Quantifying the call blending balance in two way communication retrial queues: analysis of correlation
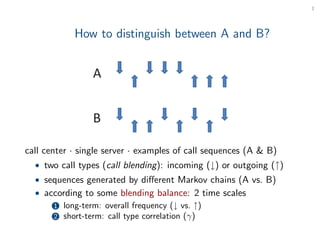
- 1. 1 How to distinguish between A and B? call center · single server · examples of call sequences (A & B) • two call types (call blending): incoming (↓) or outgoing (↑) • sequences generated by different Markov chains (A vs. B) • according to some blending balance: 2 time scales 1 long-term: overall frequency (↓ vs. ↑) 2 short-term: call type correlation (γ)
- 2. 2 γ enables to study short-term balance • coefficient of correlation γ ∈ [−1, 1] captures correlation in call sequence, from one call to the next (definition see further) • γ in [0, 1]: call type likely repeated (↓↓ & ↑↑ prevail) • γ in [−1, 0]: call type likely swapped (↓↑ & ↑↓ prevail) • the larger |γ|, the stronger the correlation
- 3. 3 Quantifying the call blending balance in two way communication retrial queues: analysis of correlation based on joint work while at Kyoto University Wouter Rogiestb,∗ & Tuan Phung-Duca,c a Graduate School of Informatics · Kyoto University · Japan b Dept. of Telecomm. & Inf. Processing · Ghent University · Belgium c Dept. of Math. & Comp. Sciences · Tokyo Institute of Technology · Japan ∗ presenting QTNA 2012 · Kyoto · 1–3 August 2012
- 4. 4 Outline 1 Introduction 2 Model & Analysis 3 Numerical examples for constant retrial rate 4 Conclusion
- 5. 5 Outline 1 Introduction 2 Model & Analysis 3 Numerical examples for constant retrial rate 4 Conclusion
- 6. 6 Context: retrial queue with call blending • retrial queue, well-known model • customers not served upon arrival enter orbit and request for retrial after some random time • applied to call center with single server • retrial queue for incoming calls (↓) • typically assigned by the Automatic Call Distributor (ACD) • no queue for outgoing calls (↑) • initiated after some idle time by the ACD, or by operator
- 7. 7 Call blending: A vs. B earlier/ongoing work [A] for classical retrial rate → J. R. Artalejo & T. Phung-Duc, QTNA 2011. [B] for constant retrial rate → T. Phung-Duc & W. Rogiest, ASMTA 2012. findings on blending balance • long-term: identical for A and B • short-term: (to be studied!) (no answer from steady-state expressions alone) (intuitive: should be quite different)
- 8. 8 Outline 1 Introduction 2 Model & Analysis 3 Numerical examples for constant retrial rate 4 Conclusion
- 9. 9 Assumptions: {α, λ, µ, ν1 , ν2 } all: rates of exponential distributions α outgoing call rate • when server turns idle, outgoing call after exp. distr. time λ primary incoming call rate (Poisson arrivals) • finding idle server: receive service immediately • finding busy server: enter orbit µ retrial rate (within orbit) A classical: nµ, B constant: µ(1 − δ0,n ), with n : number of customers in orbit δ0,n : Kronecker delta ν1 service rate incoming call ν2 service rate outgoing call
- 10. 10 Markov chain • S(t): server state at time t, 0 if the server is idle, S(t) = 1 if the server is providing an incoming service, 2 if the server is providing an outgoing service, • N(t): number of calls in orbit at time t • {(S(t), N(t)); t ≥ 0} forms a Markov chain • state space {0, 1, 2} × Z+ • steady-state distribution obtained ([A] & [B]) • input for calculation of γ
- 11. 11 Correlation coefficient γ • numbering consecutive events Sk with k • Sk : incoming (Sk = s1 ) (↓) or outgoing (Sk = s2 ) (↑) • assuming steady-state E[Sk Sk+m ] − (E[Sk ])2 γm = ; m ∈ Z+ Var[Sk ] • −1 ≤ γm ≤ 1 • main interest γ1 , or γ • main challenges 1 extracting distrib. (Sk , Nk ) from distrib. (S(t), N(t)) 2 determining E[Sk Sk+1 ]
- 12. 12 From S(t) to Sk : 2 steps original Markov chain censor: remove idle periods discretize: “compensate” for ν1 = ν2
- 13. 13 In general: from (S(t), N(t)) to (Sk , Nk ) • original Markov chain: under conditions, unique stochastic equilibrium, with limt→∞ : πi,j = Pr[S(t) = i , N(t) = j], (i, j) ∈ {0, 1, 2} × Z+ • censor, with limt→∞ : πi,j = Pr[S(t) = i, N(t) = j|S(t) ∈ {1, 2}], (i, j) ∈ {1, 2}×Z+ ˜ • discretize, with limk→∞ : ηi = Pr[Sk = i] , ηi,j = Pr[Sk = i, Nk = j] , with (i, j) ∈ {1, 2} × Z+
- 14. 14 In general: from (S(t), N(t)) to (Sk , Nk ) • censor and discretize: expressions T1 = 1/ν1 , T2 = 1/ν2 , σi = Pr[S(t) = si ] , 1 T = , σ1 ν1 + σ2 ν2 T ηi,j = πi,j , i ∈ {1, 2} , j ∈ Z+ , Ti T ηi = σi , i ∈ {1, 2} . Ti
- 15. 15 Determining E[Sk Sk+1 ] and γ Choosing {s1 , s2 } = {1, 0} , leads to E[Sk ] = η1 , Var[Sk ] = η1 (1 − η1 ) , ∞ E[Sk Sk+1 ] = η1,j χj , j=0 where A classical: χj different for each j (infinite sum) B constant: χj = χ1 for j ≥ 1 (finite sum)
- 16. 16 Outline 1 Introduction 2 Model & Analysis 3 Numerical examples for constant retrial rate 4 Conclusion
- 17. 17 correlation positive when outgoing activity limited γ λν µ µ µ µ µ µ µ outgoing call rate limited (α = 0.1), primary incoming call rate varying (λ ∈ [0, λmax )), call durations matched (ν1 = ν2 = 1)
- 18. 18 correlation positive when time share matched γ λν µ µ µ µ outgoing rate (α) increasing with incoming (λ) such that time share incoming/outgoing is matched, call durations matched (ν1 = ν2 = 1)
- 19. 19 correlation strictly negative in some cases γ λ µ µ µ outgoing call rate fixed (α = 1), primary incoming call rate varying (λ ∈ [0, λmax )), call durations strongly differing (ν1 = 100, ν2 = 1) (and thus, ρ = λ/ν1 always < 0.01 in the figure)
- 20. 20 Outline 1 Introduction 2 Model & Analysis 3 Numerical examples for constant retrial rate 4 Conclusion
- 21. 21 Conclusion • distinguishing A from B with correlation coefficient γ • focus: retrial queue model for call center with call blending • from continuous-time result to discrete sequence: censor and discretize • numerical results constant retrial rate (B) illustrate variability of γ • currently working on comparison with classical retrial rate (A)
- 22. 22 Questions?