Des1
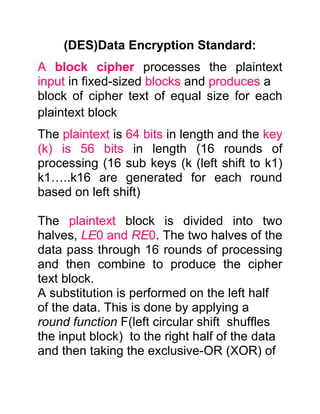
- 1. (DES)Data Encryption Standard: A block cipher processes the plaintext input in fixed-sized blocks and produces a block of cipher text of equal size for each plaintext block The plaintext is 64 bits in length and the key (k) is 56 bits in length (16 rounds of processing (16 sub keys (k (left shift to k1) k1…..k16 are generated for each round based on left shift) The plaintext block is divided into two halves, LE0 and RE0. The two halves of the data pass through 16 rounds of processing and then combine to produce the cipher text block. A substitution is performed on the left half of the data. This is done by applying a round function F(left circular shift shuffles the input block) to the right half of the data and then taking the exclusive-OR (XOR) of
- 2. the output of that function and the left half of the data. Permutation is performed that consists of the interchange of the two halves of the data.
- 3. Implemtation of simple DES Algorithm Program: import java.security.*; // Java Security Packages There are three security- related packages in java 1. JCA/JCE (Java Cryptography Architecture & Java Cryptography Extensions) 2. JSSE( Java Secure-Sockets Extension). 3. JAAS( Java Authentication & Authorization Service) import javax.crypto.*; // Provides the classes and interfaces for cryptographic operations. Operation include encryption, key generation and key agreement, and Message Authentication Code (MAC) generation. public class PrivateExample
- 4. { public static void main(String[] args) throws Exception { if (args.length != 1) { System.err.println("Usage:Java PrivateExample text"); System.exit(1); } byte[] plainText = args[0].getBytes("UTF8"); /* 8-bit Unicode Transformation Format */ System.out.println("n start generating DES key"); KeyGenerator KeyGen = KeyGenerator.getInstance("DES"); KeyGen.init(56); Key key= KeyGen.generateKey();
- 5. System.out.println("n finish generating DES key"); Cipher cipher= Cipher.getInstance("DES/ECB/PKCS5Pa dding");//electronic code book : public key crypto standard 5 System.out.println("n"+cipher.getProvid er().getInfo()); System.out.println("n start encryption "); cipher.init(Cipher.ENCRYPT_MODE,ke y); byte[] cipherText = cipher.doFinal(plainText); System.out.println("Finish Encryption"); System.out.println(new String(cipherText,"UTF8")); System.out.println("n Start Decryption"); cipher.init(Cipher.DECRYPT_MODE,ke y);
- 6. byte[] newPlainText = cipher.doFinal(cipherText); System.out.println("Final decryption"); System.out.println(new String(newPlainText, "UTF8")); } } Output :