Digital Watermarking
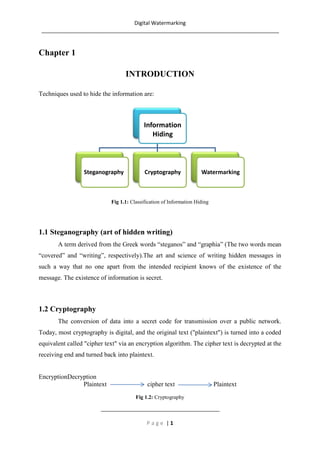
- 1. Digital Watermarking ________________________________________________________________________________ Chapter 1 INTRODUCTION Techniques used to hide the information are: Information Hiding Steganography Cryptography Watermarking Fig 1.1: Classification of Information Hiding 1.1 Steganography (art of hidden writing) A term derived from the Greek words “steganos” and “graphia” (The two words mean “covered” and “writing”, respectively).The art and science of writing hidden messages in such a way that no one apart from the intended recipient knows of the existence of the message. The existence of information is secret. 1.2 Cryptography The conversion of data into a secret code for transmission over a public network. Today, most cryptography is digital, and the original text ("plaintext") is turned into a coded equivalent called "cipher text" via an encryption algorithm. The cipher text is decrypted at the receiving end and turned back into plaintext. EncryptionDecryption Plaintext cipher text Plaintext Fig 1.2: Cryptography ________________________________________ Page |1
- 2. Digital Watermarking ________________________________________________________________________________ 1.3 Watermarking A distinguishing mark impressed on paper during manufacture; visible when paper is held up to the light (e.g. $ Bill) Physical objects can be watermarked using specialdyes and inks or during paper manufacturing. Fig 1.3:Watermarked currency 1.3.1 History of watermarking The term “watermark” was probably originated from the German term “wassermarke”. Since watermark is of no importance in the creation of the mark, the name is probably given because the marks resemble the effects of water on paper. Papers are invented in China over athousand years ago. However, the first paper watermark did not appear until 1282, in Italy. By the 18th century, watermarks on paper in Europe and America had been used as trademarks, to record the manufactured date, or to indicate the size of original sheets. Watermarks are commonly used on bills nowadays to avoid counterfeiting 1.3.2 Advancing to Digital Watermarking In recent times, due to great developments in computer andinternet technology, multimedia data i.e. audio, images and video have found wide applications. Digital watermarking is one of the best solutions to prevent illegal copying, modifying and redistributing multimedia data. Encryption of multimedia products prevents an intruder from accessing the contents without a proper decryption key. But once the data is decrypted, it can be duplicated and distributed illegally. To enforce IP rights and to prevent illegal duplication, interpolation and distribution of multimedia data, Digital watermarking is an effective ________________________________________ Page |2
- 3. Digital Watermarking ________________________________________________________________________________ solution. Copyright protection, data authentication, covert communication and content identification can be achieved by Digital watermarking. Digital watermarking is a technique to embed copyright or other information into the underlying data. The embedded data should maintain the quality of the host signal. In order to achieve the copyright protection, the algorithm should meet few basic requirements i) Imperceptibility: The watermark should not affect the quality of the original signal, thus it should be invisible/ inaudible to human eyes/ ears. ii) Robustness: The watermarked data should not be removed or eliminated by unauthorized distributors, thus it shouldbe robust to resist common signal processingmanipulations such as filtering, compression, filteringwith compression. iii) Capacity: the number of bits that can be embedded in onesecond of the host signal. iv) Security: The watermark should only be detected byauthorized person. v) Watermark detection should be done without referencingthe original signals. vi)The watermark should be undetectable without prior knowledge of the embedded watermark sequence. vii) The watermark is directly embedded in the signals, not ina header of the signal. All these requirements are often contradictory with each otherand we need to make a trade-off among them. For exampleincreasing data rate in watermarking system results in qualitydegradation of the watermarked signal and decreases therobustness against attacks. Imperceptibility and robustness arethe most important properties for many applications. Theseconflicting requirements pose many challenges to design ofrobust watermarking. ________________________________________ Page |3
- 4. Digital Watermarking ________________________________________________________________________________ Chapter 2 WHAT IS DIGITAL WATERMARKING? Watermarking can also be applied to digital signals! (a) Images (b) Video (c) Audio Fig 2.1 A digital watermark is a pattern of bits inserted into a digitalimage, audio or video file that identifies the file's copyright information (author, rights, etc.). The name “watermark” is derived from the faintly visible marks imprinted on organisational stationery. In addition, the bits representing the watermark must be scattered throughout the file in such a way that they cannot be identified and manipulated. And finally, a digital watermark must be robust enough to survive changes to the file its embedded in, such as being saved using a lossycompressionalgorithm eg: JPEG. Satisfying all these requirements is no easy feat, but there are a number of companies offering competing technologies. All of them work by making the watermark appear as noise that is, random data that exists in most digital files anyway. Digital Watermarking works by concealing information within digital data, such that it cannot be detected without special software with the purpose of making sure the concealed data is present in all copies of the data that are made whether legally or otherwise, regardless of attempts to damage/remove it. Thepurposeofdigitalwatermarksis toprovidecopyrightprotection for intellectual property that is in digital format. ________________________________________ Page |4
- 5. Digital Watermarking ________________________________________________________________________________ Fig 2.2 As seenabove in Fig 3.2,Alicecreatesan original image and watermarks it beforepassingittoBob.IfBobclaims the image and sells copies to otherpeopleAlicecanextracther watermarkfromtheimageproving her copyright to it. ThecaveathereisthatAlicewillonlybeabletoprovehercopyright oftheimageifBobhasn’tmanagedtomodifytheimagesuchthat thewatermarkisdamagedenough to be undetectable or added his own watermark such that it is impossible to discover which watermark was embedded first. 2.1How Watermarking is Different from Steganography and Cryptography. 2.1.1Steganography vs. Watermarking The main goal of steganography is to hide a message m in some audio or video (cover) data d, to obtain new data d', practically indistinguishable from d, by people, in such a way that an eavesdropper cannot detect the presence of m in d'. The main goal of watermarking is to hide a message m in some audio or video (cover) data d, to obtain new data d', practically indistinguishable from d, by people, in such a way that an eavesdropper cannot remove or replacem in d'. It is also often said that the goal of steganography is to hide a message in one-to-one communications and the goal of watermarking is to hide message in one-to-many communications. ________________________________________ Page |5
- 6. Digital Watermarking ________________________________________________________________________________ Shortly, one can say that cryptography is about protecting the content of messages, steganography is about concealing its very existence. Steganography methods usually do not need to provide strong security against removing or modification of the hidden message. Watermarking methods need to to be very robust to attempts to remove or modify a hidden message. 2.1.2Cryptography vs. Watermarking Watermarking is a totally different technique from cryptography. Cryptography only provides security by encryption and decryption. However, encryption cannot help the seller monitor how a legitimate customer handles the content after decryption. So there is no protection after decryption. Unlike cryptography, watermarks can protect content even after they are decoded. Other difference is cryptography is only about protecting the content of the messages. Because watermarks are inseparable from the cover in which they are embedded, so in addition to protecting content they provide many other applications also, like copyright protection, copy protection, ID card security etc. 2.2 Characteristics of Digital Watermarking Invisibility: an embedded watermark is not visible. Robustness: piracy attack or image processing should not affect the embedded watermark. Readability: A watermark should convey as much information as possible. A watermark should be statisticallyundetectable. Moreover, retrieval of the digital watermark can be used to identify the ownership and copyrightunambiguously. Security: A watermark should be secret and must be undetectable by an unauthorized user in general. Awatermark should only be accessible by authorized parties. This requirement is regarded as a security and thewatermark is usually achieved by the use of cryptographic keys. As information security techniques, the details of adigital watermark algorithm must be published to everyone. The owner of the intellectual ________________________________________ Page |6
- 7. Digital Watermarking ________________________________________________________________________________ property image is the onlyone who holds the private secret keys. A particular watermark signal is related with a special number usedembedding and extracting. The special number is kept secretly and is used for confirming legal owners of digitalproducts later. If we lay strong stress on robustness, and then invisibility may be weak. If we put emphasis oninvisibility, then vice versa. Therefore, developing robustness watermark with invisibility is an important issue. 2.3 History of digital watermarking The first watermarking example similar to thedigital methods nowadays appeared in 1954.The Muzak Corporation filed a patent for“watermarking” musical Work. Anidentification Work was inserted in music byintermittently applying a narrow notch filtercentred at 1KHz. About 1995, interest in digital watermarking began to mushroom. The water marking fever Fig 2.3: Annualnumber ofpaperspublishedonwatermarking ________________________________________ Page |7
- 8. Digital Watermarking ________________________________________________________________________________ Chapter 3 WATERMARKING CLASSIFICATION Digital Watermarking techniques can be classified in a number of ways depending on different parameters. Various types of watermarking techniques are enlisted below. Robust & Fragile Watermarking Robust watermarking is a technique in which modification to the watermarked content will not affect the watermark. As opposed to this, fragile watermarking is a technique in which watermark gets destroyed when watermarked content is modified or tampered with. Visible & Transparent Watermarking Visible watermarks are ones, which are embedded in visual content in such a way that they are visible when the content is viewed. Transparent watermarks are imperceptible and they cannot be detected by just viewing the digital content. Public & Private Watermarking In public watermarking, users of the content are authorized to detect the watermark while in private watermarking the users are not authorized to detect the watermark. Asymmetric & Symmetric Watermarking Asymmetric watermarking (also called asymmetric key watermarking) is a technique where different keys are used for embedding and detecting the watermark. In symmetric watermarking (or symmetric key watermarking) the same keys are used for embedding and detecting watermarks. Steganographic &Non-Steganographic watermarking Steganographic watermarking is the technique where content users are unaware of the presence of a watermark. In nonsteganographic watermarking, the users are aware of the presence of a watermark. Steganographic watermarking is used in fingerprinting applications while nonsteganographic watermarking techniques can be used to deter piracy. ________________________________________ Page |8
- 9. Digital Watermarking ________________________________________________________________________________ Chapter 4 DIGITAL WATERMARKING LIFE CYCLE PHASES Fig 4.1:Block diagram of a watermarking system. The information to be embedded in a signal is called a digital watermark, although in some contexts the phrase digital watermark means the difference between the watermarked signal and the cover signal. The signal where the watermark is to be embedded is called the host signal. A watermarking system is usually divided into three distinct steps 1. Embedding 2. Attack 3. Detection/Extraction 4.1 Embedding In embedding, an algorithm accepts the host and the data to be embedded, and produces a watermarked signal. Fig 4.2: Embedding Inputs to the scheme are the watermark, the cover dataand an optional public or secret key. The outputs are watermarkeddata.The key is used to enforce security. ________________________________________ Page |9
- 10. Digital Watermarking ________________________________________________________________________________ 4.2 Attacks The watermarked digital signal is transmitted or stored, usually transmitted to another person. If this person makes a modification, this is called an attack. While the modification may not be malicious, the term attack arises from copyright protection application, where pirates attempt to remove the digital watermark through modification. There are many possible modifications, for example, lossy compression of the data (in which resolution is diminished), cropping an image or video, or intentionally adding noise. 4.3 Extraction Extraction is an algorithm which is applied to the attacked signal to attempt to extract the watermark from it. If the signal was unmodified during transmission, then the watermark still is present and it may be extracted. Fig 4.3: Extraction Inputs to the scheme are the watermarked data, the secret or public key and, depending on the method, the original dataand/or the original watermark. The output is the recoveredwatermarked W or some kind of confidence measure indicatinghow likely it is for the given watermark at the input to be present inthe data under inspection. ________________________________________ P a g e | 10
- 11. Digital Watermarking ________________________________________________________________________________ Chapter 5 WATERMARKING TECHNIQUES Watermarking Frequency Spatial Domain Domain Watermarking Watermarking Discrete Least SSM- Discrete Cosine Wavelet Significant Bit Modulation Transformation Transformation Fig 5.1: Watermark Techniques 5.1 Spatial Domain Techniques Some of the Spatial Techniques of watermarking are as follow. 5.1.1 Least-Significant Bit (LSB) The earliest work of digital image watermarking schemes embeds watermarks in the LSB of the pixels. Given an image with pixels, and each pixel being represented by an 8-bit sequence, the watermarks are embedded in the last (i.e., least significant), bit, of selected pixels of the image. This method is easy to implement and does not generate serious distortion to the image; however, it is not very robust against attacks. For instance, an attacker could simply randomize all LSBs, which effectively destroys the hidden information. 5.1.2SSM-Modulation-Based Technique Spread-spectrum techniques are methods in which energy generated at one or more discrete frequencies is deliberately spread or distributed in time or frequency domains. This is done for a variety of reasons, including the establishment of secure communications, increasing resistance to natural interference and jamming, and to prevent detection. When applied to the context of image watermarking, SSM based watermarking algorithms embed ________________________________________ P a g e | 11
- 12. Digital Watermarking ________________________________________________________________________________ information by linearly combining the host image with a small pseudo noise signal that is modulated by the embedded watermark. 5.2 Frequency Domain Techniques Compared to spatial-domain methods, frequency-domain methods are more widely applied. The aim is to embed the watermarks in the spectral coefficients of the image. The most commonly used transforms are the Discrete CosineTransform (DCT), Discrete Fourier Transform (DFT), Discrete Wavelet Transform (DWT), Discrete LaguerreTransform (DLT) and the Discrete Hadamard Transform (DHT). The reason for watermarking in the frequencydomain is that the characteristics of the human visual system (HVS) are better captured by the spectral coefficients.For example, the HVS is more sensitive to low- frequency coefficients, and less sensitive to high-frequency coefficients. In other words, low- frequency coefficients are perceptually significant, which means alterations to those components might cause severe distortion to the original image. On the other hand, high- frequency coefficients are considered insignificant; thus, processing techniques, such as compression, tend to remove high-frequency coefficients aggressively. To obtain a balance between imperceptibility and robustness, most algorithms embed watermarks in the midrange frequencies. 5.2.1 Discrete Cosine Transformation (DCT) DCT like a Fourier Transform, it represents data in terms of frequency space rather than an amplitude space. This is useful because that corresponds more to the way humans perceive light, so that the part that are not perceived can be identified and thrown away. DCT based watermarking techniques are robust compared to spatial domain techniques. Such algorithms are robust against simple image processing operations like low pass filtering, brightness and contrast adjustment, blurring etc. However, they are difficult to implement and are computationally more expensive. At the same time they are weak against geometric attacks like rotation, scaling, cropping etc. DCT domain watermarking can be classified into Global DCT watermarking and Block based DCT watermarking. Embedding in the perceptually significant portion of the image has its own advantages because most compression schemes remove the perceptually insignificant portion of the image. ________________________________________ P a g e | 12
- 13. Digital Watermarking ________________________________________________________________________________ 5.2.2 Discrete Wavelet Transformation (DWT) The Discrete Wavelet Transform (DWT) is currently used in a wide variety of signal processing applications, such as in audio and video compression, removal of noise in audio, and the simulation of wireless antenna distribution. Wavelets have their energy concentrated in time and are well suited for the analysis of transient, time-varying signals. Since most of the real life signals encountered are time varying in nature, the Wavelet Transform suits many applications very well. 5.3 Backdrops of above mentioned watermark technique systems Scope Tamper Proofing Inseparability Transparency / Visibility Insecurity 5.4 Fast Hadamard Transform (FHT) FHT Technique/Algorithm has many advantages over above mentioned techniques, those are Shorterprocessingtime Invisibilityofthewatermarkguaranteed Increasedwatermarkenergyleadstohigherrobustness 5.4.1 2D-Hadamard transform of signal The 2D-Hadamard transform has been used extensively in image processing and image compression. In this section, we give a brief review of the Hadamard transform representation of image data, which is used in the watermarking embedding and extraction process. Let [U] represents the original image and [V] the transformed image, the 2D-Hadamard transform is given by: ________________________________________ P a g e | 13
- 14. Digital Watermarking ________________________________________________________________________________ (1) Where Hnrepresents an N×N Hadamard matrix, N=2n, n=1,2,3…, with element values either +1 or –1. The advantages of Hadamard transform are that the elements of the transform matrix Hnare simple: they are binary, real numbers andthe rows or columns of Hnare orthogonal. Hence the Hadamard transform matrix has the following property: Hn = Hn* = HT = H-1(2) Since Hnhas N orthogonal rows HnHn= NI (I is the identity matrix) and HnHn= NHnHn- 1 , thus Hn–1= Hn/N. The inverse2D-fast Hadamard transform (IFHT) is given as (3) In our watermarking algorithm, the forward and reverse Hadamard transform is applied to the sub-blocks of the originalor watermarked images. A two-dimensional FHT of the segmented 8×8 blocks is performed by applying a one dimensional FHT on the rows first and then followed by a 1-D FHT on the columns. In the computer implementation, the 8×8 sub-block is first multiplied by Hadamard matrix, and then the resultant matrix is transposed and multiplied by the Hadamard matrix again. The final matrix is the transformed matrix. For N=2, the Hadamard matrix, H1, is called a core matrix, which is defined as (4) The Hadamard matrix of the order n is generated in terms of Hadamard matrix of order n-1 using Kroneckerproduct, ⊗, as Hn=Hn-1⊗H1 (5) ________________________________________ P a g e | 14
- 15. Digital Watermarking ________________________________________________________________________________ Or (6) Since in our algorithm, the processing is carried out based on the 8×8 sub-blocks of the whole image, the third orderHadamard transform matrix H3 is used. By applying (5) or (6), H3 becomes: (7) The characteristic of the rows or columns of H3 is sign transitions, which is defined as a 1 to –1 or –1 to 1 change. In H3, the number of transitions for row 1 to row 8 is 0, 7, 3, 4, 1, 6, 2 and 5 according to equation (7). The number of sign changes is referred to as sequency. The concept of sequency is analogous to its Fourier counterpart frequency. Zero sign transitions correspond to DC and a large number of sign transitions correspond to high frequency. In Hadamard matrix H3, the elements are not arranged in increasing sequency, such that the number of transitions is 0, 1, 2, 3, 4, 5, 6and 7. If the order of rows is in ascending of sequency, this transform matrix is called a Walsh transform matrix. A Walsh transform may cause the transformed matrix to have DC value at upper left corner and AC coefficients arrange in Zigzag order from low frequency components to high frequency components. The Walsh transform is not used here because the middle and high frequency AC components, which could be watermarked has shown to be somewhat unreliable and the performance worse than existing DCT watermarking algorithms. On the contrary, the Hadamard transform matrix H3 has its AC components in Hadamard order. It is possible that in the watermarking process, some of the watermark information can be embedded into the low frequency AC components. This increases the mark reliability and makes it more ________________________________________ P a g e | 15
- 16. Digital Watermarking ________________________________________________________________________________ difficult to attack and remove. Moreover, Hadamard transform has more useful middle and high frequency bands available, for hiding the watermark, as compared to other high coding gain transforms like DCT and DWT, at high noise environment. It has been shownthat transforms including DCT and sub-band transforms are suitable for watermarking when the channel noise is low. But low channel noise condition is not usually the case. For low quality JPEG or wavelet compression as well as some linear or nonlinear filtering such as Gaussian filtering and median filtering, the processing noise approachesinfinity for the middle and high frequency bands. In these cases, the high gain transform watermarking methods are not very robust. But middle and high frequency Hadamard transform coefficients have components equivalent to where many DCT low-frequency AC coefficients are located. So it is more likely that in high noise environment the Hadamard transform bands would remain and unscathed and immune to the channel noise. Furthermore, low quality JPEG and wavelet compression could normally affect the high frequency components of DCTor DWT based watermarked image than the high frequency components in the Hadamard bands. Watermark information embedded in these components of DCT and DWT may be removed by these compressions. However, Hadamard transform would survive the compression as some of the watermark energy is embedded into the equivalent low frequency components of DCT and DWT domain. Therefore, decompositions that are not so efficient for compression, such as the Hadamard transform, would provide more immunity to channel noise than decompositions with high coding gain transform. Another advantage of using the FHT is that it has a shorter processing time and its ease of hardware implementation than many commonly used orthogonal transforms. An efficient FHT hardware structure has been reported. Based on the radix-2 algorithm, the structure can be implemented with shift register and controllable adder/subtracters for high processing throughput. This makes it possible for the real-time implementation of a digital watermarking system. ________________________________________ P a g e | 16
- 17. Digital Watermarking ________________________________________________________________________________ 5.4.2Experiment Results and Discussions The experiment for the watermarking system is performed using the MATLAB 6 platform. Two container test images consist of lenna.bmp cameraman.bmp are selected for the experiment. All these images are of sizes of 512×512×8bit, grayscale intensity images. For the robustness test, we use the Stirmark benchmarking software that consistsapproximately 90 different types of image manipulations or attacks. The Stirmark attacks destroy the synchronization required in information retrieval via applying some small random geometrical transforms in such a way that the distortion is not visually perceivable. Some Stirmark attack examples such as cropping, changing aspect ratio, rotation and JPEG compression are shown in figure 5.2: (a)Original watermarked (b) image Cropping 50% (c) Rotation 30° (d)Changing aspect ratio(e) 3×3 median filtering (f)JPEG compression x-1 y-0.8 factor 35 Fig 5.2: Stirmark attack examples on watermarked image lenna.bmp For our algorithm, a maximum image size of 256×256×8bit can be hidden into the container digital image of size512×512×8bit. In the experiment, a grayscale image dmt.bmp with size 64×64×8bit is used. The original and watermarked image examples are shown in figure 5.3: (lenna.bmp marked with image dmt.bmp) ________________________________________ P a g e | 17
- 18. Digital Watermarking ________________________________________________________________________________ (a) Original image (b) Watermarked image (c) Original watermark (d) Extracted watermark Fig 5.3:Original and watermarked images for image embedded algorithm Results show that there were no perceptually visible degradations on the watermarked images. The extracted watermarkis also highly correlated with the original watermark with correlation factor 0.989. Results using benchmarking softwareStirmark are shown in Table 1: (lenna.bmp is marked with image dmt.bmp) Table 5.1: Results of some Stirmark tests for image-in-image embedding algorithm ________________________________________ P a g e | 18
- 19. Digital Watermarking ________________________________________________________________________________ Chapter 6 ANALYSIS OF ROBUSTNESS The similarity measurement between original watermark and extracted watermark is obtained through Normalized Correlation (NC) coefficient and Accuracy Rate (AR). 6.1 Normalized Correlation (NC) The Normalized correlation Coordinate (NCC) computes the similarity measurement of original watermark and extracted watermark, which is defined as Where N×N is the size of watermark, W(i,j) and W’(i,j) represents the watermark and recovered watermarkimages respectively. 6.2 Accuracy Rate (AR) The Accuracy Rate (AR) is used to measure the difference between the originalwatermark and the recovered one. AR is computes as follows: AR= CP/ NP Where NP is the number of pixels in the original watermark and CP is the number of correct pixels obtained by comparing the pixels of the original watermark to the corresponding ones of the recovered watermark. ________________________________________ P a g e | 19
- 20. Digital Watermarking ________________________________________________________________________________ Chapter 7 APPLICATIONS OF WATERMARKING 7.1 Security In the field of data security, watermarks may be used for certification, authentication, and conditional access. 7.1.1 Certification It is an important issue for official documents, such as identity cards or passports. Digital watermarking allows to mutually link information on the documents. That means some information is written twice on the document, for instance, the name of a passport owner is normally printed in clear text and is also hidden as an invisible watermark in the photo of the owner. If anyone would intend to duplicate the passport by replacing the photo, it would be possible to detect the change by scanning the passport and verifying the name hidden in the photo does not match any more the name printed on the passport. 7.1.2 Authentication The goal of this application is to detect alterations and modifications in an image. Suppose we have picture of a car that has been protected with a watermarking technology. And if, the same picture is shown but with a small modification, say, the numbers on the license plate has been changed. Then after running the watermark detection program on the tampered photo, the tampered areas will be indicated in different color and we can clearly say that the detected area corresponds to the modifications applied to the original photo. 7.1.3 Conditional access For example conditional access to confidential data on CD-ROMs may be provided using digital watermarking technology. The concept consists of inserting a watermark into the CD label. In order to read and decrypt the data stored on the CD, the watermark has to be read since it contains information needed for decryption. If someone copies the CD, he will not be able to read the data in clear-text since he does not have the required watermark. ________________________________________ P a g e | 20
- 21. Digital Watermarking ________________________________________________________________________________ 7.2 Copyright Protection Copyright protection inserts copyright information into the digital object without the loss of quality. Whenever the copyright of a digital object is in question, this information is extracted to identify the rightful owner. It is also possible to encode the identity of the original buyer along with the identity of the copyright holder, which allows tracing of any unauthorized copies. 7.3 Copy protection Copy protection attempts to find ways, which limits the access to copyrighted material and/or inhibit the copy process itself. Examples of copy protection include encrypted digital TV broadcast, access controls to copyrighted software through the use of license servers and technical copy protection mechanisms on the media. A recent example is the copy protection mechanism on DVDs. However, copy protection is very difficult to achieve in open systems, as recent incidents (like the DVD hack) show. 7.4 Other applications Digital watermarks can also serve as invisible labels and content links. For example, photo development laboratories may insert a watermark into the picture to link the print to its negative. This way is very simple to find the negative for a given print. All one has to do is scan the print and extracted the information about the negative. In order to distinguish between different copies, different watermarks are embedded into different copies of the same document. These marks are also called "digital fingerprints". ________________________________________ P a g e | 21
- 22. Digital Watermarking ________________________________________________________________________________ CONCLUSION Digital watermarking has rapidly advanced from theory to practice. This report focuses on how watermarking techniques are advantageous over stegnography, cryptography and also focuses on different types and domains of digital watermarking techniques. A common application requirement for the watermarks is that they resist attacks that would remove it. Some of the watermarks being attack-resistant may be accidentally removed by unintended attacks such as cropping, reduction, or compression. There are also other techniques like blind watermarking (which uses multiple watermarks and also no need of original image at the of watermark recovery), which uses watermark nesting and encryption. Nesting means it embeds an extra watermark into the main watermark and then embeds the main watermark into the cover image. This report has presented a hybrid watermarking technique for embedding characters or grayscale image watermark into a container digital image based on the FHT for copyright protection. Although Hadamard transform has lower energy compaction capability than other high gain transforms, it was found to be more suitable for watermarking application because the watermark energy could spread over the whole workspace and more likely to survive under various attacks compared to other high gain transform domain such as DCT. The experimental results showed that the proposed method is robust against most of the Stirmark attacks and Checkmark non-geometric attacks. It was also shown to be more robust than DCT algorithm under the same malicious attacks. Moreover, the Hadamard transform offers a significant advantage in shorter processing time and ease of hardware implementation than commonly used DCT and DWT techniques. ________________________________________ P a g e | 22
- 23. Digital Watermarking ________________________________________________________________________________ REFERENCES [1] M. Swanson, B. Zhu, A. Tewfik, and L. Boney, “Robust audiowatermarking using perceptual masking,”Signal Process., Special Issue onWatermarking, 1997, pp. 337- 355. [2] L. Boney, A. Tewfik, and K. Hamdy, “Digital watermarks for audio signals,” in IEEE Proc. Multimedia, 1996, pp. 473-480. [3] M. Swanson, M. Kobayashi, and A. Tewfik, “Multimedia data-embedding and watermarking strategies,” Proc. IEEE, vol. 86, pp. 1064-1087, June 1998. [4] Christine I. Podilchuk and Edward J. Delp, “Digital Watermarking: Algorithms and Applications”,IEEE SIGNAL PROCESSING MAGAZINE, 1053- 5888/01/$10.00©2001IEEE [5] Keshav S Rawat, Dheerendra S Tomar, “Digital watermarking schemes for authorization Against copying or piracy of color images” in IEEE, Vol. 1 No. 4 295- 300 [6] Anthony T.S.Ho, Jun Shen, Soon Hie Tan “A Robust Digital Image-in-Image Watermarking Algorithm Using the Fast Hadamard Transform” Proceedings of SPIE Vol. 4793 (2003) © 2003 SPIE · 0277-786X/03/$15.00 ________________________________________ P a g e | 23