Security Concerns Around the World | Infographic
•
1 j'aime•1,138 vues
Ping Identity’s 2019 consumer survey reveals interesting insights about where residents of the U.S., Australia, France and Germany differ from one another in their cybersecurity concerns and behavioral trends. Check out the infographic to see which country’s respondents are most concerned about surveillance, which are least likely to sign-on to their accounts through a third-party service and more.
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
2015 TRUSTe US Consumer Privacy Confidence Index – Infographic

2015 TRUSTe US Consumer Privacy Confidence Index – Infographic
TeleSign’s Findings on the Future of Digital Identity, Guillaume Bourcy

TeleSign’s Findings on the Future of Digital Identity, Guillaume Bourcy
TRUSTe 2014 US Consumer Confidence Privacy Report Consumer Opinion and Busine...

TRUSTe 2014 US Consumer Confidence Privacy Report Consumer Opinion and Busine...
Infographic: Philippines B2C E-Commerce Market 2019

Infographic: Philippines B2C E-Commerce Market 2019
Selfies are dead. Long live the user generated content!

Selfies are dead. Long live the user generated content!
Aligning Today's IT with the Future of Government - Peter Pin

Aligning Today's IT with the Future of Government - Peter Pin
Similaire à Security Concerns Around the World | Infographic
Similaire à Security Concerns Around the World | Infographic (20)
GRBN Trust and Personal Data Survey Report - Part 2 - Regions and countries -...

GRBN Trust and Personal Data Survey Report - Part 2 - Regions and countries -...
GRBN Trust and Personal Data Survey report - Part 1 - Concern, familiarity, t...

GRBN Trust and Personal Data Survey report - Part 1 - Concern, familiarity, t...
Ericsson ConsumerLab: Privacy, security and safety online

Ericsson ConsumerLab: Privacy, security and safety online
Strong demand across Europe for financial education in schools

Strong demand across Europe for financial education in schools
Tablets adoption and Mobile Web Usage :in Central euope

Tablets adoption and Mobile Web Usage :in Central euope
HOW AUDIENCES USES TECHNOLOGY AND ITS IMPACT IN THEIR LIVES.

HOW AUDIENCES USES TECHNOLOGY AND ITS IMPACT IN THEIR LIVES.
FOR RELEASE APRIL 30, 2018 BY Aaron Smith and .docx

FOR RELEASE APRIL 30, 2018 BY Aaron Smith and .docx
GMX / MAIL.COM INTERNATIONAL DATA SECURITY SURVEY 2021 

GMX / MAIL.COM INTERNATIONAL DATA SECURITY SURVEY 2021
Plus de Ping Identity
Plus de Ping Identity (20)
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

Standard Based API Security, Access Control and AI Based Attack - API Days Pa...
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

Fishing for a CIAM Platform? 11 Question to Ask Before You Buy
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

Webinar: Three Steps to Transform Your Mobile App into a Security Factor
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass
GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance

GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance
Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...

Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...
Dernier
Dernier (20)
A Journey Into the Emotions of Software Developers

A Journey Into the Emotions of Software Developers
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
What's New in Teams Calling, Meetings and Devices March 2024

What's New in Teams Calling, Meetings and Devices March 2024
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
The Role of FIDO in a Cyber Secure Netherlands: FIDO Paris Seminar.pptx

The Role of FIDO in a Cyber Secure Netherlands: FIDO Paris Seminar.pptx
Scale your database traffic with Read & Write split using MySQL Router

Scale your database traffic with Read & Write split using MySQL Router
Digital Identity is Under Attack: FIDO Paris Seminar.pptx

Digital Identity is Under Attack: FIDO Paris Seminar.pptx
Security Concerns Around the World | Infographic
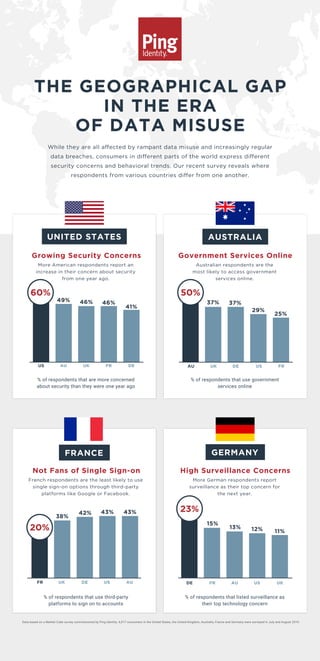
- 1. THE GEOGRAPHICAL GAP IN THE ERA OF DATA MISUSE % of respondents that listed surveillance as their top technology concern Data based on a Market Cube survey commissioned by Ping Identity. 4,017 consumers in the United States, the United Kingdom, Australia, France and Germany were surveyed in July and August 2019. More German respondents report surveillance as their top concern for the next year. High Surveillance Concerns % of respondents that use third-party platforms to sign on to accounts French respondents are the least likely to use single sign-on options through third-party platforms like Google or Facebook. Not Fans of Single Sign-on 15% FRDE AU US UK 13% 12% 11% 23% While they are all affected by rampant data misuse and increasingly regular data breaches, consumers in different parts of the world express different security concerns and behavioral trends. Our recent survey reveals where respondents from various countries differ from one another. GERMANY 38% 42% 43% 43% UKFR DE US AU AUSTRALIA FRANCE UNITED STATES % of respondents that use government services online Australian respondents are the most likely to access government services online. Government Services Online % of respondents that are more concerned about security than they were one year ago More American respondents report an increase in their concern about security from one year ago. Growing Security Concerns 20% 37% 37% 29% 25% UKAU DE US FR 50% 49% AUUS UK FR DE 46% 46% 41% 60%
