Detecting In-Situ Identity Fraud on Social Network Services: A Case Study on Facebook
•
1 j'aime•2,363 vues
In this paper, we propose to use a continuous authentication approach to detect the in-situ identity fraud incidents, which occur when the attackers use the same devices and IP addresses as the victims. Using Facebook as a case study, we show that it is possible to detect such incidents by analyzing SNS users’ browsing behavior. Our experiment results demonstrate that the approach can achieve reasonable accuracy given a few minutes of observation time.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTION

A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTIONWright State University, Dayton, OH, USA
Contenu connexe
Similaire à Detecting In-Situ Identity Fraud on Social Network Services: A Case Study on Facebook
A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTION

A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTIONWright State University, Dayton, OH, USA
Similaire à Detecting In-Situ Identity Fraud on Social Network Services: A Case Study on Facebook (20)
IRJET- Enhancing NLP Techniques for Fake Review Detection

IRJET- Enhancing NLP Techniques for Fake Review Detection
Credential Harvesting Using Man in the Middle Attack via Social Engineering

Credential Harvesting Using Man in the Middle Attack via Social Engineering
Credential Harvesting Using Man in the Middle Attack via Social Engineering

Credential Harvesting Using Man in the Middle Attack via Social Engineering
Trust based video management framework for social multimedia networks

Trust based video management framework for social multimedia networks
A Study on Credit Card Fraud Detection using Machine Learning

A Study on Credit Card Fraud Detection using Machine Learning
Websites using touchless interaction having graphical

Websites using touchless interaction having graphical
User service-rating-prediction-by-exploring social users rating Behaviours

User service-rating-prediction-by-exploring social users rating Behaviours
IRJET- Honeywords: A New Approach for Enhancing Security

IRJET- Honeywords: A New Approach for Enhancing Security
A SUPERVISED MACHINE LEARNING APPROACH USING K-NEAREST NEIGHBOR ALGORITHM TO ...

A SUPERVISED MACHINE LEARNING APPROACH USING K-NEAREST NEIGHBOR ALGORITHM TO ...
A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTION

A SOFT COMPUTING APPROACH FOR BENIGN AND MALICIOUS WEB ROBOT DETECTION
IRJET- Big Data Driven Information Diffusion Analytics and Control on Social ...

IRJET- Big Data Driven Information Diffusion Analytics and Control on Social ...
Webinar: Everyone cares about sample quality but not everyone values it!

Webinar: Everyone cares about sample quality but not everyone values it!
Webinar: Everyone cares about sample quality but not everyone values it!

Webinar: Everyone cares about sample quality but not everyone values it!
IRJET-Gaussian Filter based Biometric System Security Enhancement

IRJET-Gaussian Filter based Biometric System Security Enhancement
IEEE - 2016 Active Research Projects - 1 Crore Projects

IEEE - 2016 Active Research Projects - 1 Crore Projects
IRJET - Secure Banking Application with Image and GPS Location

IRJET - Secure Banking Application with Image and GPS Location
Prediction Techniques in Internet of Things (IoT) Environment: A Comparative ...

Prediction Techniques in Internet of Things (IoT) Environment: A Comparative ...
Plus de Academia Sinica
Plus de Academia Sinica (20)
Computational Social Science:The Collaborative Futures of Big Data, Computer ...

Computational Social Science:The Collaborative Futures of Big Data, Computer ...
Cloud Gaming Onward: Research Opportunities and Outlook

Cloud Gaming Onward: Research Opportunities and Outlook
Quantifying User Satisfaction in Mobile Cloud Games

Quantifying User Satisfaction in Mobile Cloud Games
Understanding The Performance of Thin-Client Gaming

Understanding The Performance of Thin-Client Gaming
Quantifying QoS Requirements of Network Services: A Cheat-Proof Framework

Quantifying QoS Requirements of Network Services: A Cheat-Proof Framework
Online Game QoE Evaluation using Paired Comparisons

Online Game QoE Evaluation using Paired Comparisons
Are All Games Equally Cloud-Gaming-Friendly? An Electromyographic Approach

Are All Games Equally Cloud-Gaming-Friendly? An Electromyographic Approach
Identifying MMORPG Bots: A Traffic Analysis Approach

Identifying MMORPG Bots: A Traffic Analysis Approach
Toward an Understanding of the Processing Delay of Peer-to-Peer Relay Nodes

Toward an Understanding of the Processing Delay of Peer-to-Peer Relay Nodes
Inferring Speech Activity from Encrypted Skype Traffic

Inferring Speech Activity from Encrypted Skype Traffic
Improving Reliability of Web 2.0-based Rating Systems Using Per-user Trustiness

Improving Reliability of Web 2.0-based Rating Systems Using Per-user Trustiness
A Collusion-Resistant Automation Scheme for Social Moderation Systems

A Collusion-Resistant Automation Scheme for Social Moderation Systems
Tuning Skype’s Redundancy Control Algorithm for User Satisfaction

Tuning Skype’s Redundancy Control Algorithm for User Satisfaction
Network Game Design: Hints and Implications of Player Interaction

Network Game Design: Hints and Implications of Player Interaction
Dernier
Dernier (20)
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
The Evolution of Money: Digital Transformation and CBDCs in Central Banking

The Evolution of Money: Digital Transformation and CBDCs in Central Banking
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Detecting In-Situ Identity Fraud on Social Network Services: A Case Study on Facebook
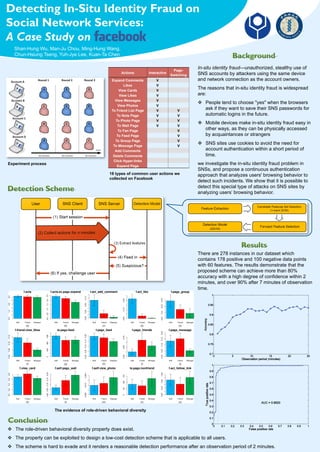
- 1. Detecting In-Situ Identity Fraud on Social Network Services: A Case Study on In-situ identity fraud—unauthorized, stealthy use of SNS accounts by attackers using the same device and network connection as the account owners. The reasons that in-situ identity fraud is widespread are: v People tend to choose "yes" when the browsers ask if they want to save their SNS passwords for automatic logins in the future. v Mobile devices make in-situ identity fraud easy in other ways, as they can be physically accessed by acquaintances or strangers v SNS sites use cookies to avoid the need for account authentication within a short period of time. we investigate the in-situ identity fraud problem in SNSs, and propose a continuous authentication approach that analyzes users' browsing behavior to detect such incidents. We show that it is possible to detect this special type of attacks on SNS sites by analyzing users’ browsing behavior. There are 278 instances in our dataset which contains 178 positive and 100 negative data points with 60 features. The results demonstrate that the proposed scheme can achieve more than 80% accuracy with a high degree of confidence within 2 minutes, and over 90% after 7 minutes of observation time. v The role-driven behavioral diversity property does exist. v The property can be exploited to design a low-cost detection scheme that is applicable to all users. v The scheme is hard to evade and it renders a reasonable detection performance after an observation period of 2 minutes. Shan-Hung Wu, Man-Ju Chou, Ming-Hung Wang, Chun-Hsiung Tseng, Yuh-Jye Lee, Kuan-Ta Chen Actions Interactive Page- Switching Expand Comments V Likes V View Cards V View Likes V View Messages V View Photos V To Friend List Page V V To Note Page V V To Photo Page V V To Wall Page V V To Fan Page V To Feed Page V To Group Page V To Message Page V Add Comments Delete Comments Click Hyper-links Expand Page The evidence of role-driven behavioral diversity Experiment process 18 types of common user actions we collected on Facebook
