Data Breaches: The Untold Story
•
0 likes•212 views
Data breaches where millions of records are lost happen because of poor user access control. Do you know who has access to what data in your enterprise? Get better protection with BlueTalon data-centric security solution.
Report
Share
Report
Share
Download to read offline
Recommended
Realizing the Value of Social: Evolving from Social Media to Customer Experience

Realizing the Value of Social: Evolving from Social Media to Customer ExperienceTata Consultancy Services
Recommended
Realizing the Value of Social: Evolving from Social Media to Customer Experience

Realizing the Value of Social: Evolving from Social Media to Customer ExperienceTata Consultancy Services
More Related Content
What's hot
What's hot (20)
Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.

Lions, Tigers, and PHI, Oh My! The latest in data loss prevention in the cloud.
Protecting Corporate Data When an Employee Leaves: Survey and Best Practices

Protecting Corporate Data When an Employee Leaves: Survey and Best Practices
Security and privacy of cloud data: what you need to know (Interop)

Security and privacy of cloud data: what you need to know (Interop)
Taking a Proactive Approach to Combat Ransomware [Druva Webinar]![Taking a Proactive Approach to Combat Ransomware [Druva Webinar]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Taking a Proactive Approach to Combat Ransomware [Druva Webinar]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Taking a Proactive Approach to Combat Ransomware [Druva Webinar]
The EU General Protection Regulation and how Oracle can help 

The EU General Protection Regulation and how Oracle can help
ThinAir Endpoint Visibility Security HIMSS2018 Brian_Reed

ThinAir Endpoint Visibility Security HIMSS2018 Brian_Reed
Quantifying Cloud Risk for Your Corporate Leadership

Quantifying Cloud Risk for Your Corporate Leadership
Boldon James - How Data Classification can harness the power of Big Data

Boldon James - How Data Classification can harness the power of Big Data
The Definitive CASB Business Case Kit - Presentation

The Definitive CASB Business Case Kit - Presentation
New Strategies for More Effective Remote/Branch Office Data Protection

New Strategies for More Effective Remote/Branch Office Data Protection
Simplicity in Hybrid IT Environments – A Security Oxymoron?

Simplicity in Hybrid IT Environments – A Security Oxymoron?
Manage Risk by Protecting the Apps and Data That Drive Business Productivity

Manage Risk by Protecting the Apps and Data That Drive Business Productivity
Himss 2016 Lunch & Learn: Data Security in IoT (and ePHI Risks)

Himss 2016 Lunch & Learn: Data Security in IoT (and ePHI Risks)
Similar to Data Breaches: The Untold Story
Similar to Data Breaches: The Untold Story (20)
Where data security and value of data meet in the cloud ulf mattsson

Where data security and value of data meet in the cloud ulf mattsson
Data centric security key to digital business success - ulf mattsson - bright...

Data centric security key to digital business success - ulf mattsson - bright...
ciso-platform-annual-summit-2013-Hp enterprise security overview

ciso-platform-annual-summit-2013-Hp enterprise security overview
Manage Risk By Protecting the Apps and Data Infographic

Manage Risk By Protecting the Apps and Data Infographic
Manage Risk By Protecting the Apps and Data That Drive Business Productivity

Manage Risk By Protecting the Apps and Data That Drive Business Productivity
Cyber security within Organisations: A sneaky peak of current status, trends,...

Cyber security within Organisations: A sneaky peak of current status, trends,...
Top Cloud Infrastructure Practices And Strategies For Maximum Security.pdf

Top Cloud Infrastructure Practices And Strategies For Maximum Security.pdf
ISACA New York Metro, Developing, Deploying and Managing a Risk-Adjusted Data...

ISACA New York Metro, Developing, Deploying and Managing a Risk-Adjusted Data...
Webinar: Endpoint Backup is not Enough - You Need an End-user Data Strategy

Webinar: Endpoint Backup is not Enough - You Need an End-user Data Strategy
Getting Real About Security Management and “Big Data” 

Getting Real About Security Management and “Big Data”
Why Data-Centric Security Needs to be a Top Priority for Enterprises.pdf

Why Data-Centric Security Needs to be a Top Priority for Enterprises.pdf
Managing sensitive applications in the public cloud

Managing sensitive applications in the public cloud
Recently uploaded
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Data Breaches: The Untold Story
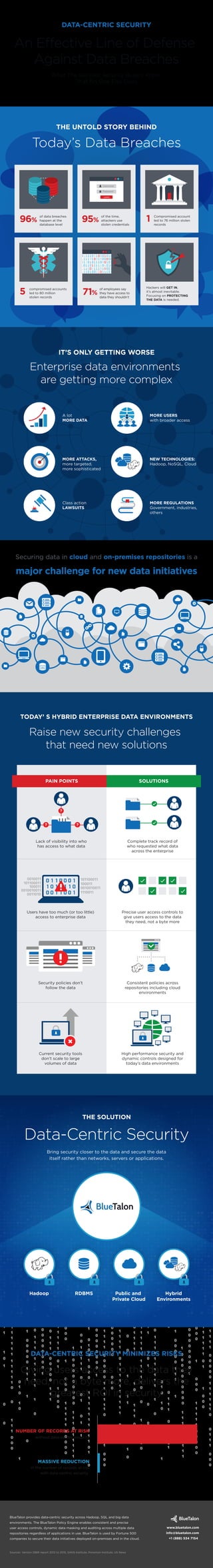
- 1. THE SOLUTION Bring security closer to the data and secure the data itself rather than networks, servers or applications. TODAY’ S HYBRID ENTERPRISE DATA ENVIRONMENTS Raise new security challenges that need new solutions Data-Centric Security DATA-CENTRIC SECURITY An Effective Line of Defense Against Data Breaches What The Savviest Security Buyers Know That No One Else Does DATA-CENTRIC SECURITY MINIMIZES RISKS BlueTalon provides data-centric security across Hadoop, SQL and big data environments. The BlueTalon Policy Engine enables consistent and precise user access controls, dynamic data masking and auditing across multiple data repositories regardless of applications in use. BlueTalon is used by Fortune 500 companies to secure their data initiatives deployed on-premises and in the cloud. Sources: Verizon DBIR report 2012 to 2015, SANS Institute, Ponemon Institute, US News www.bluetalon.com info@bluetalon.com +1 (888) 534 7154 IT’S ONLY GETTING WORSE Enterprise data environments are getting more complex Class action LAWSUITS MORE REGULATIONS Government, industries, others MORE ATTACKS, more targeted, more sophisticated NEW TECHNOLOGIES: Hadoop, NoSQL, Cloud A lot MORE DATA MORE USERS with broader access SOLUTIONSPAIN POINTS RDBMS Public and Private Cloud Hybrid Environments Hadoop Precise user access controls to give users access to the data they need, not a byte more Consistent policies across repositories including cloud environments High performance security and dynamic controls designed for today’s data environments Complete track record of who requested what data across the enterprise Users have too much (or too little) access to enterprise data Security policies don’t follow the data Current security tools don’t scale to large volumes of data Lack of visibility into who has access to what data MASSIVE REDUCTION NUMBER OF RECORDS AT RISK ? ? ? in the number of records at risk with data-centric security without data-centric security Giving users access to the data they need, not a byte more, delivers the greatest ROI in security Securing data in cloud and on-premises repositories is a major challenge for new data initiatives THE UNTOLD STORY BEHIND Today’s Data Breaches of data breaches happen at the database level 96% of the time, attackers use stolen credentials Compromised account led to 76 million stolen records 1 compromised accounts led to 80 million stolen records 5 of employees say they have access to data they shouldn’t 71% Hackers will GET IN, it’s almost inevitable. Focusing on PROTECTING THE DATA is needed. LOGIN 95%
