Mobile E-commerce: Friend or Foe
•
0 likes•1,029 views
E
EMCThis infographic highlights key stats and messages from the analyst report from J.Gold Associates that addresses the growing economic impact of mobile cybercrime and fraud.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (15)
Takeaways from 2019's Biggest Information Security Incidents

Takeaways from 2019's Biggest Information Security Incidents
Viewers also liked
Viewers also liked (20)
What Are Your Servers Doing While You’re Sleeping?

What Are Your Servers Doing While You’re Sleeping?
EMC Enterprise Hybrid Cloud 2.5.1, Federation SDDC Edition: Backup Solution G...

EMC Enterprise Hybrid Cloud 2.5.1, Federation SDDC Edition: Backup Solution G...
Similar to Mobile E-commerce: Friend or Foe
Presented at Executive Leaders Network CMO/DPO/CIO/CISO Event on October 06th.
"Last year a staggering 21% of Hornetsecurity Ransomware Attack Survey respondents reported that their organisations fell victim to a ransomware attack. On top of that consider that over 22% of companies reported thinking that Microsoft 365 data cannot be impacted by ransomware attacks, or do not know if it can be impacted. How have things changed since? What is the current state of the ransomware ecosystem today?
Join us as we deep dive into the results of this year's annual ransomware survey and explore the current trends, threats, and news from the industry.
Audience Takeaways
• Current Ransomware Trends
• Ransomware and Microsoft 365
• Protection Techniques
• And More!"Current Ransomware Trends, Ransomware Attack Survey 2022 (Colin Wright at Hor...

Current Ransomware Trends, Ransomware Attack Survey 2022 (Colin Wright at Hor...Executive Leaders Network
Similar to Mobile E-commerce: Friend or Foe (20)
CONSUMER PERCEPTIONS ON SECURITY: DO THEY STILL CARE?

CONSUMER PERCEPTIONS ON SECURITY: DO THEY STILL CARE?
Current Ransomware Trends, Ransomware Attack Survey 2022 (Colin Wright at Hor...

Current Ransomware Trends, Ransomware Attack Survey 2022 (Colin Wright at Hor...
Main Street vs. Wall Street: Who is to Blame for Data Breaches?

Main Street vs. Wall Street: Who is to Blame for Data Breaches?
Updated Cyber Security and Fraud Prevention Tools Tactics

Updated Cyber Security and Fraud Prevention Tools Tactics
Running head HOW TO AVOID INTERNET SCAMS AT THE WORKPLACE 1 .docx

Running head HOW TO AVOID INTERNET SCAMS AT THE WORKPLACE 1 .docx
Accounting for Cyber Risks - How much does Cyber actually cost the Industry?

Accounting for Cyber Risks - How much does Cyber actually cost the Industry?
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear
The Internet of Security Things (A Story about Change) 

The Internet of Security Things (A Story about Change)
2019 06-05-dalakova-kateryna-mkm-mmt-pov-assignment (1)

2019 06-05-dalakova-kateryna-mkm-mmt-pov-assignment (1)
Frauds making fs companies uncompetitive parag deodhar

Frauds making fs companies uncompetitive parag deodhar
More from EMC
More from EMC (20)
INDUSTRY-LEADING TECHNOLOGY FOR LONG TERM RETENTION OF BACKUPS IN THE CLOUD

INDUSTRY-LEADING TECHNOLOGY FOR LONG TERM RETENTION OF BACKUPS IN THE CLOUD
Transforming Desktop Virtualization with Citrix XenDesktop and EMC XtremIO

Transforming Desktop Virtualization with Citrix XenDesktop and EMC XtremIO
EMC FORUM RESEARCH GLOBAL RESULTS - 10,451 RESPONSES ACROSS 33 COUNTRIES 

EMC FORUM RESEARCH GLOBAL RESULTS - 10,451 RESPONSES ACROSS 33 COUNTRIES
The Trust Paradox: Access Management and Trust in an Insecure Age

The Trust Paradox: Access Management and Trust in an Insecure Age
Data Science and Big Data Analytics Book from EMC Education Services

Data Science and Big Data Analytics Book from EMC Education Services
Using EMC Symmetrix Storage in VMware vSphere Environments

Using EMC Symmetrix Storage in VMware vSphere Environments
2014 Cybercrime Roundup: The Year of the POS Breach

2014 Cybercrime Roundup: The Year of the POS Breach
Recently uploaded
Recently uploaded (20)
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Mobile E-commerce: Friend or Foe
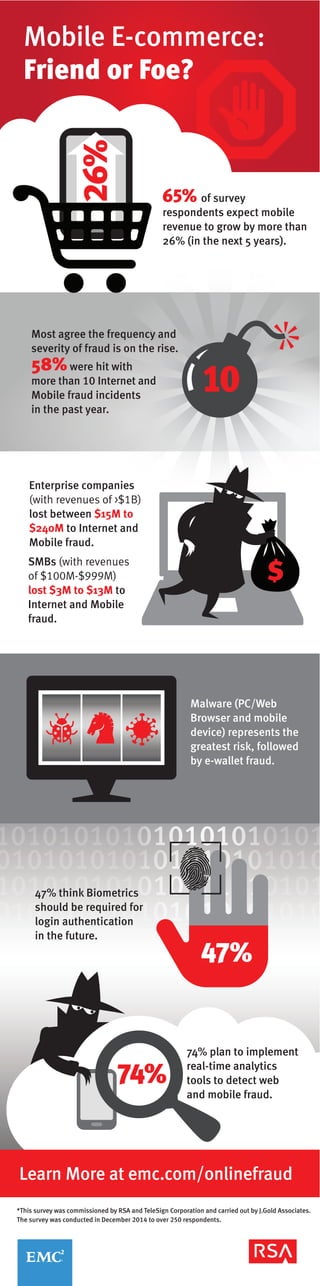
- 1. *This survey was commissioned by RSA and TeleSign Corporation and carried out by J.Gold Associates. The survey was conducted in December 2014 to over 250 respondents. 65% of survey respondents expect mobile revenue to grow by more than 26% (in the next 5 years). Most agree the frequency and severity of fraud is on the rise. 58%were hit with more than 10 Internet and Mobile fraud incidents in the past year. 74% plan to implement real-time analytics tools to detect web and mobile fraud. Malware (PC/Web Browser and mobile device) represents the greatest risk, followed by e-wallet fraud. Mobile E-commerce: Friend or Foe? SMBs (with revenues of $100M-$999M) lost $3M to $13M to Internet and Mobile fraud. Enterprise companies (with revenues of >$1B) lost between $15M to $240M to Internet and Mobile fraud. Learn More at emc.com/onlinefraud 10 26% $ 47% 47% think Biometrics should be required for login authentication in the future. 74%