Ransomwares variants vying for the top slot
•
0 likes•36 views
WannaCry Ransomware is a game changer at all level in the arena ruled by the likes of Reveton, CryptoLocker, CryptoWall, Locky etc. WannaCry utilized not the encryption capabilities but also exploited vulnerabilities to propagate.
Report
Share
Report
Share
Download to read offline
Recommended
Chris Vargo & Toby HoppSocioeconomic Status, Social Capital, and Partisan Polarity as Predictors of ...

Socioeconomic Status, Social Capital, and Partisan Polarity as Predictors of ...The University of Alabama System
Recommended
Chris Vargo & Toby HoppSocioeconomic Status, Social Capital, and Partisan Polarity as Predictors of ...

Socioeconomic Status, Social Capital, and Partisan Polarity as Predictors of ...The University of Alabama System
Andrea Lelli, Microsoft
My presentation will trace the end-to-end WannaCrypt (also known as WannaCry) attack. I will start with an analysis of the underlying SMBv1 remote code execution kernel-mode exploit dubbed "Eternalblue", a powerful cyberweapon leaked by a hacker group known as "The Shadow Brokers".
I will then describe how the Wannacrypt ransomware works, and show how the cybercriminals leveraged the EternalBlue exploit to spread the ransomware and achieve a massive and unprecedented infection rate, leaving hundreds of thousands of machines affected. I will highlight the Windows 10 kernel mitigations that granted the OS immunity from the attack.
I will also focus on some interesting characteristics that make WannaCrypt particularly sophisticated, like the file-wiping and space-consuming capabilities designed to make the recovery of the original files nearly impossible.
I will conclude with a look into how much the perpetrators might have likely earned from the attack. An analysis of the Bitcoin transactions shows that the cybercriminals pooled around $137 dollars to date, which is a huge amount of money, but doesn’t seem to scale with the extent of infection. Not to mention, Bitcoin is a double-edged sword and there’s a good chance that the cybercriminals may not be able to cash out a dime. In this section I will also mention some copycat malware that tried to spread using the same SMB vulnerability (e.g. NotPetya).
I will end the presentation with advice on preventing, detecting, and responding to ransomware attacks. BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...

BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...BlueHat Security Conference
More Related Content
Similar to Ransomwares variants vying for the top slot
Andrea Lelli, Microsoft
My presentation will trace the end-to-end WannaCrypt (also known as WannaCry) attack. I will start with an analysis of the underlying SMBv1 remote code execution kernel-mode exploit dubbed "Eternalblue", a powerful cyberweapon leaked by a hacker group known as "The Shadow Brokers".
I will then describe how the Wannacrypt ransomware works, and show how the cybercriminals leveraged the EternalBlue exploit to spread the ransomware and achieve a massive and unprecedented infection rate, leaving hundreds of thousands of machines affected. I will highlight the Windows 10 kernel mitigations that granted the OS immunity from the attack.
I will also focus on some interesting characteristics that make WannaCrypt particularly sophisticated, like the file-wiping and space-consuming capabilities designed to make the recovery of the original files nearly impossible.
I will conclude with a look into how much the perpetrators might have likely earned from the attack. An analysis of the Bitcoin transactions shows that the cybercriminals pooled around $137 dollars to date, which is a huge amount of money, but doesn’t seem to scale with the extent of infection. Not to mention, Bitcoin is a double-edged sword and there’s a good chance that the cybercriminals may not be able to cash out a dime. In this section I will also mention some copycat malware that tried to spread using the same SMB vulnerability (e.g. NotPetya).
I will end the presentation with advice on preventing, detecting, and responding to ransomware attacks. BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...

BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...BlueHat Security Conference
Similar to Ransomwares variants vying for the top slot (20)
MLabs - Cyber Crime Tactics and Techniques Q2 2017

MLabs - Cyber Crime Tactics and Techniques Q2 2017
BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...

BlueHat v17 || Wannacrypt + Smbv1.0 Vulnerability = One of the Most Damaging ...
A comprehensive survey ransomware attacks prevention, monitoring and damage c...

A comprehensive survey ransomware attacks prevention, monitoring and damage c...
A Comprehensive Survey: Ransomware Attacks Prevention, Monitoring and Damage ...

A Comprehensive Survey: Ransomware Attacks Prevention, Monitoring and Damage ...
A Comprehensive Survey: Ransomware Attacks Prevention, Monitoring and Damage ...

A Comprehensive Survey: Ransomware Attacks Prevention, Monitoring and Damage ...
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...
OSDC 2014: Michael Renner - Secure encryption in a wiretapped future

OSDC 2014: Michael Renner - Secure encryption in a wiretapped future
OSDC 2014: Michael Renner - Secure encryption in a wiretapped future

OSDC 2014: Michael Renner - Secure encryption in a wiretapped future
Recently uploaded
Recently uploaded (20)
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Ransomwares variants vying for the top slot
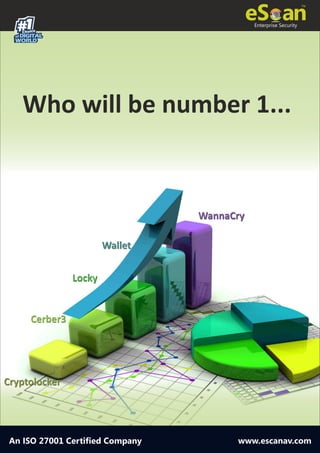
- 1. 1#Choice of DIGITAL WORLD Enterprise Security An ISO 27001 Certified Company www.escanav.com Who will be number 1... WannaCry Wallet Cerber3 Locky CryptolockerCryptolocker Cerber3 Locky Wallet WannaCry
- 2. An ISO 27001 Certified Company RANSOMWARES VARIANTS VYING FOR THE TOP SLOT WannaCry Ransomware is a game changer at all level in the arena ruled by the likes of Reveton, CryptoLocker, CryptoWall, Locky etc. WannaCry utilized not the encryption capabilities but also exploited vulnerabilities to propagate. WannaCry gained prominence due to its worm-like propagation method and due to sheer fact that the Eternal Blue vulnerability used by it was in-fact found in the arsenal of NSA. However, for past week WannaCry wasn’t the only Ransomware which wrecked havoc, Wallet and JAFF have too dominated, although the focus was on WannaCry. Our R&D team, has released the breakdown of the various Ransomwares attacks in past week, added that in the coming few weeks, moreover there would be an increase in such attacks. However we could observe increased activity amongst the various variants and families of different Ransomwares, vying for the top-position.
- 3. An ISO 27001 Certified Company From the available statistics it is apparent that Wallet/Jaff Ransomware commanded 41% of the total Ransomware incidents, while WannaCry was at 11%. There are other families of Ransomware which have continued to maintain their onslaught however; these are intermittent attempts which just add up to the numbers. However, it is to be noted that Ransomware, be it any variant of any family, is the most destructive piece of malware to have ever been created. The future is bleak, due to the fact that the anonymity offered by Crypto- Currencies has been embraced by cyber-criminals and till such time the currency conversion is handled by private / non-government organizations, Crypto-Currencies would gain prominence amongst the criminals and Ransomware would continue to rule the roost. There is stiff competition amongst the various families Ransomwares, as to who is the best and better of all and as we can observe, the fight for the Top Place has already begun. Would it be too early for us to state that Locky Ransomware is steadily loosing its market value in the Underground (Dark-Web) Market Places or shall we wait for the time to prove us correct once again? The cyber-crime ecosystem thrives on: 1. Fame. 2. The depth of the attack. 3. Stability of the infection. 4. Reliability of the Malware. 5. The most important of all, the ability of the authors to provide FUD (Fully Undetectable) at a very fast pace. Cyber Criminals are aware of these facts and in order to increase their revenue and grab their share of spoils are working hard to unleash a new wave of destruction.
