feature according to each
Typical Usage customer’s need. Role based as well
Size: 50-1000s of Users as privilege based access control can
be set by the Business and above.
Typical Usage
Size: 100s – 1000s of Users
and above
2012 © Knowledge IT Corporation. All Rights Reserved
- 4. Incident List and Incident Registration
By this function you can
add, modify or delete the Add Incident from Options are provided to
folder/ subfolder here search your incidents
You can view all or
latest versions of the
incidents added
Incident Registration
2012 © Knowledge IT Corporation. All Rights Reserved
- 6. Responses to Incident
Incident Response Icon
Content as the response to
the incident
2012 © Knowledge IT Corporation. All Rights Reserved
- 7. Categorizing Incident by Folders
Folder Register with
security
Folder Modify
2012 © Knowledge IT Corporation. All Rights Reserved
- 9. Escalation Mail and Views
Escalation mail is observed in Review
Manager
Escalation mails can be viewed by clicking
on subject link
2012 © Knowledge IT Corporation. All Rights Reserved