Swot 1
•Télécharger en tant que PPTX, PDF•
3 j'aime•1,580 vues
Rough slides for SWOT analysis
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
Microsoft Intune - Empowering Enterprise Mobility - Presented by Atidan 

Microsoft Intune - Empowering Enterprise Mobility - Presented by Atidan
Best practices for building network operations center

Best practices for building network operations center
Protect your applications from DDoS/BOT & Advanced Attacks

Protect your applications from DDoS/BOT & Advanced Attacks
Chris Munns, DevOps @ Amazon: Microservices, 2 Pizza Teams, & 50 Million Depl...

Chris Munns, DevOps @ Amazon: Microservices, 2 Pizza Teams, & 50 Million Depl...
Using Models for Incident, Change, Problem and Request Fulfillment Management

Using Models for Incident, Change, Problem and Request Fulfillment Management
Similaire à Swot 1
According to EMA research, 79% of organizations consider privileged access management (PAM) to be very important or critical to their business operations. However, 76% of organizations experience significant privileged access policy violations each year, exposing the most sensitive business information and IT resources to extreme risks of exposure.
These slides—based on the webinar from EMA Research and Remediant—provide actionable guidance on how to advance your PAM implementations regardless of where you are currently in your security management journey.
Actionable Guidance to Succeed in Enterprise-Class Privileged Access Management

Actionable Guidance to Succeed in Enterprise-Class Privileged Access ManagementEnterprise Management Associates
Similaire à Swot 1 (20)
The Keys To A Successful Identity And Access Management Program: How Does You...

The Keys To A Successful Identity And Access Management Program: How Does You...
AgileCville: How to sell a traditional client on an Agile project plan

AgileCville: How to sell a traditional client on an Agile project plan
Identity Management: What Solution is Right for You?

Identity Management: What Solution is Right for You?
Giving your AppSec program the edge - using OpenSAMM for benchmarking and sof...

Giving your AppSec program the edge - using OpenSAMM for benchmarking and sof...
Actionable Guidance to Succeed in Enterprise-Class Privileged Access Management

Actionable Guidance to Succeed in Enterprise-Class Privileged Access Management
Role Discovery and RBAC Design: A Case Study with IBM Role and Policy Modeler

Role Discovery and RBAC Design: A Case Study with IBM Role and Policy Modeler
Software Outsourcing: Outsource Your Project or Build a Team

Software Outsourcing: Outsource Your Project or Build a Team
Dernier
Dernier (20)
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Swot 1
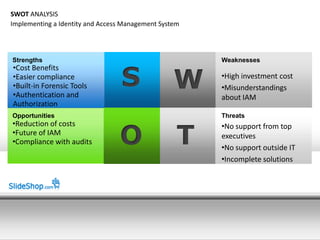
- 1. SWOT ANALYSIS Implementing a Identity and Access Management System Strengths Weaknesses S W •Cost Benefits •Easier compliance •High investment cost •Built-in Forensic Tools •Misunderstandings •Authentication and about IAM Authorization Opportunities Threats O T •Reduction of costs •No support from top •Future of IAM executives •Compliance with audits •No support outside IT •Incomplete solutions
- 2. SWOT ANALYSIS Strengths Current strengths of Goals and project IAM plan: strengths •Identity management processes which become automated offer cost benefits -Implement automated IAM • Example: Password resets system to reduce risk and costs cost time and resources at help desk •Create a roadmap and vision •Inbuilt forensic tools •Design architecture of system • Need to find where issue and select components originated during a breach or leak, this is difficult with •Develop release schedule and manual IAM system timeline •Authorization and Authentication • Prove that an individual holds the identity that she/he claims to hold.
- 3. SWOT ANALYSIS Weaknesses Current weaknesses However: •"Almost 60% of respondents say their High investment costs companies are unable to effectively focus IAM controls on areas of greatest • Many of these business risk" systems do have a high initial cost •"51% Take a reactive approach to security issues" •There are several myths which surround IAM •"58% of companies studied still rely systems on manual controls to audit and control user access to critical • “IAM systems can enterprise systems and data do everything”, and resources, leaving networks open to privacy breaches, failed audits, and “IAM is a potential fraud or misuse of data“ technology only solution” •http://www.informationweek.com/ne ws/show/showArticle.jhtml?articleID= 197800526
- 4. SWOT ANALYSIS Opportunities Current opportunities Goals and project plan: •Reduction of costs over time Opportunities • Maintaining current tools •Implementing a solid for IM will increase in cost I&AM solution will reduce over time risks and overall costs • Implementing IAM system will reduce costs over time •There are many resources •The future of IAM and IAM solutions • IAM tools will become available from a variety of easier to companies which can use, maintain, and usually be mixed and programs will become matched and worked with consolodated to find the perfect solution •Compliance with audits will be for this company much easier
- 5. SWOT ANALYSIS Threats Current threats Goals and project plan: threats •No support from top executives • Lack of support from top •Gain the support for implementing a executives makes a solid successful IAM system throughout the IAM soluation almost orgianzation impossible •No support outside IT •Make sure the entire system is • Some believe an IAM system planned and executed in a way so the is only for the IT future vision becomes a reality department. An IAM solution hasa company-wide •Make sure the correct systems are architecture purchased and put in place to make •Incomplete solutions the investment match up with cost- • When only certain pieces of benefit analysis a system are used, the system is not worth the investment usually
- 6. SWOT ANALYSIS Summary SWOT summary