How to do hydra-Ethical hacking
- 1. How to do Hydra (Brute force Attack) to hack any E-mail Password POSTED ON 22:58 BY VIV EK Brute-force attack A password attack that does not attempt to decrypt any information, but continue to try different passwords. For example, a brute-force attack may have a dictionary of all words or a listing of commonly used passwords. To gain access to an account using a brute-force attack, a program tries all available words it has to gain access to the account. Another type of brute-force attack is a program that runs through all letters or letters and numbers until it gets a match. Although a brute-force attack may be able to gain access to an account eventually, these attacks can take several hours, minutes or Hour to run. The amount of time it takes to complete these attacks is dependent on how complicated the password is and how well the attacker knows the target. To help prevent brute-force attacks many systems will only allow a user to make a mistake in entering their username or password three or four times. If the user exceeds these attempts, the system will either lock them out of the system or prevent any future attempts for a set amount of time.
- 2. # So here we are going to use Backtrack 5, Hydra Attack. I will use fake G-mail a/c for this tutorial. # Requirements. * Backtrack 4 or 5 with Internet connection * Password.txt file (That contains Possible passwords) * Brain !! # For Eg. I took fake ID of G-mail (hackerseven5@gmail.com) as my victim it's password is '521478963', and Suppose i know the possibilities of password so, I will make password.txt file to do brute force attack !! like this >>>>>>>> #Now it's time to start attack !! using Hydra gtk, Go to>Application>Backtrack>Privilege Escalation>Password Attacks>Online Attacks>hydra-gtk.
- 3. # And it will start like this >>>>>>
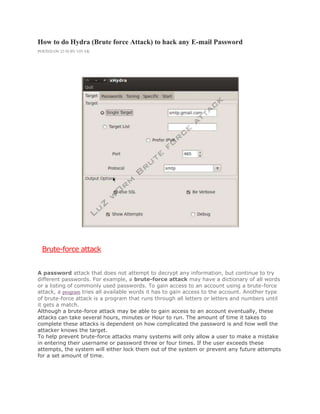
- 4. # Fill all info in this way !! * Single Target = smtp.gmail.com * Port = 465 * Protocol = smtp * mark = Use SSl, Be Verbose, Show Attempts # As shown in this Image >>>>>>>>
- 5. #After setting your Target, go on Password tab >> # Fill all info in this way !! * Username = G-mail ID (hackerseven5@gmail.com) * Password list = upload your possibilites password file (save your password.txt file on desktop)
- 6. # After all go to > Start Tab and Clik on Start !!
- 7. # So, your Brute Force Attack has been started !!
- 8. # After all it will try Brute force attack using every password and try to login with possibilities password, if you were lucky !! then it will show successful message like this >>>>>
- 9. >>>>>>>>>>>>>>>>>Viv EK<<<<<<<<<<<<<<<<<<< I no using this attack it is very hard to hack any G-mail Password, but it can help you to recover your hacked ID or forget password.
