CentOS Implementation - Who Will Support you?
•
0 j'aime•165 vues
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
OSSIM User Training: Get Improved Security Visibility with OSSIM

OSSIM User Training: Get Improved Security Visibility with OSSIM
IDS for Security Analysts: How to Get Actionable Insights from your IDS

IDS for Security Analysts: How to Get Actionable Insights from your IDS
From Zero To Hero: Continuous Container Security in 4 Simple Steps- A WhiteSo...

From Zero To Hero: Continuous Container Security in 4 Simple Steps- A WhiteSo...
Technical track kevin cardwell-10-00 am-solid-defense

Technical track kevin cardwell-10-00 am-solid-defense
New OSSIM v5.0 - Get Security Visibility Faster & Easier Than Ever

New OSSIM v5.0 - Get Security Visibility Faster & Easier Than Ever
Best Practices for Configuring Your OSSIM Installation

Best Practices for Configuring Your OSSIM Installation
Similaire à CentOS Implementation - Who Will Support you?
Similaire à CentOS Implementation - Who Will Support you? (20)
Everything you need to know about your open source support contract

Everything you need to know about your open source support contract
VMWare Tech Talk: "The Road from Rugged DevOps to Security Chaos Engineering"

VMWare Tech Talk: "The Road from Rugged DevOps to Security Chaos Engineering"
Cyber security - It starts with the embedded system

Cyber security - It starts with the embedded system
Security and DevOps: Agility and Teamwork - SID315 - re:Invent 2017

Security and DevOps: Agility and Teamwork - SID315 - re:Invent 2017
Embedded Systems Security: Building a More Secure Device

Embedded Systems Security: Building a More Secure Device
Embedded Systems Security: Building a More Secure Device

Embedded Systems Security: Building a More Secure Device
Dernier
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Exploring iOS App Development: Simplifying the Process

Exploring iOS App Development: Simplifying the ProcessEvangelist Apps https://twitter.com/EvangelistSW/
CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE

CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE9953056974 Low Rate Call Girls In Saket, Delhi NCR
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...MyIntelliSource, Inc.
Dernier (20)
Tech Tuesday-Harness the Power of Effective Resource Planning with OnePlan’s ...

Tech Tuesday-Harness the Power of Effective Resource Planning with OnePlan’s ...
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...
Optimizing AI for immediate response in Smart CCTV

Optimizing AI for immediate response in Smart CCTV
The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...

The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...
Exploring iOS App Development: Simplifying the Process

Exploring iOS App Development: Simplifying the Process
How To Troubleshoot Collaboration Apps for the Modern Connected Worker

How To Troubleshoot Collaboration Apps for the Modern Connected Worker
W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...

W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...
Shapes for Sharing between Graph Data Spaces - and Epistemic Querying of RDF-...

Shapes for Sharing between Graph Data Spaces - and Epistemic Querying of RDF-...
CALL ON ➥8923113531 🔝Call Girls Kakori Lucknow best sexual service Online ☂️

CALL ON ➥8923113531 🔝Call Girls Kakori Lucknow best sexual service Online ☂️
CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE

CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE
The Ultimate Test Automation Guide_ Best Practices and Tips.pdf

The Ultimate Test Automation Guide_ Best Practices and Tips.pdf
A Secure and Reliable Document Management System is Essential.docx

A Secure and Reliable Document Management System is Essential.docx
Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...

Steps To Getting Up And Running Quickly With MyTimeClock Employee Scheduling ...
CentOS Implementation - Who Will Support you?
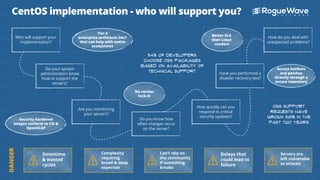
- 1. CentOS implementation - who will support you? Who will support your implementation? How do you deal with unexpected problems? Do your system administrators know how to support the servers? Have you performed a disaster recovery test? Are you monitoring your servers? How quickly can you respond to critical security updates? Do you know how often changes occur on the server? Security hardened images conform to CIS & OpenSCAP Complexity requiring broad & deep expertise Can’t rely on the community if something breaks Delays that could lead to failure Downtime & wasted cycles Servers are left vulnerable to attacks 54% of developers choose OSS packages based on availability of technical support OSS support requests have grown 50% in the past two years Tier 4 enterprise-architects 24x7 that can help with entire ecosystems No vendor lock-in Access hotfixes and patches directly through a secure repository Better SLA than Linux vendors
