what is OSI model
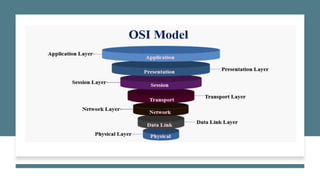
- 3. What is OSI Model? The Open Systems Interconnection model (OSI model) is a conceptual model that 'provides a common basis for the coordination of [ISO] standards development for the purpose of systems interconnection'.[2] In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
- 4. What is OSI Model? The model partitions the flow of data in a communication system into seven abstraction layers to describe networked communication from the physical implementation of transmitting bits across a communications medium to the highest- level representation of data of a distributed application. Each intermediate layer serves a class of functionality to the layer above it and is served by the layer below it. Classes of functionality are realized in all software development through all and any standardized communication protocols.
- 5. •Layer 1 defines devices’ electrical and physical aspects, for example, cables, connectors, electrical signals, pinouts, etc. It provides the physical interface between a device and the transmission media. •Layer 2 – The data link layer provides the transmission protocol that controls the data flow between network devices, for example, a network switch. Data packets are encoded and decoded into bits, flow control, and error checks in layer 1. This layer has two sub-layers, Media Access Control (MAC) and the Logical Link Control (LLC) layer. •communication are functions of the application layer.
- 6. •Layer 3 provides routing and switching technologies that route variable length data packets from the source to the destination network. It creates logical routes (Virtual Circuits) which transmit the data from one network to another. Layer 3 includes packets, IP, ICMP, IPSec, and IGMP. •Layer 4 ensures complete data transfer is error-free, in sequence, and with no losses or duplications, for example, TCP and UDP. The transport layer controls a link’s reliability through flow control, segmentation and desegmentation, and error control. Providing the transfer of data between end-users.
- 7. •Layer 5 of the OSI model handles the management, establishment, and termination of connections between two end-users of a network. Communication sessions consist of requests and responses that occur between applications. •Layer 6 translates data for the application layer for the network. Encryption and authentication, for example, SSL and TLS, and data compression are processed in the presentation layer. •Layer 7 is the layer that handles the end-user direct interaction with the application, for example, SSH, HTTP, and DNS. Resource evaluation, synchronization, and communication are functions of the application layer.
- 8. OSI Model Explained Each layer in the OSI model has its own well-defined functions, and the functions of each layer communicate and interact with the layers immediately above and below it, unless the layer does not have layers below or above. The Internet protocol suite has a separate model, the layers of which are mentioned in RFC 1122 and RFC 1123. That model combines the physical and data link layers of the OSI model into a single link layer, and has a single application layer for all protocols above the transport layer, as opposed to the separate application, presentation and session layers of the OSI model.
- 9. Advantage of OSI Model •It helps you to standardize router, switch, motherboard, and other hardware •Reduces complexity and standardizes interfaces •Facilitates modular engineering •Helps you to ensure interoperable technology •Helps you to accelerate the evolution •Protocols can be replaced by new protocols when technology changes. •Provide support for connection-oriented services as well as connectionless service. •It is a standard model in computer networking. •Supports connectionless and connection-oriented services. •Offers flexibility to adapt to various types of protocols
- 11. OSI Layers •The upper layer of the OSI model mainly deals with the application related issues, and they are implemented only in the software. The application layer is closest to the end user. Both the end user and the application layer interact with the software applications. An upper layer refers to the layer just above another layer. •The lower layer of the OSI model deals with the data transport issues. The data link layer and the physical layer are implemented in hardware and software. The physical layer is the lowest layer of the OSI model and is closest to the physical medium. The physical layer is mainly responsible for placing the information on the physical medium.
- 12. OSI Model TCP/IP model OSI model provides a clear distinction between interfaces, services, and protocols. TCP/IP doesn’t offer any clear distinguishing points between services, interfaces, and protocols. OSI uses the network layer to define routing standards and protocols. TCP/IP uses only the Internet layer. OSI model use two separate layers physical and data link to define the functionality of the bottom layers TCP/IP uses only one layer (link). OSI model, the transport layer is only connection-oriented. A layer of the TCP/IP model is both connection- oriented and connectionless. In OSI model, data link layer and physical are separate layers. In TCP data link layer and physical layer are combined as a single host-to-network layer. The minimum size of the OSI header is 5 bytes. Minimum header size is 20 bytes.
- 14. Layer Name Protocols Layer 7 Application SMTP, HTTP, FTP, POP3, SNMP Layer 6 Presentation MPEG, ASCH, SSL, TLS Layer 5 Session NetBIOS, SAP Layer 4 Transport TCP, UDP Layer 3 Network IPV5, IPV6, ICMP, IPSEC, ARP, MPLS. Layer 2 Data Link RAPA, PPP, Frame Relay, ATM, Fiber Cable, etc. Layer 1 Physical RS232, 100BaseTX, ISDN, 11. Protocols supported at various levels
- 15. THANK YOU Like the Video and Subscribe the Channel
