A Vulnerability I Discovered in TFTPGui
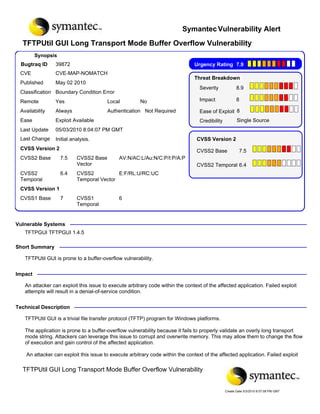
- 1. Symantec Vulnerability Alert TFTPUtil GUI Long Transport Mode Buffer Overflow Vulnerability Synopsis Bugtraq ID 39872 Urgency Rating 7.9 CVE CVE-MAP-NOMATCH Threat Breakdown Published May 02 2010 Severity 8.9 Classification Boundary Condition Error Remote Yes Local No Impact 8 Availability Always Authentication Not Required Ease of Exploit 8 Ease Exploit Available Credibility Single Source Last Update 05/03/2010 8:04:07 PM GMT Last Change Initial analysis. CVSS Version 2 CVSS Version 2 CVSS2 Base 7.5 CVSS2 Base 7.5 CVSS2 Base AV:N/AC:L/Au:N/C:P/I:P/A:P Vector CVSS2 Temporal 6.4 CVSS2 6.4 CVSS2 E:F/RL:U/RC:UC Temporal Temporal Vector CVSS Version 1 CVSS1 Base 7 CVSS1 6 Temporal Vulnerable Systems TFTPGUI TFTPGUI 1.4.5 Short Summary TFTPUtil GUI is prone to a buffer-overflow vulnerability. Impact An attacker can exploit this issue to execute arbitrary code within the context of the affected application. Failed exploit attempts will result in a denial-of-service condition. Technical Description TFTPUtil GUI is a trivial file transfer protocol (TFTP) program for Windows platforms. The application is prone to a buffer-overflow vulnerability because it fails to properly validate an overly long transport mode string. Attackers can leverage this issue to corrupt and overwrite memory. This may allow them to change the flow of execution and gain control of the affected application. An attacker can exploit this issue to execute arbitrary code within the context of the affected application. Failed exploit attempts will result in a denial-of-service condition. TFTPUtilGUI 1.4.5 is vulnerable; other versions may also be affected. TFTPUtil GUI Long Transport Mode Buffer Overflow Vulnerability Create Date 5/3/2010 8:07:08 PM GMT
- 2. attempts will result in a denial-of-service condition. TFTPUtil GUI 1.4.5 is vulnerable; other versions may also be affected. Attack Scenarios 1. An attacker locates a remotely accessible vulnerable server. 2. The attacker sends a malicious request to the TFTP service. The request will contain excessive data, memory addresses, machine code, and possibly NOP instructions. 3. When the vulnerable application processes the request, a buffer overflows and the attacker-supplied code runs in the context of the affected application. Exploits The following proof of concept is available: Jeremiah Talamantes 2010-05-02 00:00:00Z http://downloads.securityfocus.com/vulnerabilities/exploits/39872.py Mitigating Strategies Deploy network intrusion detection systems to monitor network traffic for malicious activity. Deploy NIDS to monitor the network for suspicious requests. This may help detect attacks that try to exploit this and similar vulnerabilities. Audit all applicable logs regularly. Do not follow links provided by unknown or untrusted sources. To reduce the likelihood of successful exploits, never visit sites of questionable integrity or follow links provided by unfamiliar or untrusted sources. Implement multiple redundant layers of security. Various memory-protection schemes (such as nonexecutable and randomly mapped memory segments) may hinder an attacker's ability to exploit this vulnerability to execute arbitrary code. Block sites at border that are against policy. Block external access at the network boundary, unless external parties require service. Solutions Currently we are not aware of any vendor-supplied patches. If you feel we are in error or if you are aware of more recent information, please mail us at: vuldb@securityfocus.com. Credit Jeremiah Talamantes References Web Page:TFTPGUI Homepage TFTPGUI http://sourceforge.net/projects/tftputil TFTPUtil GUI Long Transport Mode Buffer Overflow Vulnerability Create Date 5/3/2010 8:07:08 PM GMT
- 3. Change Log 2010.05.03: Initial analysis. URL https://alerts.symantec.com/loaddocument.aspx?GUID=44d1bb0e-e78e-4aa4-9f22-a48ad289e5d8 TFTPUtil GUI Long Transport Mode Buffer Overflow Vulnerability Create Date 5/3/2010 8:07:08 PM GMT