Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Plus de pajo01
Plus de pajo01 (18)
Unified Service Theory and Perspectives on Services

Unified Service Theory and Perspectives on Services
Dernier
Dernier (20)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
I S1 Lesson1 Solution Sketch
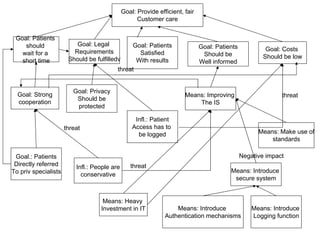
- 1. Goal: Provide efficient, fair Customer care Goal: Patients should Goal: Legal Goal: Patients Goal: Patients Requirements Goal: Costs wait for a Satisfied Should be Should be fulfilledv Should be low short time With results Well informed threat Goal: Privacy Goal: Strong Means: Improving threat Should be cooperation The IS protected Infl.: Patient threat Access has to be logged Means: Make use of standards Goal.: Patients Negative impact Directly referred Infl.: People are threat To priv specialists Means: Introduce conservative secure system Means: Heavy Investment in IT Means: Introduce Means: Introduce Authentication mechanisms Logging function