Report
Share
More Related Content
What's hot
Viewers also liked
Similar to Ch09 2
Similar to Ch09 2 (20)
Error Detection and Correction in Data Communication DC18

Error Detection and Correction in Data Communication DC18
More from Idris Usmani
Recently uploaded
Recently uploaded (20)
Event-Driven Architecture Masterclass: Challenges in Stream Processing

Event-Driven Architecture Masterclass: Challenges in Stream Processing
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...

Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...
Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...

Choosing the Right FDO Deployment Model for Your Application _ Geoffrey at In...
“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf

“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf
How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf

How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf
Introduction to FIDO Authentication and Passkeys.pptx

Introduction to FIDO Authentication and Passkeys.pptx
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
Using IESVE for Room Loads Analysis - UK & Ireland

Using IESVE for Room Loads Analysis - UK & Ireland
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...

Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...
Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...

Human Expert Website Manual WCAG 2.0 2.1 2.2 Audit - Digital Accessibility Au...
Ch09 2
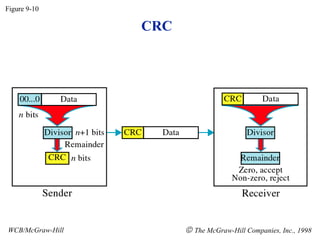
- 1. CRC Figure 9-10 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 2. Binary Division Figure 9-11 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 3. Polynomial Figure 9-12 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 4. Figure 9-13 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Polynomial and Divisor
- 5. Standard Polynomials Figure 9-14 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 6. Checksum Figure 9-15 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 7. Figure 9-16 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Data Unit and Checksum
- 8. Error Correction Figure 9-17 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 9. Hamming Code Figure 9-18 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 10. Figure 9-19 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 11. Figure 9-19-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 12. Figure 9-20 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Example of Hamming Code
- 13. Single-bit error Figure 9-21 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 14. Figure 9-22 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Error Detection
