CNS599_TestPlanControl
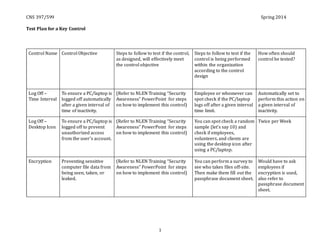
- 1. CNS 397/599 Spring 2014 1 Test Plan for a Key Control Control Name Control Objective Steps to follow to test if the control, as designed, will effectively meet the control objective Steps to follow to test if the control is being performed within the organization according to the control design How often should control be tested? Log Off – Time Interval To ensure a PC/laptop is logged off automatically after a given interval of time of inactivity. (Refer to NLEN Training “Security Awareness” PowerPoint for steps on how to implement this control) Employee or whomever can spot check if the PC/laptop logs off after a given interval time limit. Automatically set to perform this action on a given interval of inactivity. Log Off – Desktop Icon To ensure a PC/laptop is logged off to prevent unauthorized access from the user’s account. (Refer to NLEN Training “Security Awareness” PowerPoint for steps on how to implement this control) You can spot check a random sample (let’s say 10) and check if employees, volunteers, and clients are using the desktop icon after using a PC/laptop. Twice per Week Encryption Preventing sensitive computer file data from being seen, taken, or leaked. (Refer to NLEN Training “Security Awareness” PowerPoint for steps on how to implement this control) You can perform a survey to see who takes files off-site. Then make them fill out the passphrase document sheet. Would have to ask employees if encryption is used, also refer to passphrase document sheet.
- 2. CNS 397/599 Spring 2014 2 Access Controls To ensure that employees, volunteers, clients, and visitors each their own personal login Refer to NLEN Information Security Design and Test Control to view screenshots on how to create user accounts By following the screenshots an admin at NLEN will be able to see that they are following the steps properly to create users for volunteers, clients, and visitors Monthly by checking to see what user accounts have been disabled, passwords are being changed and steps being taken each time a new volunteer, client or visitor walk into NLEN. File Inventory To ensure that clients paper files are secured properly and stored in a safe area and logged accurately Securing the boxes that store client paper files with masking tape and creating a log which is available in the NLEN Training Awareness PowerPoint Securing the boxes and creating the log will allow NLEN to be able to see who has accessed the paper files Weekly by checking the log to see if employees have signed in/out paper files accurately and ensuring that the boxes stayed secured with masking tape at all times. Server Room To ensure that computer logs are done to make sure that no system violations occurred In command prompt run “sfc /scannow” this will let you know if a violation occurred Have a manual set timer on all computers and then check a concatenated log file and search for and integrity violations Daily by checking the log files every day you will know if a violation occurred; addressing the problem afterwards ASAP.
- 3. CNS 397/599 Spring 2014 3 Inventory To identify network devices for accountability, trouble shooting, secure the devices, and know which devices are assigned to staff. Periodic spot checks by manager(s) or designated staff member(s) of assets against the inventory list. When new assets are added or removed from the network and when there is new staff hired and staff leaving NLEN the inventory should reflect the changes. Upon increase/decrease of assets and staff. When no change of assets or staff at least once annually. Temporary Use of Equipment Maintain accountability of portable devices. Periodic spot checks by manager(s) or designated staff member(s) of assets against the inventory list. All equipment issued and accounted for by custody form completed by user. Check weekly to maintain accountability. If no issues check monthly.
- 4. CNS 397/599 Spring 2014 4
- 5. CNS 397/599 Spring 2014 5