Small Business Guide to Information Security
•
1 j'aime•1,797 vues
http://www.choosewhat.com/ (ChooseWhat.com) brings small business owners and entrepreneurs a Step-By-Step Guide to Keeping Your Sensitive Information Secure. Embed this on your own blog, share it with your social network or let us know if we can help!
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
DSS ITSEC 2013 Conference 07.11.2013 - HeadTechnology - IT security trends 2014

DSS ITSEC 2013 Conference 07.11.2013 - HeadTechnology - IT security trends 2014
ISC(2) Security Briefing Part 2 - CASBs: Real-world use cases

ISC(2) Security Briefing Part 2 - CASBs: Real-world use cases
The security story behind critical industrial networks 

The security story behind critical industrial networks
The Business Case for Enterprise Endpoint Protection: Can You Afford Not To?

The Business Case for Enterprise Endpoint Protection: Can You Afford Not To?
odix introduction ransomware prevention in WFH reality 2020

odix introduction ransomware prevention in WFH reality 2020
Next-Generation Cybersecurity for the Globally Connected Enterprise with Telos

Next-Generation Cybersecurity for the Globally Connected Enterprise with Telos
En vedette
En vedette (10)
Business continuity & disaster recovery planning (BCP & DRP)

Business continuity & disaster recovery planning (BCP & DRP)
Similaire à Small Business Guide to Information Security
Mobile Device Security by Michael Gong, Jake Kreider, Chris Lugo, Kwame Osafoh-Kantanka Mobile Device Security by Michael Gong, Jake Kreider, Chris Lugo, Kwame Osaf...

Mobile Device Security by Michael Gong, Jake Kreider, Chris Lugo, Kwame Osaf...Information Security Awareness Group
Similaire à Small Business Guide to Information Security (20)
Lock it or Lose It: Why Every Company Should be Concerned About Data Security

Lock it or Lose It: Why Every Company Should be Concerned About Data Security
Essential Layers of IBM i Security: Physical Security

Essential Layers of IBM i Security: Physical Security
Mobile Device Security by Michael Gong, Jake Kreider, Chris Lugo, Kwame Osaf...

Mobile Device Security by Michael Gong, Jake Kreider, Chris Lugo, Kwame Osaf...
3 ways to secure your law firm’s information and reputation

3 ways to secure your law firm’s information and reputation
Wfh security risks - Ed Adams, President, Security Innovation

Wfh security risks - Ed Adams, President, Security Innovation
apsec 7 Golden Rules Data Leakage Prevention / DLP

apsec 7 Golden Rules Data Leakage Prevention / DLP
Avoiding Common Security Breaches & HIPAA Violations

Avoiding Common Security Breaches & HIPAA Violations
Protect Sensitive Data on Your IBM i (Social Distance Your IBM i/AS400)

Protect Sensitive Data on Your IBM i (Social Distance Your IBM i/AS400)
Security Awareness Training - For Companies With Access to NYS "Sensitive" In...

Security Awareness Training - For Companies With Access to NYS "Sensitive" In...
Protecting Your Business from Unauthorized IBM i Access

Protecting Your Business from Unauthorized IBM i Access
Office 365 Security Features That Nonprofits Should Know and Use

Office 365 Security Features That Nonprofits Should Know and Use
Mobile_Forensics- General Introduction & Software.pptx

Mobile_Forensics- General Introduction & Software.pptx
Dernier
VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS Live
Booking Contact Details :-
WhatsApp Chat :- [+91-9999965857 ]
The Best Call Girls Delhi At Your Service
Russian Call Girls Delhi Doing anything intimate with can be a wonderful way to unwind from life's stresses, while having some fun. These girls specialize in providing sexual pleasure that will satisfy your fetishes; from tease and seduce their clients to keeping it all confidential - these services are also available both install and outcall, making them great additions for parties or business events alike. Their expert sex skills include deep penetration, oral sex, cum eating and cum eating - always respecting your wishes as part of the experience
(07-May-2024(PSS)VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...

VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Saudi Arabia [ Abortion pills) Jeddah/riaydh/dammam/++918133066128☎️] cytotec tablets uses abortion pills 💊💊 How effective is the abortion pill? 💊💊 +918133066128) "Abortion pills in Jeddah" how to get cytotec tablets in Riyadh " Abortion pills in dammam*💊💊 The abortion pill is very effective. If you’re taking mifepristone and misoprostol, it depends on how far along the pregnancy is, and how many doses of medicine you take:💊💊 +918133066128) how to buy cytotec pills
At 8 weeks pregnant or less, it works about 94-98% of the time. +918133066128[ 💊💊💊 At 8-9 weeks pregnant, it works about 94-96% of the time. +918133066128) At 9-10 weeks pregnant, it works about 91-93% of the time. +918133066128)💊💊 If you take an extra dose of misoprostol, it works about 99% of the time. At 10-11 weeks pregnant, it works about 87% of the time. +918133066128) If you take an extra dose of misoprostol, it works about 98% of the time. In general, taking both mifepristone and+918133066128 misoprostol works a bit better than taking misoprostol only. +918133066128 Taking misoprostol alone works to end the+918133066128 pregnancy about 85-95% of the time — depending on how far along the+918133066128 pregnancy is and how you take the medicine. +918133066128 The abortion pill usually works, but if it doesn’t, you can take more medicine or have an in-clinic abortion. +918133066128 When can I take the abortion pill?+918133066128 In general, you can have a medication abortion up to 77 days (11 weeks)+918133066128 after the first day of your last period. If it’s been 78 days or more since the first day of your last+918133066128 period, you can have an in-clinic abortion to end your pregnancy.+918133066128
Why do people choose the abortion pill? Which kind of abortion you choose all depends on your personal+918133066128 preference and situation. With+918133066128 medication+918133066128 abortion, some people like that you don’t need to have a procedure in a doctor’s office. You can have your medication abortion on your own+918133066128 schedule, at home or in another comfortable place that you choose.+918133066128 You get to decide who you want to be with during your abortion, or you can go it alone. Because+918133066128 medication abortion is similar to a miscarriage, many people feel like it’s more “natural” and less invasive. And some+918133066128 people may not have an in-clinic abortion provider close by, so abortion pills are more available to+918133066128 them. +918133066128 Your doctor, nurse, or health center staff can help you decide which kind of abortion is best for you. +918133066128 More questions from patients: Saudi Arabia+918133066128 CYTOTEC Misoprostol Tablets. Misoprostol is a medication that can prevent stomach ulcers if you also take NSAID medications. It reduces the amount of acid in your stomach, which protects your stomach lining. The brand name of this medication is Cytotec®.+918133066128) Unwanted Kit is a combination of two medicines, ounwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE AbudhabiAbortion pills in Kuwait Cytotec pills in Kuwait
Dernier (20)
B.COM Unit – 4 ( CORPORATE SOCIAL RESPONSIBILITY ( CSR ).pptx

B.COM Unit – 4 ( CORPORATE SOCIAL RESPONSIBILITY ( CSR ).pptx
BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL

BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL
VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...

VVVIP Call Girls In Greater Kailash ➡️ Delhi ➡️ 9999965857 🚀 No Advance 24HRS...
Value Proposition canvas- Customer needs and pains

Value Proposition canvas- Customer needs and pains
Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...

Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...
Mysore Call Girls 8617370543 WhatsApp Number 24x7 Best Services

Mysore Call Girls 8617370543 WhatsApp Number 24x7 Best Services
👉Chandigarh Call Girls 👉9878799926👉Just Call👉Chandigarh Call Girl In Chandiga...

👉Chandigarh Call Girls 👉9878799926👉Just Call👉Chandigarh Call Girl In Chandiga...
Call Girls Kengeri Satellite Town Just Call 👗 7737669865 👗 Top Class Call Gir...

Call Girls Kengeri Satellite Town Just Call 👗 7737669865 👗 Top Class Call Gir...
Call Girls Service In Old Town Dubai ((0551707352)) Old Town Dubai Call Girl ...

Call Girls Service In Old Town Dubai ((0551707352)) Old Town Dubai Call Girl ...
Call Girls Jp Nagar Just Call 👗 7737669865 👗 Top Class Call Girl Service Bang...

Call Girls Jp Nagar Just Call 👗 7737669865 👗 Top Class Call Girl Service Bang...
Call Girls From Pari Chowk Greater Noida ❤️8448577510 ⊹Best Escorts Service I...

Call Girls From Pari Chowk Greater Noida ❤️8448577510 ⊹Best Escorts Service I...
Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876

Call Girls in Delhi, Escort Service Available 24x7 in Delhi 959961-/-3876
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
unwanted pregnancy Kit [+918133066128] Abortion Pills IN Dubai UAE Abudhabi
Call Girls Hebbal Just Call 👗 7737669865 👗 Top Class Call Girl Service Bangalore

Call Girls Hebbal Just Call 👗 7737669865 👗 Top Class Call Girl Service Bangalore
Insurers' journeys to build a mastery in the IoT usage

Insurers' journeys to build a mastery in the IoT usage
Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...

Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...
Small Business Guide to Information Security
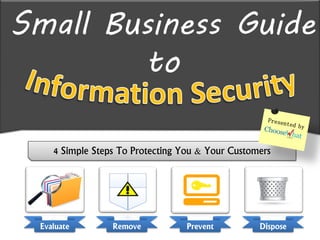
- 1. Small Business Guide to 4 Simple Steps To Protecting You & Your Customers Evaluate Remove Prevent Dispose
- 2. EvaluateYour Company’s Assets & Identify Sensitive Information Step1 Develop a list of physical and digital assets located within each room of your company *Don’t forget storage, equipment, software & networks for each room Treat each digital device as an “office room” Take inventory of all personal and sensitive information stored or transmitted through these devices. Answer the following questions for each piece of office equipment:
- 3. EvaluateInformation Security Questionnaire – Digital Asset Evaluation Step1
- 4. RemoveAll identified security threats & unsecure practices Step2 Review your physical & digital asset log to identify sensitive data you do NOT need Only request sensitive data on the LAST step of transactions *Financial data should only be requested for processing payment or tax documents. NEVER include the expiration date or more than 5 digits on a sales receipt All online transactions or sharing of sensitive data should be done on a Secure Sockets Layer (SSL) *See final slide of Small Business Guide for secure payroll and ecommerce software
- 5. PreventFuture Security Breaches by Addressing Digital Security Step 3 Take inventory of new IT equipment that collects sensitive data *Log each VIN # and check it periodically to ensure it has not been switched Identify all connections to computers, servers & IT equipment that may contain sensitive data *iPhone’s, Dropbox accounts, online fax storage, digital copiers, etc. Do NOT email sensitive data, use an online fax service *Faxing is the most secure way to transfer sensitive information, although fax machines are built with an internal hard drive that is often hacked when a company disposes of it. Use a Password Management Service Don’t store sensitive data on electronic devices that are easily stolen or lost *If needed, use an online backup service with an encryption & auto-destroy function
- 6. PreventFuture Security Breaches by Addressing Physical Security Step 3 Define employee guidelines, responsibilities & restrictions upon new employee hire & in company handbook. Make sure your employees log-off their computers and lock all cabinet doors prior to leaving each day. *iPhone’s, Dropbox accounts, online fax storage, digital copiers, etc. Do NOT email sensitive data, use an online fax service. *Faxing is the most secure way to transfer sensitive information, although fax machines are built with an internal hard drive that is often hacked when a company disposes of it. Lock all file cabinets with sensitive information & start a “sign in/out” system each time they are accessed. *This should be true of off-site storage facilities as well.
- 7. DisposeOf any and ALL sensitive information Step 4 Make shredders available throughout the office, especially around mail areas, copy or fax machines *Do not create a “To Be Shredded” box, this will only increase your risk Erase electronic devices COMPLETELY before removal. *There are software options available to clean all electronics periodically or wipe completely Mail centers and fax machines should be placed in private area, AWAY from foot traffic *According to a GFI study, 49% of employees claimed to have seen a paper fax that was not intended for them
- 8. Security Software Recommendations Explain this point in a few sentences. An infographic doesn’t necessarily mean you aren’t allowed to use words. Secure Online Shopping & Payroll • Intuit GoPayment • Intuit Online Payroll Password Management • Lastpass • Dashlane Secure Online Backup • iDrive • Carbonite Online Backup External Hard Drive with “Auto Destroy” Feature • Apricorn Aegis Padlock 1 TB USB 3.0 256-bit AES XTS Hardware Encrypted Portable External Hard Drive • Apricorn Aegis Padlock 500 GB USB 2.0 256-bit Encrypted Portable External Hard Drive • Apricorn Aegis Secure Key FIPS Validated 16 GB USB 2.0 256-bit AES-CBC Encrypted Flash Drive Security Software for Portable Electronics • LoJack for Laptops Secure Online Fax Plans • MetroFax Essential • Nextiva Single User • eFax – eFax Plus
- 9. Sources Explain this point in a few sentences. An infographic doesn’t necessarily mean you aren’t allowed to use words. ChooseWhat.com would like to thank the following websites for their help in developing this information security guide. • http://business.ftc.gov/documents/bus75-medical-identity-theft-faq-health-care- health-plan • business.ftc.gov/privacy-and-security • David of FindAFax.com • www.OnGuardOnline.gov • Electronic Code of Federal Regulations • http://business.ftc.gov/documents/bus69-protecting-personal-information-guide- business • http://www.sba.gov/category/navigation-structure/starting-managing- business/managing-business/business-guides-industry • http://business.ftc.gov/privacy-and-security/data-security A detailed version of this guide is available here: http://www.choosewhat.com/starticles/small-business-security-essentials
- 10. Sharing is Caring!! Brought to you by:
