Chapter 5
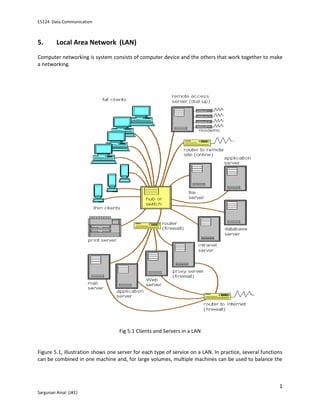
- 1. E5124 Data Communication 5. Local Area Network (LAN) Computer networking is system consists of computer device and the others that work together to make a networking. Fig 5.1 Clients and Servers in a LAN Figure 5.1, illustration shows one server for each type of service on a LAN. In practice, several functions can be combined in one machine and, for large volumes, multiple machines can be used to balance the 1 Sargunan Ainal (JKE)
- 2. E5124 Data Communication traffic for the same service. For example, a large Internet Web site is often made up of several Web servers. A Local Area Network (LAN) is a network that is confined to a relatively small area. It is generally limited to a geographic area such as a writing lab, school, or building. Computers connected to a network are broadly categorized as servers or workstations. Servers are generally not used by humans directly, but rather run continuously to provide "services" to the other computers (and their human users) on the network. Services provided can include printing and faxing, software hosting, file storage and sharing, messaging, data storage and retrieval, complete access control (security) for the network's resources, and many others. Workstations are called such because they typically do have a human user which interacts with the network through them. Workstations were traditionally considered a desktop, consisting of a computer, keyboard, display, and mouse, or a laptop, with with integrated keyboard, display, and touchpad. With the advent of the tablet computer, and the touch screen devices such as iPad and iPhone, our definition of workstation is quickly evolving to include those devices, because of their ability to interact with the network and utilize network services. Servers tend to be more powerful than workstations, although configurations are guided by needs. For example, a group of servers might be located in a secure area, away from humans, and only accessed through the network. In such cases, it would be common for the servers to operate without a dedicated display or keyboard. However, the size and speed of the server's processor(s), hard drive, and main memory might add dramatically to the cost of the system. On the other hand, a workstation might not need as much storage or working memory, but might require an expensive display to accommodate the needs of its user. Every computer on a network should be appropriately configured for its use. On a single LAN, computers and servers may be connected by cables or wirelessly. Wireless access to a wired network is made possible by wireless access points (WAPs). These WAP devices provide a bridge between computers and networks. A typical WAP might have the theoretical capacity to connect hundreds or even thousands of wireless users to a network, although practical capacity might be far less. Nearly always servers will be connected by cables to the network, because the cable connections remain the fastest. Workstations which are stationary (desktops) are also usually connected by a cable to the network, although the cost of wireless adapters has dropped to the point that, when installing workstations in an existing facility with inadequate wiring, it can be easier and less expensive to use wireless for a desktop. 5.1 Topology in Network Design Think of a topology as a network's virtual shape or structure. This shape does not necessarily correspond to the actual physical layout of the devices on the network. For example, the computers on a home LAN may be arranged in a circle in a family room, but it would be highly unlikely to find a ring topology there. 2 Sargunan Ainal (JKE)
- 3. E5124 Data Communication Fig 5.2 LAN connection with various medium like gateway, router, hub, switch, bridge, repeater Network topologies are categorized into the following basic types: Bus Ring Star Tree Mesh The physical topology of a network is the actual geometric layout of workstations. There are several common physical topologies, as described below and as shown in Fig 5.3 3 Sargunan Ainal (JKE)
- 4. E5124 Data Communication Fig 5.3 Various topoloies More complex networks can be built as hybrids of two or more of the above basic topologies. 5.1.1 Bus Topology Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message. Ethernet bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. 10Base-2 ("ThinNet") and 10Base-5 ("ThickNet") both were popular Ethernet cabling options many years ago for bus topologies. However, bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable, refer Fig 5.4 4 Sargunan Ainal (JKE)
- 5. E5124 Data Communication Fig 5.4 Bus Topology Fig 5.5 Ring Topology 5.1.2 Ring Topology In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network. To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses. 5.1.3. Star Topology Many home networks use the star topology. A star network features a central connection point called a "hub" that may be a hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet. Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however, the entire network also fails.) Fig 5.6 Star Topology Fig 5.7 Mesh Topology 5 Sargunan Ainal (JKE)
- 6. E5124 Data Communication 5.1.4 Mesh Topology Mesh topologies involve the concept of routes. Unlike each of the previous topologies, messages sent on a mesh network can take any of several possible paths from source to destination. (Recall that even in a ring, although two cable paths exist, messages can only travel in one direction.) Some WANs, most notably the Internet, employ mesh routing. A mesh network in which every device connects to every other is called a full mesh. As shown in Fig 5.7, partial mesh networks also exist in which some devices connect only indirectly to others. 5.1.5 Tree Topology Tree topologies integrate multiple star topologies together onto a bus. In its simplest form, only hub devices connect directly to the tree bus, and each hub functions as the "root" of a tree of devices. This bus/star hybrid approach supports future expandability of the network much better than a bus (limited in the number of devices due to the broadcast traffic it generates) or a star (limited by the number of hub connection points) alone. Fig 5.8 Tree Topology 5.2 Signal Transmission Two techniques can be used to transmit the encoded signals over cable baseband and broadband transmission. 5.2.1 Baseband Transmission Baseband systems use digital signaling over a single frequency. Signals flow in the form of discrete pulses of electricity or light. With baseband transmission, the entire communication channel capacity is used to transmit a single data signal. The digital signal uses the complete bandwidth of the cable, which constitutes a single channel. A cable's total bandwidth is the difference between the highest and lowest frequencies that are carried over that cable. 6 Sargunan Ainal (JKE)
- 7. E5124 Data Communication Each device on a baseband network transmits bidirectional, and some can transmit and receive at the same time. Figure 5.9: Baseband transmission showing bidirectional digital wave As the signal travels along the network cable, it gradually decreases in strength and can become distorted. If the cable length is too long, the result is a signal that is weak or distorted. The received signal may be unrecognizable or misinterpreted. As a safeguard, baseband systems sometimes use repeaters to receive an incoming signal and retransmit it at its original strength and definition to increase the practical length of a cable. 5.2.2 Broadband Transmission Broadband systems use analog signaling and a range of frequencies. With analog transmission, the signals are continuous and non-discrete. Signals flow across the physical medium in the form of electromagnetic or optical waves. With broadband transmission, signal flow is unidirectional. Figure 5.10: Broadband transmission showing unidirectional analog wave If sufficient total bandwidth is available, multiple analog transmission systems such as cable television and network transmissions can be supported simultaneously on the same cable. Each transmission system is allocated a part of the total bandwidth. All devices associated with a given transmission system, such as all computers using a LAN cable, must then be tuned so that they use only the frequencies that are within the allocated range. While baseband systems use repeaters, broadband systems use amplifiers to regenerate analog signals at their original strength. Because of broadband transmission signal flow is unidirectional, there must be two paths for data flow in order for a signal to reach all devices. There are two common ways to do this: Mid-split broadband configuration divides the bandwidth into two channels, each using a different frequency or range of frequencies. One channel is used to transmit signals, the other to receive signals. In dual-cable broadband configuration, each device is attached to two cables. One cable is used to send and the other is used to receive. 7 Sargunan Ainal (JKE)
- 8. E5124 Data Communication 5.3 Carrier Sense Multiple Access (CSMA) CSMA is a network access method used on shared network topologies such as Ethernet to control access to the network. Devices attached to the network cable listen (carrier sense) before transmitting. If the channel is in use, devices wait before transmitting. MA (multiple access) indicates that many devices can connect to and share the same network. All devices have equal access to use the network when it is clear. Even though devices attempt to sense whether the network is in use, there is a good chance that two stations will attempt to access it at the same time. On large networks, the transmission time between one end of the cable and another is enough that one station may access the cable even though another has already just accessed it. There are two methods for avoiding these so-called collisions, listed here: CSMA/CD (carrier sense multiple access/collision detection) CD (collision detection) defines what happens when two devices sense a clear channel, then attempt to transmit at the same time. A collision occurs, and both devices stop transmission, wait for a random amount of time, then retransmit. This is the technique used to access the 802.3 Ethernet network channel. This method handles collisions as they occur, but if the bus is constantly busy, collisions can occur so often that performance drops drastically. It is estimated that network traffic must be less than 40 percent of the bus capacity for the network to operate efficiently. If distances are long, time lags occur that may result in inappropriate carrier sensing, and hence collisions. Fig 5.11 CSMA/CD medium access Base on Fig 5.11, Here are the rules that make CSMA/CD work. All computers stay quiet if another computer is talking. Any computer that wants to talk must listen to see if the network is silent, they must wait a predetermined time based on the time it takes for a message to travel the length of the network. If after waiting, if the network is silent, then a computer may talk. If two computers wait and both talk together, a collision is said to occur. 8 Sargunan Ainal (JKE)
- 9. E5124 Data Communication Other computers recognize the collision and re-enforce it by talking. Then all computers stop talking. Each computer picks a random number and counts backward to zero. Hopefully one of the two computers that wanted to talk finishes first and begins talking causing the other computers to wait. CSMA/CA (carrier sense multiple access/collision avoidance). In CA (collision avoidance), collisions are avoided because each node signals its intent to transmit before actually doing so. This method is not popular because it requires excessive overhead that reduces performance. 5.4 Token Passing Token passing is an orderly access method and is shown in Fig5.12. Each workstation passes on the opportunity to transmit to its closest neighbor until a station is found with a message to send. This permission to transmit is called a token. When a workstation with data to send is handed a token, part of the token is changed, indicating it is carrying a message, and then data is transmitted with the token. The token is then passed around the network, and every station checks whether the message is intended for it. The receiving station copies the message from the token, but then passes the unchanged token along the network. When the transmitting station receives the same token, it knows the message has been passed around the network. The transmitting station erases the message and puts the empty token back into circulation on the network. The amount of information that maybe transmitted during possession of the token is limited so that all workstations can share the cable equally. Network PC Server 1 Token is here PC Nodes PC 5 Nodes PC 2 PC 5 data to send has data to 2 to node PC1 send to node PC4 PC PC 4 3 Fig 5.12 A ring network using the token passing access method 9 Sargunan Ainal (JKE)
- 10. E5124 Data Communication 5.5 Differences between LAN, WAN and MAN LAN A group of computers that share a common connection and are usually in a small area or even in the same building. For example an office or home network. They are usually connected by Ethernet cables and have high speed connections. If it was a wireless setup it would be called a WLAN, which would have a lower connection speed. MAN (Metropolitan Area Network) This is a larger network that connects computer users in a particular geographic area or region. For example a large university may have a network so large that it may be classified as a MAN. The MAN network usually exist to provide connectivity to local ISPs, cable tv, or large corporations. It is far larger than a LAN and smaller than a WAN. Also large cities like London and Sydney, Australia have metropolitan area networks. WAN (Wide Area Network) This is the largest network and can interconnect networks throughout the world and is not restricted to a geographical location. The Internet is an example of a worldwide public WAN. Most WANs exist to connect LANs that are not in the same geographical area. This technology is high speed and very expensive to setup. Fig 5.13 View of LAN, MAN and WAN by area coverage 10 Sargunan Ainal (JKE)