Forrester Research on OT Cybersecurity Risks and Solutions
In the new digital economy, data – and what you do with that data – is the key to success. Consumers and employees alike now demand instant access to critical information that allows them to solve problems, make informed decisions, or conduct transactions. But that’s just the part of the data equation most of us can see. To effectively compete in today’s digital market, and capitalize on the data being collected and processed, organizations need to be able to respond quickly to market shifts and consumer demands, fine tune production, realign resources, and manage infrastructure. Which is why nearly three-fourths of all organizations have begun to converge their information technology (IT) infrastructure with their traditionally isolated operational technology (OT) networks.
Recommandé
Contenu connexe
Tendances
Tendances (20)
Similaire à Forrester Research on OT Cybersecurity Risks and Solutions
Similaire à Forrester Research on OT Cybersecurity Risks and Solutions (20)
Plus de Fortinet
Plus de Fortinet (12)
Dernier
Dernier (20)
Forrester Research on OT Cybersecurity Risks and Solutions
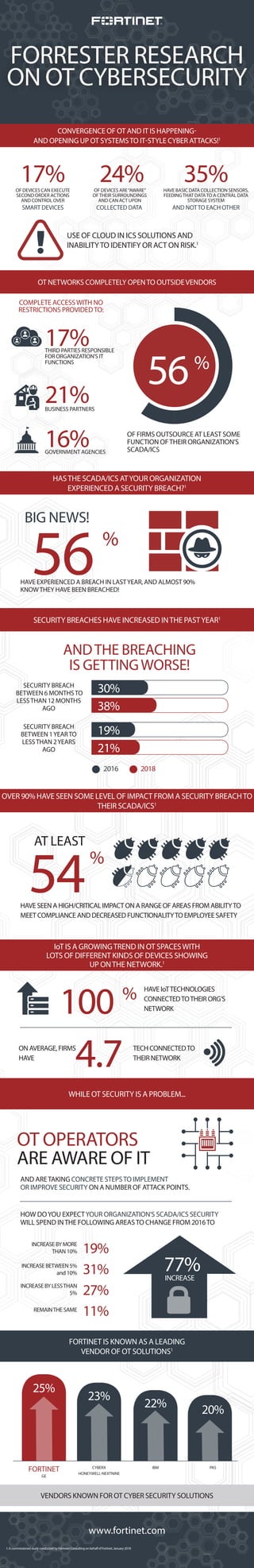
- 1. FORRESTER RESEARCH ON OT CYBERSECURITY www.fortinet.com CONVERGENCE OF OT AND IT IS HAPPENING- AND OPENING UP OT SYSTEMSTO IT-STYLE CYBER ATTACKS!1 SECURITY BREACHES HAVE INCREASED INTHE PASTYEAR1 OVER 90% HAVE SEEN SOME LEVEL OF IMPACT FROM A SECURITY BREACHTO THEIR SCADA/ICS1 OF DEVICES CAN EXECUTE SECOND ORDER ACTIONS AND CONTROL OVER SMART DEVICES USE OF CLOUD IN ICS SOLUTIONS AND INABILITYTO IDENTIFY OR ACT ON RISK.1 1: A commissioned study conducted by Forrester Consulting on behalf of Fortinet, January 2018 17% OF DEVICES ARE“AWARE” OFTHEIR SURROUNDINGS AND CAN ACT UPON COLLECTED DATA 24% HAVE BASIC DATA COLLECTION SENSORS, FEEDINGTHAT DATATO A CENTRAL DATA STORAGE SYSTEM AND NOTTO EACH OTHER 35% HASTHE SCADA/ICS ATYOUR ORGANIZATION EXPERIENCED A SECURITY BREACH?1 HAVE EXPERIENCED A BREACH IN LASTYEAR, AND ALMOST 90% KNOWTHEY HAVE BEEN BREACHED! 56% BIG NEWS! GOVERNMENT AGENCIES OT NETWORKS COMPLETELY OPENTO OUTSIDEVENDORS THIRD PARTIES RESPONSIBLE FOR ORGANIZATION’S IT FUNCTIONS 17% COMPLETE ACCESSWITH NO RESTRICTIONS PROVIDEDTO: BUSINESS PARTNERS 21% 16% OF FIRMS OUTSOURCE AT LEAST SOME FUNCTION OFTHEIR ORGANIZATION’S SCADA/ICS 56% SECURITY BREACH BETWEEN 6 MONTHSTO LESSTHAN 12 MONTHS AGO 30% 38% SECURITY BREACH BETWEEN 1YEARTO LESSTHAN 2YEARS AGO 19% 21% 20182016 ANDTHE BREACHING IS GETTINGWORSE! 54 % AT LEAST HAVE SEEN A HIGH/CRITICAL IMPACT ON A RANGE OF AREAS FROM ABILITYTO MEET COMPLIANCE AND DECREASED FUNCTIONALITYTO EMPLOYEE SAFETY IoT IS A GROWINGTREND IN OT SPACESWITH LOTS OF DIFFERENT KINDS OF DEVICES SHOWING UP ONTHE NETWORK.1 ON AVERAGE, FIRMS HAVE 4.7 TECH CONNECTEDTO THEIR NETWORK 100 % HAVE IoTTECHNOLOGIES CONNECTEDTOTHEIR ORG’S NETWORK FORTINET IS KNOWN AS A LEADING VENDOR OF OT SOLUTIONS1 VENDORS KNOWN FOR OT CYBER SECURITY SOLUTIONS FORTINET GE 25% 23% 22% 20% CYBERX HONEYWELL-NEXTNINE IBM PAS AND ARETAKING CONCRETE STEPSTO IMPLEMENT OR IMPROVE SECURITY ON A NUMBER OF ATTACK POINTS. WHILE OT SECURITY IS A PROBLEM... OT OPERATORS ARE AWARE OF IT 19% 31% HOW DOYOU EXPECTYOUR ORGANIZATION’S SCADA/ICS SECURITY WILL SPEND INTHE FOLLOWING AREASTO CHANGE FROM 2016TO 27% 11%REMAINTHE SAME INCREASE BY LESSTHAN 5% INCREASE BETWEEN 5% and 10% INCREASE BY MORE THAN 10% 77%INCREASE
