IBM Identity Governance Infographic
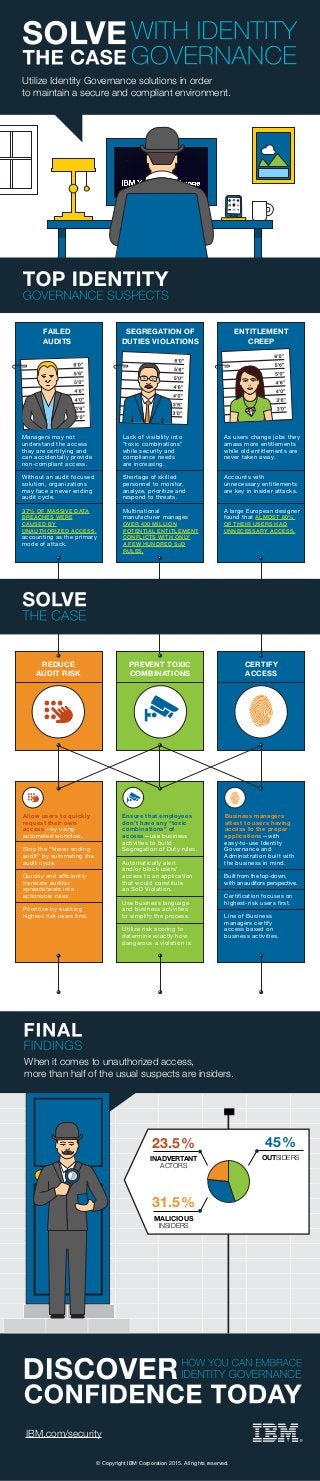
- 1. IBM.com/security ENTITLEMENT CREEP FAILED AUDITS SEGREGATION OF DUTIES VIOLATIONS As users change jobs they amass more entitlements while old entitlements are never taken away. Accounts with unnecessary entitlements are key in insider attacks. A large European designer found that ALMOST 80% OF THEIR USERS HAD UNNECESSARY ACCESS. Managers may not understand the access they are certifying and can accidentally provide non-compliant access. Without an audit focused solution, organizations may face a never ending audit cycle. 37% OF MASSIVE DATA BREACHES WERE CAUSED BY UNAUTHORIZED ACCESS, accounting as the primary mode of attack. Lack of visibility into “toxic combinations” while security and compliance needs are increasing. Shortage of skilled personnel to monitor, analyze, prioritize and respond to threats. Multinational manufacturer manages OVER 430 MILLION POTENTIAL ENTITLEMENT CONFLICTS WITH ONLY A FEW HUNDRED SoD RULES. Utilize Identity Governance solutions in order to maintain a secure and compliant environment. REDUCE AUDIT RISK PREVENT TOXIC COMBINATIONS CERTIFY ACCESS Allow users to quickly request their own access—by using automated workflow. Stop the “Never ending audit” by automating the audit cycle. Quickly and efficiently translate auditor spreadsheets into actionable rules. Prioritize by auditing highest risk users first. Ensure that employees don't have any “toxic combinations” of access—use business activities to build Segregation of Duty rules. Automatically alert and/or block users’ access to an application that would constitute an SoD Violation. Use business language and business activities to simplify the process. Utilize risk scoring to determine exactly how dangerous a violation is. Business managers attest to users having access to the proper applications—with easy-to-use Identity Governance and Administration built with the business in mind. Built from the top-down, with an auditors perspective. Certification focuses on highest-risk users first. Line of Business managers certify access based on business activities. OUTSIDERSINADVERTANT ACTORS MALICIOUS INSIDERS 45% 31.5% 23.5% When it comes to unauthorized access, more than half of the usual suspects are insiders. © Copyright IBM Corporation 2015. All rights reserved.
