2 1. introduction of digital laws in china
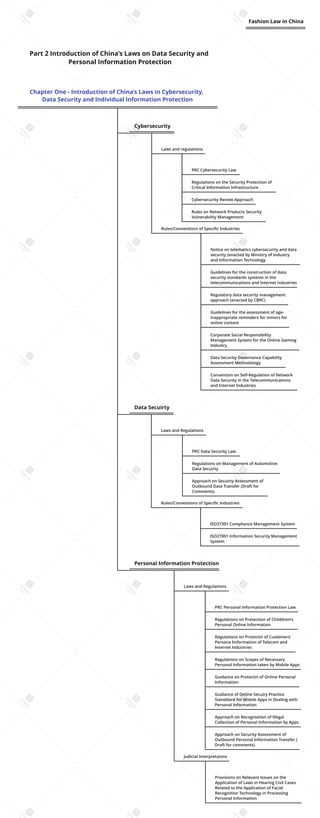
- 1. Chapter One - Introduction of China’s Laws in Cybersecurity, Data Security and Individual Information Protection Cybersecurity Laws and regulations PRC Cybersecurity Law Regulations on the Security Protection of Critical Information Infrastructure Cybersecurity Review Approach Rules on Network Products Security Vulnerability Management Rules/Conventions of Specific Industries Notice on telematics cybersecuirty and data security (enacted by Ministry of Industry and Information Technology Guidelines for the construction of data security standards systems in the telecommunications and Internet industries Regulatory data security management approach (enacted by CBRC) Guidelines for the assessment of age- inappropriate reminders for minors for online content Corporate Social Responsibility Management System for the Online Gaming Industry Data Security Governance Capability Assessment Methodology Convention on Self-Regulation of Network Data Security in the Telecommunications and Internet Industries Data Secuirty Laws and Regulations PRC Data Security Law Regulations on Management of Automotive Data Secuirty Approach on Secuirty Assessment of Outbound Data Transfer (Draft for Comments) Rules/Conventions of Specific Industries ISO37301 Compliance Management System ISO27001 Information Security Management System Personal Information Protection Laws and Regulations PRC Personal Information Protection Law Regulations on Protection of Childdren’s Personal Online Information Regulations on Protectin of Custemers’ Persona linformation of Telecom and Internet Industries Regulations on Scopes of Necessary Personal Information taken by Mobile Apps Guidance on Protectin of Online Personal Information Gudiance of Online Secuiry Practice Standdard for Mobile Apps in Dealing with Personal Information Approach on Recogniation of Illegal Collection of Personal Information by Apps Approach on Security Assessment of Outbound Personal Information Transfer ( Draft for comments) Judicial Interpretaions Provisions on Relevant Issues on the Application of Laws in Hearing Civil Cases Related to the Application of Facial Recognition Technology in Processing Personal Information Part 2 Introduction of China’s Laws on Data Security and Personal Information Protection Fashion Law in China