assignment
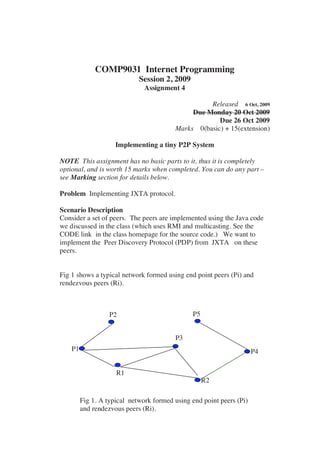
- 1. COMP9031 Internet Programming Session 2, 2009 Assignment 4 Released 6 Oct, 2009 Due Monday 20 Oct 2009 Due 26 Oct 2009 Marks 0(basic) + 15(extension) Implementing a tiny P2P System NOTE This assignment has no basic parts to it, thus it is completely optional, and is worth 15 marks when completed. You can do any part – see Marking section for details below. Problem Implementing JXTA protocol. Scenario Description Consider a set of peers. The peers are implemented using the Java code we discussed in the class (which uses RMI and multicasting. See the CODE link in the class homepage for the source code.) We want to implement the Peer Discovery Protocol (PDP) from JXTA on these peers. Fig 1 shows a typical network formed using end point peers (Pi) and rendezvous peers (Ri). P2 P5 P3 P1 P4 R1 R2 Fig 1. A typical network formed using end point peers (Pi) and rendezvous peers (Ri).
- 2. Types of peers We use two types of peers - End point peer(P) and Rendezvous peer(R). When a message is sent to a peer, the peer will send an appropriate response to the message, if the peer is an End point peer. When the peer is a Rendezvous peer, it not only sends an appropriate response to a message, but also forwards the message to all its neighbours. Types of resources We support only one type of resource, viz., Files. Files can be any files such as myfile.text, yourfile.pdf, etc. What do peers typically do? Peers typically want to share their resources with the others peers. So, when a peer P1 has a file file1.txt that it wants to share with the other peers, it advertises the description of the file to all its neighboring peers. Another peer, say P4, looking for file1.txt, tries to discover its owner using the PDP protocol. If it succeeds in its discovery, it downloads the file directly from the peer P1; otherwise, it waits till some one sends the owner’s ID. Peer Discovery Protocol (PDP) The PDP protocol is used to locate a peer that may posses a specific file, say file1.txt. Suppose P1 advertises that it has the file file1.txt. The advertisement reaches all of (and only) P1’s neighbours, and the neighbours store the contents of the advertisements in their memory. (Storing the message in memory is called caching.) Suppose another peer P4 wants to discover if anyone has the file file1.txt. Peer P4 sends a Discovery Query Message (DQM) to all of its neighboring peers, namely R2 and P5, and these peers cache the DQM in their memory. The edge peer P5 looks into its cache, finds no mention about any advertisement regarding file1.txt, so it sends a negative response to P4. However, the rendezvous peer R2 looks into its cache, finds no mention about any advertisement regarding file1.txt, sends a negative reply to P4, but also forwards the DQM to all its neighbours(R1 and P3). Peer p3, caches the DQM in its memory, finds from its cache that file1.txt is available with p1, and sends a positive response directly to P4. Thus, P4 comes to know that P1 has the file file1.txt it is looking for. The peer P4 then downloads the file from P1.
- 3. Also note that it is possible that P4 may send its DQM for a resource even though no one may have it, or no one may have advertised it. In such cases, since the DQM message is cached in some of the peers, they will respond positively to P4 whenever they receive P1’s advertisement. We also need to consider the following cases. New peer joining the network A new peer p may want to join the network. It does so by sending a Hello message to all peers in the network. All peers will reply YES to p, p will randomly select some of them, become their neighbor, and send a regret message to all other peers. Leaving the network Any peer may want to leave the network at anytime. It does so by sending a BYE message to all its neighbors, waits for their replies, and then leaves the network. Peer crashing A peer may crash without warning. In such cases, each one of its neighbours will need to detect it, and drop it from its list of neighbours. You can choose your own format or structure for the messages. It does not have to be in XML. Choose your own format for file advertisement, and for DQM and replies. IMPLEMENTATION Provide the following GUI at each peer. See Fig 2 for GUI display details. The GUI shows the name of the peer, its type (EDGE or ENDEZVOUS) and the list of its neighbors. The CACHE CONTENTS window displays the current content of the cache and the LOG window displays the log of activities that went on in the peer. CACHE CONTENTS window must show the file advertisements and the DMQ requests. The LOG window must show: File advertisement, receiving DMQ, request from new members to join, regret received, peer crashing, and receiving BYE messages from leaving peers. It is not necessary to show any other types of messages.
- 4. Events from clicking the following buttons: NAME/TYPE – When this button is clicked, ask for the name and type of the peer and display them in PEER INFORMATION WINDOW. JOIN - When the JOIN button is clicked, this peeer joins the existing network, The neigbours list is updated in PEER INFORMATION WINDOW. (Assume that this is a new peer, and it will attempt to join only once.) LEAVE - when clicked, this peer leaves the network. Set neighbours list to empty. The peer will still be running. ADVERTISE - When clicked, ask for the name of a file from the user, and send an advertisement for this file to all neighbors. (Choose your own format for this message.) DISCOVER - When clicked, ask for the name of a file, and send a DMQ message to all neighbors. (Choose your own format for this message.) Events related to LOG Messages: If you receive a file advertisment, then update cache contents and display a log message. If you receive a DMQ message, then update cache contents and display a log message. If you receive a Hello message from a new peer P' and P' becomes your neighbour, then update the Neighbours list, and display a log message. If you detect that a peer P' has crashed, then update your Neighbours list and display a log message. CRASH – When clicked, the peer stops sending muilticasting messages and does not respond to any messages, or the peer stops running altogether and the window closes.
- 5. EXIT - When clicked, this peer performs the LEAVE operation, and closes the window. The peer is not running any more. PEER GUI TINY P2P LOG WINDOW File advt for file1.txt NAME/ TYPE received from P1. DMQ received for P4. Request from new member P6 received. JOIN LEAVE Regret from P6 received. Peer P2 crash detected. ADVERTISE DISCOVER P4 BYE message received. .... .... PEER INFORMATION WINDOW Name: P1 Type: EDGE Neighbours: P2 P3 R1 CACHE CONTENTS WINDOW <ADVT P1 file1.txt> <DMQ P4 file2.txt> <DMQ R2 file1.txt> .... .... CRASH EXIT
- 6. Fig 2. Peer GUI Marking Scheme Basic Part (0 marks) – there are no basic parts in this assignment. Everything is an extension and thus is optional. Extension Part (15 marks) JOIN button – 2 marks, LEAVE button – 2 marks, ADVETISE – 2 marks, DISCOVER – 6 marks, CRASH – 2 marks, EXIT – 1 mark. (If you score, say k marks, in this assignment, then the remaining 15 – k marks will be added to your Final Exam weight (which is currently 40%)) Submission details Submit your entire code, readme file, plus bat or shell files. % give cs9031 ass4 Ass4.jar Running your program We start with one peer network, create another peer, join the network, and continue to build the network and test all the buttons. Please post your questions on the subject forum in the Ass4 thread.
