mimikatz @ phdays
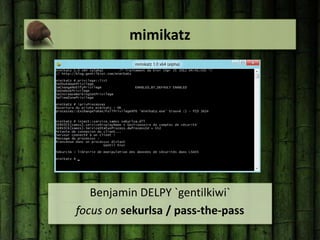
- 1. mimikatz Benjamin DELPY `gentilkiwi` focus on sekurlsa / pass-the-pass
- 2. Who ? Why ? Benjamin DELPY `gentilkiwi` – French – 26y – Kiwi addict – Lazy programmer Started to code mimikatz to : – explain security concepts ; – improve my knowledge ; – prove to Microsoft that sometimes they must change old habits. Why all in French ? – because I’m – It limits script kiddies usage. 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 2
- 3. mimikatz working On XP, 2003, Vista, 2008, Seven, 2008r2, 8, Server 8 – x86 & x64 – partial support for 8 & Server 8 (few kernel driver bugs ;)) – 2000 support dropped with mimikatz 1.0 Everywhere ; it’s statically compiled Two modes – direct action (local commands) – process or driver communication m KeyIso m SamSS « Isolation de clé CNG » « Gestionnaire de comptes de sécurité » i LSASS.EXE i LSASS.EXE m i m i VirtualAllocEx, Direct action : k crypto::patchcng k WriteProcessMemory, a a t t CreateRemoteThread... EventLog sekurlsa.dll z z « Journal d’événements Windows » . SVCHOST.EXE . Open a pipe e e x x Write a welcome message Direct action : e e Wait commands… and return results divers::eventdrop 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 3
- 4. mimikatz architecture all in VC/C++ 2010 with some ASM… mod_mimikatz_standard mod_parseur KiwiCmd.exe mod_mimikatz_winmine mod_text KiwiRegedit.exe mod_mimikatz_divers mod_memory m mod_mimikatz_nogpo mod_secacl mimikatz.sys i KiwiTaskmgr.exe m mod_mimikatz_impersonate mod_pipe i mod_mimikatz_inject mod_inject kappfree.dll k mod_mimikatz_samdump mod_hive a mod_mimikatz_crypto mod_crypto kelloworld.dll t mod_mimikatz_handle mod_patch sam z . mod_mimikatz_privilege mod_privilege klock.dll secrets e mod_mimikatz_system mod_system msv_1_0 x mod_mimikatz_service mod_service tspkg sekurlsa.dll e mod_mimikatz_process mod_process wdigest mod_mimikatz_thread mod_thread livessp mod_mimikatz_terminalserver mod_ts kerberos 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 4
- 5. mimikatz :: sekurlsa what is it ? My favorite library ! A thread that waits, in LSASS, commands from mimikatz (or mubix meterpreter) What sekurlsa can do from the inside ? – Dump system secrets – Dump SAM / DC base – Dump clear text passwords/hashes from interactive sessions • MSV1_0 (dump/inject/delete) • TsPkg • WDigest • LiveSSP • Kerberos Let’s start an injection & pass the hash ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 5
- 6. mimikatz :: sekurlsa history of « pass-the-* » 1/2 Pass-the-hash – 1997 - Unix modified SAMBA client for Hashes usage ; Paul Ashton (EIGEN) – 2000 - Private version of a Windows « LSA Logon Session Editor » ; Hernan Ochoa (CoreSecurity) – 2007 - TechEd @ Microsoft ; Marc Murray (TrueSec) present msvctl, and provide some downloads of it – 2007 - « Pass the hash toolkit » published ; Hernan Ochoa (CoreSecurity) – 2007 - mimikatz 0.1 includes pass the hash and is publicly available for x86 & x64 versions of Windows (yeah, by myself but in French; so not famous ;)) 2007 was the year of pass the hash ! Pass-the-ticket – 04/2011 - wce (pass the hash toolkit evolution) provides Kerberos ticket support; Hernan Ochoa (Ampliasecurity) 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 6
- 7. mimikatz :: sekurlsa history of « pass-the-* » 2/2 Pass-the-pass – 05/2011 – mimikatz 1.0 dumps first clear text passwords from TsPkg provider (but limited to NT 6 and some XP SP3) • http://blog.gentilkiwi.com/securite/pass-the-pass – 05/2011 – return of mimikatz ; it dumps clear text passwords from WDigest provider (unlimited this time ;)) • http://blog.gentilkiwi.com/securite/re-pass-the-pass – 05/2011 – Some organizations opened cases to Microsoft about it… …Lots of time… – begin of 2012 - Lots of blogs (and Kevin Mitnick ;)) say few words about mimikatz – 03/2012 - Hernan Ochoa (Ampliasecurity) publish at seclists that wce support WDigest password extract… • http://seclists.org/pen-test/2012/Mar/7 – 03/2012 – mimikatz strikes again with LiveSSP provider and extracts Live login passwords from Windows 8 memory • http://blog.gentilkiwi.com/securite/rere-pass-the-pass – 03/2012 – yeah, once again…, more curious but Kerberos keeps passwords in memory • http://blog.gentilkiwi.com/securite/rerere-pass-the-pass 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 7
- 8. mimikatz :: sekurlsa let’s take a moment… You noticed ? It has been one year since Microsoft has been notified about passwords extraction from LSASS Without any reaction… – But blacklisting mimikatz from MSE and FEP at 20120228 ;) 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 8
- 9. mimikatz :: sekurlsa :: tspkg because sometimes hash is not enough… 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 9
- 10. mimikatz :: sekurlsa :: tspkg what is it ? Microsoft introduces SSO capability for Terminal Server with NT 6 to improve RemoteApps and RemoteDestkop users’s experience – http://technet.microsoft.com/library/cc772108.aspx Rely on CredSSP with Credentials Delegation (!= Account delegation) – Specs : http://download.microsoft.com/download/9/5/e/95ef66af- 9026-4bb0-a41d-a4f81802d92c/%5Bms-cssp%5D.pdf First impression : it seems cool – User does not have to type its password – Password is not in RDP file – Password is not in user secrets 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 10
- 11. mimikatz :: sekurlsa :: tspkg demo time ! Explanations follow… 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 11
- 12. mimikatz :: sekurlsa :: tspkg questions ? KB says that for it works, we must enable « Default credentials » delegation – “Default credentials : The credentials obtained when the user first logs on to Windows” - https://msdn.microsoft.com/library/bb204773.aspx • What ? Our User/Domain/,Password | Hash | Ticket- ? It seems … – In all cases, system seems to be vulnerable to pass-the-*… In what form ? Our specs : [MS-CSSP] – 2.2.1.2.1 TSPasswordCreds • The TSPasswordCreds structure contains the user's password credentials that are delegated to the server. (or PIN) TSPasswordCreds ::= SEQUENCE { domainName [0] OCTET STRING, userName [1] OCTET STRING, password [2] OCTET STRING } – Challenge / response for authentication ? • Serveur : YES (TLS / Kerberos) • Client : NO ; *password* is sent to server… So password resides somewhere in memory ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 12
- 13. mimikatz :: sekurlsa :: tspkg symbols & theory Let’s explore some symbols ! kd> x tspkg!*clear* 75016d1c tspkg!TSObtainClearCreds = <no type information> kd> x tspkg!*password* 75011b68 tspkg!TSDuplicatePassword = <no type information> 75011cd4 tspkg!TSHidePassword = <no type information> 750195ee tspkg!TSRevealPassword = <no type information> 75012fbd tspkg!TSUpdateCredentialsPassword = <no type information> kd> x tspkg!*locate* 7501158b tspkg!TSCredTableLocateDefaultCreds = <no type information> – sounds cool… (thanks Microsoft) Let’s imagine a scenario – Enumerate all sessions to obtain informations : • Username • Domain • LUID – Call tspkg!TSCredTableLocateDefaultCreds with LUID to obtain : • TS_CREDENTIAL – Call tspkg!TSObtainClearCreds with TS_CREDENTIAL data (TS_PRIMARY_CREDENTIAL) for : • TS_PRIMARY_CREDENTIAL with clear text credentials… 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 13
- 14. mimikatz :: sekurlsa :: tspkg test & data LsaEnumerateLogonSessions for each LUID tspkg!TSCredTableLoca teDefaultCreds tspkg!TSObtainClearCr eds password in clear ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 14
- 15. mimikatz :: sekurlsa :: tspkg test & structures LsaEnumerateLogonSessions lazy way for each LUID tspkg!TSCredTableLoca typedef struct _KIWI_TS_CREDENTIAL { #ifdef _M_X64 teDefaultCreds BYTE unk0[0x88]; #elif defined _M_IX86 BYTE unk0[0x50]; KIWI_TS_CREDEN #endif TIAL PKIWI_TS_PRIMARY_CREDENTIAL pTsPrimary; } KIWI_TS_CREDENTIAL, *PKIWI_TS_CREDENTIAL; KIWI_TS_PRIMAR typedef struct _KIWI_TS_PRIMARY_CREDENTIAL { PVOID unk0; Y_CREDENTIAL LSA_UNICODE_STRING Domaine; LSA_UNICODE_STRING UserName; LSA_UNICODE_STRING Password; tspkg!TSObtainClearCr } KIWI_TS_PRIMARY_CREDENTIAL, *PKIWI_TS_PRIMARY_CREDENTIAL; eds KIWI_TS_PRIMAR Y_CREDENTIAL password in clear ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 15
- 16. mimikatz :: sekurlsa :: tspkg first result It worked ! Since old Windows’s version I hadn’t seen my Windows password – I’ve been a little bit afraid After many hesitations, I published a post and a stable tool update on my blog at 20110508 – http://blog.gentilkiwi.com/securite/pass-the-pass But some issues : – & tspkg!TSObtainClearCreds are not exported tspkg!TSCredTableLocateDefaultCreds – tspkg!TSObtainClearCreds not always present… – Calling conventions can be a problem – Only NT6 and few XP SP3 (manual provider activation) 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 16
- 17. mimikatz :: sekurlsa :: tspkg final implementation typedef struct _KIWI_TS_CREDENTIAL_AVL_SEARCH { LsaEnumerateLogonSessions #ifdef _M_X64 BYTE unk0[108]; #elif defined _M_IX86 BYTE unk0[64]; #endif for each LUID LUID LocallyUniqueIdentifier; #ifdef _M_X64 BYTE unk1[46]; #elif defined _M_IX86 tspkg!TSGlobal KIWI_TS_CREDENTI BYTE unk1[16]; CredTable AL_AVL_SEARCH #endif } KIWI_TS_CREDENTIAL_AVL_SEARCH, *PKIWI_TS_CREDENTIAL_AVL_SEARCH; RtlLookupElementGenericTabl typedef struct _KIWI_TS_CREDENTIAL { eAvl #ifdef _M_X64 BYTE unk0[0x88]; #elif defined _M_IX86 KIWI_TS_CREDEN BYTE unk0[0x50]; TIAL #endif KIWI_TS_PRIMAR PKIWI_TS_PRIMARY_CREDENTIAL pTsPrimary; Y_CREDENTIAL } KIWI_TS_CREDENTIAL, *PKIWI_TS_CREDENTIAL; typedef struct _KIWI_TS_PRIMARY_CREDENTIAL { LsaUnprotectMemory PVOID unk0; LSA_UNICODE_STRING Domaine; LSA_UNICODE_STRING UserName; password LSA_UNICODE_STRING Password; } KIWI_TS_PRIMARY_CREDENTIAL, in clear ! *PKIWI_TS_PRIMARY_CREDENTIAL; 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 17
- 18. mimikatz :: sekurlsa :: tspkg demo time ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 18
- 19. mimikatz :: sekurlsa :: tspkg final result It works better ;) – No orphan referenced credentials – More logic approach (We will see that latter…) We have just to find : – tspkg!TSGlobalCredTable – SeckPkgFunctionTable->LsaUnprotectMemory • LSA_SECPKG_FUNCTION_TABLE : http://msdn.microsoft.com/library/windows/desktop/aa378510.aspx • LsaUnprotectMemory : http://msdn.microsoft.com/library/windows/desktop/ff714510.aspx Find this… We all have personal convictions to search unexported data : – Hardcoded addresses / offsets ( ) ; – Disassembly engine ; – Pattern matching ; – … 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 19
- 20. mimikatz :: sekurlsa :: wdigest because clear text password over http/https is not cool 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 20
- 21. mimikatz :: sekurlsa :: wdigest what is it ? “Digest access authentication is one of the agreed-upon methods a web server can use to negotiate credentials with a user's web browser. It applies a hash function to a password before sending it over the network *…+” Wikipedia : http://en.wikipedia.org/wiki/Digest_access_authentication “Common Digest Authentication Scenarios : – Authenticated client access to a Web site – Authenticated client access using SASL – Authenticated client access with integrity protection to a directory service using LDAP” Microsoft : http://technet.microsoft.com/library/cc778868.aspx Again, it seems cool – No password over the network, just hashes – No reversible password in Active Directory ; hashes for each realm • Only with Advanced Digest authentication 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 21
- 22. mimikatz :: sekurlsa :: wdigest what is it ? We speak about hashes, but what hashes ? H = MD5(HA1:nonce:[…]:HA2) • HA1 = MD5(username:realm:password) • HA2 = MD5(method:digestURI:[…]) Even after login, HA1 may change… realm is from server side and cannot be determined before Windows logon WDigest provider must have elements to compute responses for different servers : – Username – Realm (from server) – Password 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 22
- 23. mimikatz :: sekurlsa :: wdigest theory This time, we know : – that WDigest keeps password in memory « by protocol » for HA1 digest – that LSASS love to unprotect password with LsaUnprotectMemory (so protect with LsaProtectMemory) LsaUnprotectMemory – At offset 0xb4 of LSA_SECPKG_FUNCTION_TABLE – Let’s perform a research in WDigest : .text:7409D151 _DigestCalcHA1@8 call dword ptr [eax+0B4h] – Hypothesis seems verified LsaProtectMemory – At offset 0xb0 of LSA_SECPKG_FUNCTION_TABLE – Let’s perform a research in WDigest : .text:74096C69 _SpAcceptCredentials@16 call dword ptr [eax+0B0h] – SpAcceptCredentials takes clear password in args • Protect it with LsaProtectMemory • Update or insert data in double linked list : wdigest!l_LogSessList 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 23
- 24. mimikatz :: sekurlsa :: wdigest test & data LsaEnumerateLogonSessions for each LUID wdigest!l_LogS essList search linked list for LUID LsaUnprotectMemory password in clear ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 24
- 25. mimikatz :: sekurlsa :: wdigest final implementation LsaEnumerateLogonSessions for each LUID typedef struct _KIWI_WDIGEST_LIST_ENTRY { struct _KIWI_WDIGEST_LIST_ENTRY *Flink; wdigest!l_LogS struct _KIWI_WDIGEST_LIST_ENTRY *Blink; DWORD UsageCount; essList struct _KIWI_WDIGEST_LIST_ENTRY *This; LUID LocallyUniqueIdentifier; […] LSA_UNICODE_STRING UserName; search linked list for LUID LSA_UNICODE_STRING Domaine; LSA_UNICODE_STRING Password; […] } KIWI_WDIGEST_LIST_ENTRY, *PKIWI_WDIGEST_LIST_ENTRY KIWI_WDIGEST_L ; IST_ENTRY LsaUnprotectMemory password in clear ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 25
- 26. mimikatz :: sekurlsa :: wdigest demo time ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 26
- 27. mimikatz :: sekurlsa :: wdigest result It works again ! This time we just have to find : – wdigest!l_LogSessList – SeckPkgFunctionTable->LsaUnprotectMemory • LSA_SECPKG_FUNCTION_TABLE : http://msdn.microsoft.com/library/windows/desktop/aa378510.aspx • LsaUnprotectMemory : http://msdn.microsoft.com/library/windows/desktop/ff714510.aspx Seems generalizable ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 27
- 28. mimikatz :: sekurlsa and now what ? In fact, with TsPkg and WDigest, passwords can be retrieved from any version of Windows ... – WDigest • XP, 2003 • Vista / Seven / 2008 / 2008r2 • 8 But not with a Live account – TsPkg • XP SP3 (manual install) • Vista / Seven / 2008 / 2008r2 • 8 Even with a Live account 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 28
- 29. mimikatz :: sekurlsa and now what ? wce had not copied my TsPkg functionalities Only WDigest, so they missed 8 Live accounts… – Kiwi WDigest patterns (last public release) #ifdef _M_X64 BYTE ptrInsertInLogSess[] = {0x4C, 0x89, 0x1B, 0x48, 0x89, 0x43, 0x08, 0x49, 0x89, 0x5B, 0x08, 0x48, 0x8D}; #elif defined _M_IX86 BYTE ptrInsertInLogSess[] = {0x8B, 0x45, 0x08, 0x89, 0x08, 0xC7, 0x40, 0x04}; #endif – wce patterns Between ~17 occurrences of wdigest!l_LogSessList, maybe a coincidence… for lack of TsPkg, they can be inspired by next releases ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 29
- 30. mimikatz :: sekurlsa :: livessp because Microsoft was too good in closed networks 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 30
- 31. mimikatz :: sekurlsa :: livessp how ? Actually I’ve only used logical (empirical) approach to search passwords… : – Protocol reading – Symbols searching ~ Boring ~… be more brutal this time : make a WinDBG trap ! 0: kd> !process 0 0 lsass.exe PROCESS 83569040 SessionId: 0 Cid: 0224 Peb: 7f43f000 ParentCid: 01b4 DirBase: 5df58100 ObjectTable: 80ce4740 HandleCount: <Data Not Accessible> Image: lsass.exe 0: kd> .process /i 83569040 You need to continue execution (press 'g' <enter>) for the context to be switched. When the debugger breaks in again, you will be in the new process context. 0: kd> g Break instruction exception - code 80000003 (first chance) nt!RtlpBreakWithStatusInstruction: 814b39d0 cc int 3 0: kd> .reload /user Loading User Symbols ............................................................ 0: kd> bp /p @$proc lsasrv!LsaProtectMemory "kc 5 ; g" 0: kd> g 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 31
- 32. mimikatz :: sekurlsa :: livessp how ? Let’s login with a Live account on Windows 8 ! lsasrv!LsaProtectMemory livessp!LiveMakeSupplementalCred livessp!LiveMakeSecPkgCredentials Our LiveSSP provider livessp!LsaApLogonUserEx2 livessp!SpiLogonUserEx2 lsasrv!LsaProtectMemory msv1_0!NlpAddPrimaryCredential Yeah, Pass the Hash capability with Live msv1_0!SspAcceptCredentials msv1_0!SpAcceptCredentials account too… lsasrv!LsaProtectMemory tspkg!TSHidePassword Live user can logon through RDP via SSO tspkg!SpAcceptCredentials 1: kd> uf /c livessp!LsaApLogonUserEx2 livessp!LsaApLogonUserEx2 (74781536) [...] livessp!LsaApLogonUserEx2+0x560 (74781a96): call to livessp!LiveCreateLogonSession (74784867) After credentials protection, LsaApLogonUserEx2 calls LiveCreateLogonSession to insert data in LiveGlobalLogonSessionList (similar to WDigest) 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 32
- 33. mimikatz :: sekurlsa :: livessp final implementation typedef struct _KIWI_LIVESSP_LIST_ENTRY { LsaEnumerateLogonSessions struct _KIWI_LIVESSP_LIST_ENTRY *Flink; struct _KIWI_LIVESSP_LIST_ENTRY *Blink; PVOID unk0; PVOID unk1; PVOID unk2; for each LUID PVOID unk3; DWORD unk4; DWORD unk5; PVOID unk6; livessp!LiveGloba LUID LocallyUniqueIdentifier; lLogonSessionList LSA_UNICODE_STRING UserName; PVOID unk7; PKIWI_LIVESSP_PRIMARY_CREDENTIAL suppCreds; } KIWI_LIVESSP_LIST_ENTRY, search linked list for LUID *PKIWI_LIVESSP_LIST_ENTRY; KIWI_LIVESSP_LIS T_ENTRY typedef struct _KIWI_LIVESSP_PRIMARY_CREDENTIAL { KIWI_LIVESSP_PRI DWORD isSupp; MARY_CREDENTIAL DWORD unk0; LSA_UNICODE_STRING UserName; LSA_UNICODE_STRING Domaine; LSA_UNICODE_STRING Password; LsaUnprotectMemory } KIWI_LIVESSP_PRIMARY_CREDENTIAL, *PKIWI_LIVESSP_PRIMARY_CREDENTIAL; password in clear ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 33
- 34. mimikatz :: sekurlsa :: livessp demo time ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 34
- 35. mimikatz :: sekurlsa it was a cool trap no ? Even if we already have tools for normal accounts, are you not curious to test one with this trap ?* * Me, yes 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 35
- 36. mimikatz :: sekurlsa :: kerberos Let’s login normal account lsasrv!LsaProtectMemory kerberos!KerbHideKey kerberos!KerbCreatePrimaryCredentials kerberos!KerbCreateLogonSession Kerberos, ticket part ? Maybe ;) kerberos!SpAcceptCredentials lsasrv!LsaProtectMemory kerberos!KerbHidePassword kerberos!KerbCreateLogonSession Kerberos part for password ?????? kerberos!SpAcceptCredentials lsasrv!LsaProtectMemory msv1_0!NlpAddPrimaryCredential msv1_0!SspAcceptCredentials msv1_0!SpAcceptCredentials lsasrv!LsaProtectMemory wdigest!SpAcceptCredentials lsasrv!LsaProtectMemory tspkg!TSHidePassword tspkg!SpAcceptCredentials After credentials protection, KerbCreateLogonSession calls : – NT6 ; KerbInsertOrLocateLogonSession to insert data in KerbGlobalLogonSessionTable – NT5 ; KerbInsertLogonSession to insert data in KerbLogonSessionList 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 36
- 37. mimikatz :: sekurlsa :: kerberos (nt 6) final implementation typedef struct _KIWI_KERBEROS_LOGON_AVL_SEARCH { LsaEnumerateLogonSessions #ifdef _M_X64 BYTE unk0[64]; #elif defined _M_IX86 BYTE unk0[36]; #endif for each LUID LUID LocallyUniqueIdentifier; } KIWI_KERBEROS_LOGON_AVL_SEARCH, *PKIWI_KERBEROS_LOGON_AVL_SEARCH; Kerberos!KerbG KIWI_KERBEROS_LO lobalLogonSess GON_AVL_SEARCH ionTable typedef struct _KIWI_KERBEROS_PRIMARY_CREDENTIAL { DWORD unk0; PVOID unk1; PVOID unk2; RtlLookupElementGenericTabl #ifdef _M_X64 eAvl BYTE unk3[96]; #elif defined _M_IX86 BYTE unk3[68]; #endif LSA_UNICODE_STRING UserName; KIWI_KERBEROS_PR LSA_UNICODE_STRING Domaine; IMARY_CREDENTIAL LSA_UNICODE_STRING Password; } KIWI_KERBEROS_PRIMARY_CREDENTIAL, *PKIWI_KERBEROS_PRIMARY_CREDENTIAL; LsaUnprotectMemory password in clear ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 37
- 38. mimikatz :: sekurlsa :: kerberos (nt 5) final implementation typedef struct _KIWI_KERBEROS_LOGON_SESSION { LsaEnumerateLogonSessions struct _KIWI_KERBEROS_LOGON_SESSION *Flink; struct _KIWI_KERBEROS_LOGON_SESSION *Blink; DWORD UsageCount; PVOID unk0; PVOID unk1; for each LUID PVOID unk2; DWORD unk3; DWORD unk4; PVOID unk5; kerberos!KerbLog PVOID unk6; onSessionList PVOID unk7; LUID LocallyUniqueIdentifier; #ifdef _M_IX86 DWORD unk8; search linked list for LUID #endif DWORD unk9; DWORD unk10; PVOID unk11; DWORD unk12; DWORD unk13; KIWI_LIVESSP_PRI PVOID unk14; MARY_CREDENTIAL PVOID unk15; PVOID unk16; […] LSA_UNICODE_STRING UserName; LSA_UNICODE_STRING Domaine; LsaUnprotectMemory LSA_UNICODE_STRING Password; } KIWI_KERBEROS_LOGON_SESSION, *PKIWI_KERBEROS_LOGON_SESSION; password in clear ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 38
- 39. mimikatz :: sekurlsa :: kerberos demo time ! 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 39
- 40. mimikatz :: sekurlsa :: kerberos « hu ? » Ok It works…* But why ? *Not at all logon on NT5 *Can need an unlock… From my understanding of Microsoft explanations, no need of passwords for the Kerberos protocol… all is based on the hash (not very sexy too) 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 40
- 41. mimikatz :: sekurlsa :: kerberos BONUS « hu ? » Microsoft’s implementation of Kerberos is full of logical… For password auth : – password hash for shared secret, but keeping password in memory For full smartcard auth : – No password on client – No hash on client ? • NTLM hash on client… • KDC sent it back as a gift 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 41
- 42. mimikatz :: sekurlsa why this is dangerous ? Not a bug Not a weakness Not a vulnerability Not a 0-day – (for now, there may be too) It’s “normal” that LSASS keeps passwords in memory for passwords based providers when protocols need them – And hashes for msv1_0… All of these rely on shared secrets… So you can’t prevent Windows internal behaviors… (in a supported way) One change from Microsoft on protocols can impact all versions I don’t count on a fix or others things in the next [5;10] years… 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 42
- 43. mimikatz :: sekurlsa what we can do ? Basics – No physical access to computer (first step to pass the hash) – No admin rights / system rights / debug privileges (…) – Disable local admin accounts – Strong passwords (haha, it was a joke) – Network login instead of interactive (when possible) – Audit ; pass the hash keeps traces and can lock accounts – No admin rights / system rights / debug privileges, even VIP More in depth – Force strong authentication (SmartCard & Token) : $ / € – Short validity for Kerberos tickets – No delegation – Disable NTLM (available with NT6) – No exotic : • biometrics (it keeps password somewhere and push it to Windows) • single sign on – Stop shared secrets for authentication : push Public / Private stuff (like keys ;)) – Let opportunities to stop retrocompatibility – Disable faulty providers ? • Is it supported by Microsoft ? • Even if, you will disable Kerberos and msv1_0 ? 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 43
- 44. mimikatz :: sekurlsa Code it ! Implement it in Meta ! Discover ! Pass the hash : Package Symbols Description msv1_0 SeckPkgFunctionTable->GetCredentials Get clear LM & NTLM hashes from LUID SeckPkgFunctionTable->LsaUnprotectMemory msv1_0 SeckPkgFunctionTable->LsaProtectMemory Push clear LM & NTLM hashes to LUID SeckPkgFunctionTable->AddCredential msv1_0 SeckPkgFunctionTable->DeleteCredential Delete hashes from LUID Get passwords : Package Symbols Type tspkg tspkg!TSGlobalCredTable RTL_AVL_TABLE SeckPkgFunctionTable->LsaUnprotectMemory wdigest wdigest!l_LogSessList LIST_ENTRY SeckPkgFunctionTable->LsaUnprotectMemory livessp livessp!LiveGlobalLogonSessionList LIST_ENTRY SeckPkgFunctionTable->LsaUnprotectMemory kerberos kerberos!KerbLogonSessionList LIST_ENTRY (nt5) SeckPkgFunctionTable->LsaUnprotectMemory kerberos Kerberos!KerbGlobalLogonSessionTable RTL_AVL_TABLE (nt6) SeckPkgFunctionTable->LsaUnprotectMemory 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 44
- 45. mimikatz :: sekurlsa little help to start ! Package Datas Little help * @getLogonPasswords Use « full » keyword in argument of functions msv1_0 @getMSV @getMSVFunctions msv1_0 : ** lsasrv.dll ** ; Statut recherche : OK :) – 3 * Utilisateur : termuser @GetCredentials = 000007F9C1C62938 * Domaine : DEMO @AddCredential = 000007F9C1C71010 * Hash LM : d0e9aee149655a6075e4540af1f22d3b @DeleteCredential = 000007F9C1C61F58 * Hash NTLM : cc36cf7a8514893efccd332446158b1a @LsaUnprotectMemory = 000007F9C1C59960 @LsaProtectMemory = 000007F9C1C628A4 tspkg @getTsPkg @getTsPkgFunctions tspkg : ** tspkg.dll/lsasrv.dll ** ; Statut recherche : OK :) * Utilisateur : termuser @TSGlobalCredTable = 000007F9C1557B20 * Domaine : DEMO @LsaUnprotectMemory = 000007F9C1C59960 * Mot de passe : waza1234/ wdigest @getWDigest @getWDigestFunctions wdigest : ** wdigest.dll/lsasrv.dll ** ; Statut recherche : OK :) * Utilisateur : termuser @l_LogSessList = 000007F9C15E12B0 * Domaine : DEMO @LsaUnprotectMemory = 000007F9C1C59960 * Mot de passe : waza1234/ livessp @getLiveSSP @getLiveSSPFunctions livessp : ** livessp.dll/lsasrv.dll ** ; Statut recherche : OK :) * Utilisateur : sekurlsa@live.fr @LiveGlobalLogonSessionList = 000007F9C14E8C68 * Domaine : ps:password @LsaUnprotectMemory = 000007F9C1C59960 * Mot de passe : waza1234/ kerberos @getKerberos @getKerberosFunctions kerberos : ** kerberos.dll/lsasrv.dll ** ; Statut recherche : OK :) * Utilisateur : termuser @KerbGlobalLogonSessionTable = 000007F9C1955AE0 * Domaine : DEMO.LOCAL @KerbLogonSessionList = 0000000000000000 * Mot de passe : waza1234/ @LsaUnprotectMemory = 000007F9C1C59960 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 45
- 46. mimikatz :: sekurlsa some ideas Meterpreter post module Standalone binary without injection yeah, it’s easy ! – read all data (sessions, encrypted passwords) – read all keys and implement your own (un)protectMemory routine ! – decrypt / crypt Extract all of this from memory dump / hyberfile ! etc… Make demonstrations to your chief information security officer Ask Microsoft to work on better implementation – Maybe offer possibilities to disable or not some functionalities – Think globally about data really needed for authentication 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 46
- 47. mimikatz :: sekurlsa some ideas Meterpreter post module Standalone binary without injection yeah, it’s easy ! – read all data (sessions, encrypted passwords) – read all keys and implement your own (un)protectMemory routine ! – decrypt / crypt Extract all of this from memory dump / hyberfile ! etc… Make demonstrations to your chief information security officer Ask Microsoft to work on better implementation – Maybe offer possibilities to disable or not some functionalities – Think globally about data really needed for authentication 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 47
- 48. mimikatz what else ? Crypto mod_mimikatz_crypto mod_crypto – Export non-exportable certificates and keys • CryptoAPI • CNG… Stop event monitoring mod_mimikatz_divers Basic GPO bypass mod_mimikatz_nogpo Applocker / SRP bypass kappfree.dll Driver mimikatz.sys – Play with tokens & privileges – Display SSDT x86 & x64 – List minifilters actions – List Notifications (process / thread / image / registry) – List Objects hooks and procedures – … … 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 48
- 49. mimikatz that’s all folks ! Thanks’ to / Спасибо : – my girlfriend for her support (her LSASS crashed few times) – Positive Technologies to offer me this great opportunity – Microsoft to consider it as normal/acceptable – Security friends/community for their ideas & challenges – You, for your attention ! Questions ? Don’t be shy ;) especially if you have written the corresponding slide number 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 49
- 50. mimikatz source code Not now available – I’m not proud of mixing C/C++ and STL in LSASS – Script kiddies will use it without understanding But a little part of it for “pass the pass” available – So download it on mimikatz download page • http://blog.gentilkiwi.com/mimikatz 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 50
- 51. Blog & Contact blog/mimikatz : http://blog.gentilkiwi.com/mimikatz email : benjamin@gentilkiwi.com Twitter : @gentilkiwi 6/3/2012 Benjamin DELPY `gentilkiwi` @ PHDays 2012 - benjamin@gentilkiwi.com ; blog.gentilkiwi.com 51
