Idlewild
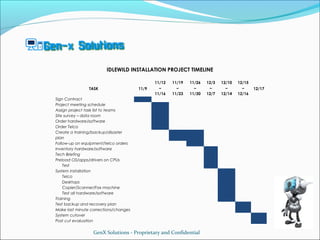
- 1. IDLEWILD INSTALLATION PROJECT TIMELINE 11/12 11/19 11/26 12/3 12/10 12/15 TASK 11/9 – – – – – – 12/17 11/16 11/23 11/30 12/7 12/14 12/16 Sign Contract Project meeting schedule Assign project task list to teams Site survey – data room Order hardware/software Order Telco Create a training/backup/disaster plan Follow-up on equipment/telco orders Inventory hardware/software Tech Briefing Preload OS/apps/drivers on CPUs Test System installation Telco Desktops Copier/Scanner/Fax machine Test all hardware/software Training Test backup and recovery plan Make last minute corrections/changes System cutover Post cut evaluation GenX Solutions - Proprietary and Confidential
- 2. HARDWARE Hardware Price Quantity Total Cost HP Desktop PC 599.99 ea. 11 $ 6,599.89 8 GB DDR3-1333MHz SDRAM (2 DIMMs) 1.0 TB Hard Drive 3.0 GHz Processor 6 MB shared cache DVD burner Keyboard & mouse Windows 7 Home 1 Yr. Kaspersky S/W HP 17” Monitor 119.99 ea. 24 $ 2,879.76 Dual Monitor Stand 56.50 ea. 11 $ 621.50 HP LaserJet Pro 200 399.99 ea. 1 $ 399.99 M276nw Color Multi- Function Laser Printer Print/Copy/Scan/Fax Duplex printing Interlink Electronics ePad 110.00 ea. 2 $ 220.00 Signature Terminal Belkin Network Interface 59.00 ea. 11 $ 649.00 Card Total Hardware Costs $10,810.14 GenX Solutions - Proprietary and Confidential
- 3. SOFTWARE Software Price Quantity Total Cost Upgrade from Windows 7 83.00 ea 11 $ 913.00 Home to Windows 7 Prof. Upgrade Windows 8 69.99 ea. 11 $ 769.89 Intuit Quick books 179.99 ea. 11 $ 1,979.89 Intuit Lacerte 395.00 ea. 11 $ 4,345.00 Engagement CS 5 @ 1,500.00 2 $ 3,290.00 – Licenses renew @ 50% of 1@ 290.00 1 license value/yr. Peachtree 2013 5@ 659.99 2 $ 1,319.98 1@ 194.00 1 $ 194.00 My PC Backup $356.40/Year 3 Years $ 1,069.20 Kaspersky Renewal after 1 3@ 49.99 4 $ 199.96 yr. Cisco ASA Security 5510 w/ 1,802.00 1 $ 1,802.00 Firewall Total Software Costs $15,882.92 GenX Solutions - Proprietary and Confidential
- 4. SERVICE & TOTAL EST. EXPENSES Software Price Quantity Total Cost Labor Fee (Estimated 25-32 hours) $100.00 $ 2500.00-$3200.00 Hardware Maintenance 3 years $500.00 $ 1500.00 User Training $125.00 $ 125.00 Help Desk Support Incl. Incl. in Maintenance Total Service Cost Estimate $ 4,125.00 - 4,825.00 Total Software Costs $15,882.92 Total Hardware Costs $10,810.14 TOTAL COSTS $30,818.06 - $31,518.06 GenX Solutions - Proprietary and Confidential
- 5. PROJECT DESCRIPTION I. Project Planning Meet with customer to review scope of work, timeline, documentation and review any changes. II. Pre-Installation • Review equipment (pre-packaged or custom), including new and existing (customer owned) hardware, software and peripherals (including racks and power equipment). • Ensure customer understands power (including voltages and receptacle types), network infrastructure, equipment and HVAC requirements and that they will be properly installed prior to the implementation. • Collect technical configuration information required for implementation. Explain any items that are unclear to ensure customer understands the information needed. III. Desktop PCs • Build and configure desktop hardware • Install and configure Windows 7 and customer specified financial software • Configure DHCP • Add users to the network • Add printer/copier/scanner to network VI. Signature Pad Setup and configure Interlink Electronics ePads GenX Solutions - Proprietary and Confidential
- 6. PROJECT DESCRIPTION – Continued V. Backups Configure to My PC Back-up(hosted vendor) and setup daily backup schedule to include data files VI. Firewall / Router / VPN Install and configure Cisco ASA security appliance firewall/router on local network • Configure Access Rules, LAN, NAT, remote desktop, direct VPN connection VII. Test Configuration VIII.End User Training IX. Project Wrap-Up X. Optional - Anti-Virus / Anti-Spam / Anti-Spyware •Install Kaspersky on server. •Install anti-virus administrator console and related agents. •Configure system to automatically update and scan local PCs on regular basis. •Uninstall current AV clients from (11) existing local PCs, as applicable. •“Push” AV client from server to 11 total PCs on network •Setup remote access page to allow remote users to “attach” to AV server •Run scans on local PCs to look for current viruses. XI. Post-Project Support per Service Level Agreement GenX Solutions - Proprietary and Confidential
- 7. SERVICE LEVEL AGREEMENT Report the System Event to our Technical Support Department available 24 by (except in the event of planned or emergency outages) by: • telephone 866-555-1212 • by email at genxsolutions.com, or • through the tech support portal on our website. SYSTEM EVENT “Priority 1” 25% or more of the functionality of the System is adversely affected by the System Event. “Priority 2” 5% - 24% of the functionality of the System is Adversely affected by the System Event. “Priority 3” 5% or less of the functionality of the System is adversely affected by the System Event. RESPONSE TIMES Priority 1 2 hours Priority 2 12 hours Priority 3 24 hours System will be monitored 24 hours a day, seven days a week. Idlewild is responsible for providing a dedicated isolated grounded receptacle (“IGR”). If Idlewild is unable to or does not provide the IGR, then the Vendor will provide the IGR on a time and materials basis at the installer’s then-current billing rates. GenX Solutions - Proprietary and Confidential
- 8. LAYOUT ePad SWITCH ePad CISCO ASA S/W ROUTER/ VPN FIREWALL SERVER Authentication HP PRINTER SERVER w/ Kaspersky S/W Internet My PC Backup Remote Access GenX Solutions - Proprietary and Confidential
- 9. CONCLUSION By choosing GenX Solutions you will get: • The leader in terms of experience, capabilities, technology, and customer service • The leading financial solutions platform available • The dedication of more than 250 GenX associates to exceed your expectations • A partner who understands your needs and has the resources and commitment to meet your changing needs in the future We sincerely thank you for this opportunity GenX Solutions - Proprietary and Confidential
