An introduction to finance
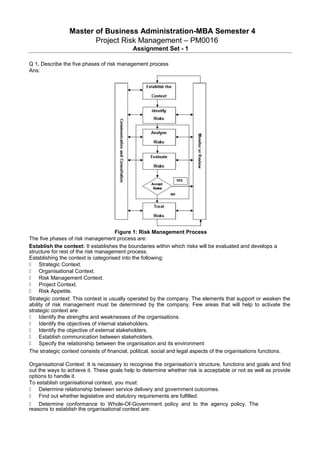
- 1. Master of Business Administration-MBA Semester 4 Project Risk Management – PM0016 Assignment Set - 1 Q 1. Describe the five phases of risk management process Ans: Figure 1: Risk Management Process The five phases of risk management process are: Establish the context: It establishes the boundaries within which risks will be evaluated and develops a structure for rest of the risk management process. Establishing the context is categorised into the following: Strategic Context. Organisational Context. Risk Management Context. Project Context. Risk Appetite. Strategic context: This context is usually operated by the company. The elements that support or weaken the ability of risk management must be determined by the company. Few areas that will help to activate the strategic context are: Identify the strengths and weaknesses of the organisations. Identify the objectives of internal stakeholders. Identify the objective of external stakeholders. Establish communication between stakeholders. Specify the relationship between the organisation and its environment The strategic context consists of financial, political, social and legal aspects of the organisations functions. Organisational Context: It is necessary to recognise the organisation’s structure, functions and goals and find out the ways to achieve it. These goals help to determine whether risk is acceptable or not as well as provide options to handle it. To establish organisational context, you must: Determine relationship between service delivery and government outcomes. Find out whether legislative and statutory requirements are fulfilled. Determine conformance to Whole-Of-Government policy and to the agency policy. The reasons to establish the organisational context are:
- 2. Risk management occurs within the structure of company’s objectives, goals and strategies. Manage the set of risks which is due to failure to accomplish certain target or specific activity. The company policy helps in determining criteria, which in turn help you to decide whether a risk is tolerable or not. This also forms an option for treatment of risk. Risk management context: The activity to be examined is defined in this context. The objectives, scope and boundaries involved is also included in it. The risk management process establishes boundaries of activity which involves: Defining parameters and scope of project risk. Defining project risk extent in terms of time and location. Identifying the need for any studies or resources. Identifying the need for risk budget to balance costs and benefits. Determining any issues related to special roles and responsibilities or any risk project dependences. The analysis in risk management context is done on the basis of type of risk and the information that need to be communicated and the methods of communication. Analysis required can be determined by the combination of the following: Level of complication in the activity. Interaction with stakeholders to convey required information. Type of project risks. Activities which are important to achieve project goal. Project context: The business need of the proposed project must be clearly outlined. To understand the project context the below mentioned areas must be evaluated, that are: Relationship between risk project and government outcomes. Relationship between risk project and company output. Changes in business process, management teams and any other related procedures. Risk appetite: Before taking any actions that you find necessary to handle the risk, you must first determine the amount of risk the company will be ready to tolerate. The risk that is considered as tolerable depends on the perceived significance of particular risks. For example, the tolerable financial loss in an organisation depends on a range of features which include budget, source of loss and other risks related to poor publicity or image issues. This particular risk can cause number of effects. An effect of financial loss may tolerable, however, the associated effect that is related to harm to health or damage to safety may not be tolerable. Identify risks: After establishing the context the next step is to identify the possible risks. This step helps you to identify the sources of risk in an organised way. There are two levels to risk identification process, which include: Risk Stage Risk Register Risk stages: To undertake a project, there are several stages. For example, stages for an asset will include: Validate extra sites Identify extra assets Approval to dispose assets Register sites in Government Land Register (GLR) Find out methods of disposal Contract and negotiation Maintenance and settlement. Risk register: Records all the risks present in each project. These risks can be due to natural disaster, political issues, commercial and legal issues, technical issues or issues raised due to economic circumstances. Experts’ knowledge helps to easily identify risks in a project. The primary goal of risk identification is to have a detailed list of risks that affects the organisations objectives. Analyse risks: Risk analysis helps to distinguish minor risks from the major risks. It also helps in evaluation and treatment of risks. Analysing risks involves finding out sources of risks, possibility of risks and the outcomes. The probability and effects of the risk are combined to produce a level of risk. Statistical analysis and calculations are use to find out the probability and effects of the risk. If no past record is available to determine the possible outcomes, then an estimate is made about a particular event and its outcome. There are three types of risk analysis, they are:
- 3. Qualitative analysis: Use descriptive scales to draw a level of possible effects of risks. The scale can also be adjusted to the extent most suitable to the circumstances. Semi-quantitative analysis: It provides more detailed prioritisation of the risks that is obtained in qualitative analysis. Quantitative analysis: Using information from a variety of sources, the effects and probability of risk is represented using numeric value. Below are some ways, which you can use for risk identification: Based on objective: The event which prevents you from achieving an objective completely or partially is identified as risk and every project and organisations have these objectives. Based on scenario: The scenarios are usually the ways to achieve an objective or to analyse the interaction of forces. Any scenario that activates an undesired event is identified as risk. Based on taxonomy: This risk identification is done by breaking down all possible sources of risk. Based on common-risk checking: Many industries list out their known risks and share them. Each and every risk in the list can be evaluated for an application to suite a specific situation. Based on risk charting: This risk identification is done by listing resources at risks and combining the above approaches. In this method of identification you can start with threat and identify the resource that will be affected or you can examine the consequences and then determine the combination of threat and resource. Evaluate risks: Risk evaluation can be done by comparing approximate level of risks against pre-established criteria. Once the level of risks is estimated then you can decide whether or not these risks require treatment. The risks with low priority can be monitored regularly without any treatment. However, high priority risks must be dealt immediately. Treat risks: The risks can be reduced by handling it effectively with proper treatment option. Avoiding, transferring and retaining the risks can also be considered as risk treatment options. The risk treatment plan must identify roles and responsibilities of project team and the results obtained from the treatment of the risk. It must also perform budgeting and reviewing of process. Q 2. Describe in brief the basic principles followed by the GMP principles Ans: Good manufacturing practice (GMP) is considered as part of quality assurance. It enables you to meet overall project quality, timeline, and cost objectives. This helps to consistently produce the products and maintain the quality standards, suitable to their specific use, as per the market authorisation. It helps the manufacturing organisations to compete effectively in the world market. GMP mainly focuses on reducing the risks present in production. Below are a few basic principles followed by the GMP guidelines, which are adopted by most of the manufacturing companies in the world: • Validation of critical manufacturing processes is made to ensure that these processes are consistent with specifications. Evaluation of the any changes in the manufacturing process is made in order to have less impact on the quality of the product. Instructions are well-written in an unambiguous language. Documentation of procedure and operator training are carried out. A detailed record of manufacture, which includes distribution, is maintained in a comprehensible and accessible form. Systems are configured for recalling of any manufactured product from sale or supply. Investigation of causes of defect in quality of manufactured products and examination of complaint received about the marketed products are undertaken to prevent re-occurrence. If the above guidelines are not correctly implemented by the manufacturing companies, then there will be the risks of poor quality products or defects in the products, which will result in gaps in the services. GMP guidelines do not provide any instructions on how to manufacture a product; instead they provide a series of basic principles, which must be noted during manufacturing process. When a company decides for manufacturing process, there are many ways to meet the GMP requirements. The company must take initiative to determine the most efficient quality process. Q 3. Write short note on the following risk categories:
- 4. a. Operational risks b. Schedule risks c. Budget risks d. Business risks e. Technical environment risk Ans: a. Operational risks: Improper process implementation, system failure and other external risks can lead to risks of loss. For example, loss can be due to insufficient resource, improper subject training, inability to deal with high priority conflicts and improper resource planning. b. Schedule risks: Schedule is a plan for an activity or event. If the project schedule is not addressed properly, then it gives rise to schedule risk which affects the project and its economy and may also lead to project failure. For example, delay in the project schedule is due to wrong estimation of project time, inability to track individual skills, unforeseen expansion in the project scope and failure in identifying complex functionalities and estimating the time required to develop those functionalities correctly. c. Budget risks: Budget is a sum of money allocated for a particular purpose. Budget risk is mainly due to incorrect budget estimation. This risk is also due to project scope expansion. For example, unresolved issue results in redoing the work within the given timeframe. The changes must be maintained within the scope of the project and any additional changes would require additional funding. d. Business risks: Business risks are mainly due to delay in obtaining proper inputs from the customers and business analyst. The non-availability of contracts and purchase order at the beginning of the project also lead to business risks. e. Technical environment risk: This risk relates to the environment, where the client as well as the customer works. For example, the technical environment risk can arise due to constant changes in a development, or production or testing environment. Q 4. Describe Risk assessment cycle. Ans: Risk assessment consists of many different stages. These stages are explained in a simple step-by-step process. The risk assessment cycle has the following seven stages: • Set the limits / scope of the Analysis The results of assessment are collected, analysed and reported to the management by the risk assessment team. Thus assessment team identifies the scope of the project objectives, the responsibilities of each member in the team, standards to be used, documents to be reviewed and operations to be noticed. • Identify tasks and hazards Hazards can be in form of violence, noise or any kind of pressure system. The identified hazards must not be ignored as this can lead to many associated unknown risks. A task-based approach is found to be the most effective method to identify the hazards. • Assess risk (Initial) This risk assessment helps to find out the initial risks in the project. Risk scoring system is used to rate risk at the initial stage of risk assessment process. It helps to describe how risks are measured. • Reduce risk The main aim of risk assessment is to minimise the risks to a tolerable level. The efforts to gain tolerable risk must work within the constraint of practicality and cost. Costing is the main factor to obtain tolerable risk. Accessing risks of a project is worthless if an appropriate plan is not made to reduce it. As risk reduction has already brought to an acceptable level, there is no need to further reduce the residual risk. This shows that risk reduction is an important part of risk assessment process. • Assess risk (Residual) Assessing any residual risk is necessary to complete risk assessment process. This process helps to mitigate any possible risks in the project. It must be noted that the risk scoring system used is different for different application. As the risk scoring system describes the possible ways to assess risks, the risk assessment process continues to improve. • Subjective judgement Subjective judgement is considered as the essential part of risk assessment process. Decision maker must be comfortable with the subjective nature of risk assessment. Basically uncertainty enters risk
- 5. assessment as subjective judgments. Uncertainty must be accepted as the part of the risk assessment process. • Document the results To have good and continuous improvement in risk assessment process there is need for documenting the risk assessments. It is recommended in every guideline to document the risk assessment process. This helps to gain access to the previous process results (history information) for the future reference and use. Thus upcoming projects find benefits from this document. Q.5. Describe in brief the major risk handling strategies. Ans: Risk handling simply means risk treatment. This involves identifying various options for treating risk, analysing the different options for treating the risk, preparing risk treatment plans based on the assessments made, and implementing the plans. Retaining/accepting risk When organisations identify potential risks, they put effective measures to eliminate them. However, an element of risk can be retained if it is deemed acceptable to the organisation after putting controls in place. Retaining/accepting risk is a good strategy only when it is impossible to transfer the risk. Depending on an evaluation of the economic loss, it is determined that a very small value placed on the risk can be safely absorbed. Another situation where you can retain a risk is when the probability of loss is so high that transferring the risk would cost as much as the cost due to the worst loss that can occur. So to say, if there is a high probability of loss, it may be best to retain the risk rather than transferring it to other involved party. Now let us discuss the aspect of the organisation retaining/accepting a risk with an example. G. K services are a service provider in telecom who had signed on many projects which had to be completed in a short span of time. Initially, G.K services planned to outsource the projects. It was found that outsourcing would cost them much more than the income generated from the project. So they decided to retain the risk of a delayed delivery rather than outsourcing the same. Risk abatement Risk abatement can be used as a process for combining loss prevention or loss control to minimise a risk. Organisations may include any one of the following plans to reduce the risk. Those plans include risk policies and procedures, testing, technical controls, training of staff, preventative maintenance, supervision, contract conditions, quality assurance programs, audit compliance programs and so on. This strategy helps to reduce the loss potential and decrease the frequency or severity of the loss. Risk abatement is preferably used in conjunction with other strategies, since using this risk management method alone will not totally eliminate the risk. Mitigating consequences of risk occurrence It is important to mitigate the consequences of the risk occurrence if it cannot be eliminated altogether. Some of the risk mitigating measures include effective contingency plan, disaster recovery and business continuity plans, off-site back-up, public relations, emergency procedures and staff training and so on. Transferring risk Organisations can distribute the perceived risks to another involved party by the use of contracts, insurance, outsourcing, joint ventures or partnerships and so on. Avoiding risk Organisation can avoid risks completely, wherever practically posible, by deciding not to proceed with the activities which are likely to throw risks. For example: following the review of a contract, if a client determines that a project is just too risky then the client may decide not to bid the work at all, or remove that element of the work from their bid, sometimes using an alternate deduct to describe the exclusion. Risk avoidance is strictly a business strategy, and sometimes an astute strategy if supporting documents are unclear, ambiguous or incomplete. There are various factors that must be considered in choosing a risk handling strategy. Some of the factors include: Payoff (or gains) for undertaking the risk Costs of risk management. Extent of the impact of risk. Q 6. Define change and the various types of changes Ans: Change in organisations demands changes in skills, and many feel that they will not be able to make the conversion very well. As pointed out by behavioural scientists, people cannot accept
- 6. change, since it is a fear that they seldom like to admit. This fear makes them resist the change consciously or subconsciously. In many cases, their fears are baseless, for change brings about progress. Indeed, a successful change campaign to accept change through an effective motivator, efficient new training programs is necessary. Training programs must be planned and executed in phases. In this way, you can reduce the early fear of a lack of personal capability to embrace change by showing how competence can solve the fear of acceptance. One popular model of change management is the ADKAR model which is developed by Hiatt (2006) whose observation is that the individual‟s acceptance to change is the key to success of change. The elements (ADKAR) here include the following: Awareness, (knowing the need for change) Desire, the individual‟s eagerness in the change process Knowledge (understanding) Ability (to implement one‟s skills and attitude) R- Reinforcement (to sustain the change). Organisational change management is an important aspect of almost every project. The attributes of this change management include the following: A change control policy which is a set of guidelines should be developed to streamline the change management process. The workflow of change is set by breaking the difficult activities of change to smaller elements. The resource requirements including the cost estimates, infrastructure and human are identified. Where necessary, outsourcing possibilities are also considered. Roles and responsibilities of change personnel are identified. An environment of acceptance of change is built with their support. Analysis of the various dependencies of the project based on the type of change is carried out and the approval process is set in. The steps are clearly documented and also communicated to the affected departments. Risk assessment based on the scope of the effects of change is well-defined. Change management should also provide emergency change mechanism. Metrics should be defined and reported to the board of management. They help in the performance analysis of change. Types of Changes Different types of change require different strategies and plans to effectively gain employee engagement and acceptance of change. According to Ackerman (1997), there are three types of change that occur most frequently in organisations, they are: developmental, transitional, and transformational. Organisational change management theories effectively support how to deal with developmental and transitional change, but are less effective at dealing with successfully implementing transformational change. The organisation is first evaluated on the type of change it is experiencing. Then accordingly, the change approach is employed to overcome resistance. Types of changes are: Developmental change It is a method applied to maintain a competitive edge in business. It enhances or corrects existing aspects of an organisation, often by focusing on the improvement of a skill or process. This type of change could be either planned or emergent (unplanned) or incremental (continual). When an organisation decides to improve its processes, methods or performance standards, then this process is considered. This type of change should cause little stress to current employees as long as the rationale for the new process is clearly conveyed and the employees are educated on the new technique. The key focus here is to strengthen or correct what is already present. There is no change in the culture, values or mindset of the organisation. Transitional change It replaces existing processes or procedures of the organisation with a new one. This type of change could be planned, episodic or radical. It is, therefore, more intrusive than developmental change. The process involves dismantling of an old state and a clear new state being created. This is carried out over a period of time and is called the transition state. Few examples of transitional change are: corporate reorganisation, merger, acquisition, creating new products or services, and implementing new technology. This model can be episodic, planned and second order.
- 7. It creates a level of discomfort in employees because the outcome of the change is unknown. Employees may feel insecure about their job but proper training given to employees on the new policies and procedures will motivate them to be a part of the change thereby reducing the resistance to change. Lewin (1951) coined changes as a three-stage process which involves: Unfreeze - Move – refreeze approach. Here he explains how people are frozen to their existing organisational equilibrium and have to be unfrozen(made ready to change), move to the change journey and finally refreeze (have to stabilise themselves to change) Schein in 1987 suggested that the unfreeze approach involved the provision of psychological safety, moving needed a cognitive restructuring and finally refreeze involves total integration of the change with the self. Transformational change • Organisations sometimes face emergence of radically different technologies, significant changes in supply and demand, unexpected competition, and lack of revenue or other major shifts in business. Developmental or transitional change may not offer the solution they need to stay competitive. Instead of methodically implementing new processes, the organisation would prefer to radically transform the existing process, structure, culture, mindset or strategy. It may involve both developmental and transitional change. Also referred as quantum change. It is common for transitional and transformation change to occur in turns. Business process reengineering is an example. Transformational change requires competent leaders to manage and is one of the most complex changes. Categorising change There are a number of ways in which change can be categorised. Most of them are related to the extent of the change. Planned versus emergent change Sometimes change is intentional with reasons that support it. This type of change is called planned change. In contrast, change could happen in an apparently spontaneous and unplanned way. This type of change is known as emergent change. Emergent change results in the following cases: Managers make decisions which are not planned. However these decisions are based on unconscious hypothesis about the organisation, its environment (Mintzberg 1989) and the future and are, therefore, not as unrelated as they initially seem. External factors such as the economy, competitors‟ behaviour, and political climate or internal features such as the relative power of different interest groups, distribution of knowledge, and uncertainty influence the change in directions beyond the control of managers. Even the most carefully planned and executed change programme can have some emergent impacts. Thus the two important aspects of managing change are to identify, explore and if necessary challenge the assumptions that underlie managerial decisions. Episodic versus continuous change Another difference between episodic and continuous change is: • Episodic change, according to Weick and Quinn1 (1999), is „infrequent, irregular and intentional‟. Occasionally termed „radical‟ or „second order‟ change, episodic change often engross replacement of one strategy or programme with another. Continuous change, in comparison, is „ongoing, developing and cumulative‟. Also referred to as „first order‟ or „incremental‟ change, constant change is characterised by people constantly adapting and editing ideas they acquire from different sources. The difference between episodic and continuous change helps clarify thinking about an organisation‟s future development and evolution in relation to its long-term goals. Few organisations decide unilaterally that they adopt an exclusively continuous change approach. They can, however, capitalise upon many of the principles of continuous change by being elastic to contain and experiment with everyday contingencies, breakdowns, exceptions, opportunities, and unintended consequences that interrupts organisational life
