Expansion of BYOD (Bring your own device) and Mobile Security
•
1 j'aime•2,556 vues
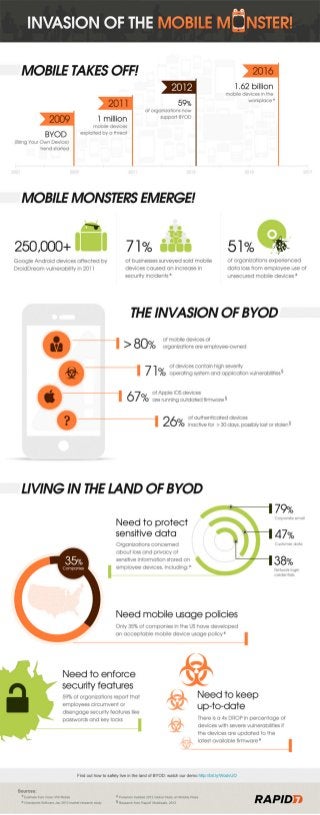
This Infographic shows that the important to understand the risks involved with the BYOD trends and mobile security.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
En vedette
En vedette (13)
BYOD: Bring Your Own Device Implementation and Security Issues

BYOD: Bring Your Own Device Implementation and Security Issues
Présentation projet de session: étude d'impacts environnementaux 

Présentation projet de session: étude d'impacts environnementaux
Le BYOD : entre perspectives et réalités pédagogiques

Le BYOD : entre perspectives et réalités pédagogiques
