2015 Global Threat Intelligence Report
•
1 j'aime•781 vues
An analysis of security trends in the Financial Services industry. 56% of attacks originate from IP addresses within the US but attackers could be anywhere in the world.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Key Trends and Opportunities in Business Mobility and Enterprise Communications

Key Trends and Opportunities in Business Mobility and Enterprise CommunicationsRaúl Castañón Martínez
Recommandé
Key Trends and Opportunities in Business Mobility and Enterprise Communications

Key Trends and Opportunities in Business Mobility and Enterprise CommunicationsRaúl Castañón Martínez
Contenu connexe
Tendances
Tendances (20)
7 Best Practices to Protect Critical Business Information [Infographic]![7 Best Practices to Protect Critical Business Information [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![7 Best Practices to Protect Critical Business Information [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
7 Best Practices to Protect Critical Business Information [Infographic]
IDC: Top Five Considerations for Cloud-Based Security

IDC: Top Five Considerations for Cloud-Based Security
Extending applications securely to wireless health workers.

Extending applications securely to wireless health workers.
Changing Your Enterprise Architecture - Mobile is Not an Add-On

Changing Your Enterprise Architecture - Mobile is Not an Add-On
Resilience Engineering as an IT Cultural Discipline

Resilience Engineering as an IT Cultural Discipline
Top 3 Reasons to Deliver Web Apps with Application Virtualization

Top 3 Reasons to Deliver Web Apps with Application Virtualization
Choosing the right network management solution: Increase network visibility t...

Choosing the right network management solution: Increase network visibility t...
10 Reasons to Strengthen Security with App & Desktop Virtualization

10 Reasons to Strengthen Security with App & Desktop Virtualization
Windows Apps on Chromebooks: Deliver a Seamless Experience

Windows Apps on Chromebooks: Deliver a Seamless Experience
Best practices for mobile enterprise security and the importance of endpoint ...

Best practices for mobile enterprise security and the importance of endpoint ...
12 Game Changing Ways to Mobilize Teaching and Learning

12 Game Changing Ways to Mobilize Teaching and Learning
Similaire à 2015 Global Threat Intelligence Report
Similaire à 2015 Global Threat Intelligence Report (20)
2015 Global Threat Intelligence Report - an analysis of global security trends

2015 Global Threat Intelligence Report - an analysis of global security trends
2015 Global Threat Intelligence Report Executive Summary | NTT i3

2015 Global Threat Intelligence Report Executive Summary | NTT i3
Key Findings from the 2015 IBM Cyber Security Intelligence Index

Key Findings from the 2015 IBM Cyber Security Intelligence Index
Future Watch: Cybersecurity market in South Africa 

Future Watch: Cybersecurity market in South Africa
Key Security Insights: Examining 2014 to predict emerging threats 

Key Security Insights: Examining 2014 to predict emerging threats
The Executive's Guide to the 2016 Global Threat Intelligence Report

The Executive's Guide to the 2016 Global Threat Intelligence Report
Combating Cybersecurity Challenges with Advanced Analytics

Combating Cybersecurity Challenges with Advanced Analytics
Top 10 cybersecurity predictions for 2016 by Matthew Rosenquist

Top 10 cybersecurity predictions for 2016 by Matthew Rosenquist
Symantec's Internet Security Threat Report for the Government Sector

Symantec's Internet Security Threat Report for the Government Sector
Plus de DImension Data
Plus de DImension Data (20)
Digital technology revolutionised the viewing experience of the tour de france

Digital technology revolutionised the viewing experience of the tour de france
Creating workspaces for tomorrow at the greatest cycling event in the world

Creating workspaces for tomorrow at the greatest cycling event in the world
Zurich case study how to move a data centre in 8 days

Zurich case study how to move a data centre in 8 days
Zurich case study: Reducing risk for insurance customers

Zurich case study: Reducing risk for insurance customers
High-performance solutions for an international university

High-performance solutions for an international university
How we helped Fujifilm keep its customers' special memories safe

How we helped Fujifilm keep its customers' special memories safe
Dimension Data Department Prime Minister and cabinet G20 case study

Dimension Data Department Prime Minister and cabinet G20 case study
Dimension Data has been recognised as one of only 5 Top Global Top Employers

Dimension Data has been recognised as one of only 5 Top Global Top Employers
Dernier
Dernier (20)
In Sharjah ௵(+971)558539980 *_௵abortion pills now available.

In Sharjah ௵(+971)558539980 *_௵abortion pills now available.
QATAR Pills for Abortion -+971*55*85*39*980-in Dubai. Abu Dhabi.

QATAR Pills for Abortion -+971*55*85*39*980-in Dubai. Abu Dhabi.
20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...

20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...
Explore Dual Citizenship in Africa | Citizenship Benefits & Requirements

Explore Dual Citizenship in Africa | Citizenship Benefits & Requirements
Famous No1 Amil Baba Love marriage Astrologer Specialist Expert In Pakistan a...

Famous No1 Amil Baba Love marriage Astrologer Specialist Expert In Pakistan a...
Black magic specialist in Canada (Kala ilam specialist in UK) Bangali Amil ba...

Black magic specialist in Canada (Kala ilam specialist in UK) Bangali Amil ba...
Famous Kala Jadu, Kala ilam specialist in USA and Bangali Amil baba in Saudi ...

Famous Kala Jadu, Kala ilam specialist in USA and Bangali Amil baba in Saudi ...
Mahendragarh Escorts 🥰 8617370543 Call Girls Offer VIP Hot Girls

Mahendragarh Escorts 🥰 8617370543 Call Girls Offer VIP Hot Girls
Strategic Resources May 2024 Corporate Presentation

Strategic Resources May 2024 Corporate Presentation
Certified Kala Jadu, Black magic specialist in Rawalpindi and Bangali Amil ba...

Certified Kala Jadu, Black magic specialist in Rawalpindi and Bangali Amil ba...
2015 Global Threat Intelligence Report
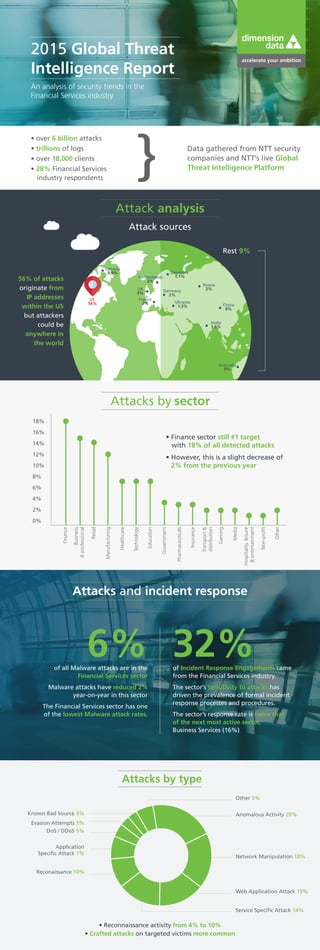
- 1. 2015 Global Threat Intelligence Report An analysis of security trends in the Financial Services industry • over 6 billion attacks • trillions of logs • over 18,000 clients • 28% Financial Services industry respondents Data gathered from NTT security companies and NTT’s live Global Threat Intelligence Platform 56% of attacks originate from IP addresses within the US but attackers could be anywhere in the world Attack analysis Attack sources US 56% China 9% France 2% India 1.5% Germany 2% Netherlands 2% Denmark 1.1% Russia 2% Ukraine 1.3% Canada 0.9% Australia 9% Rest 9% UK 3% Attacks by sector • Finance sector still #1 target with 18% of all detected attacks Finance 0% 2% 4% 8% 10% 12% 14% 16% 18% 6% Business &professional Manufacturing Retail Healthcare Technology Education Government Pharmaceuticals Insurance Transport& distribution Gaming Media Hospitality,leisure &entertainment Non-profit Other • However, this is a slight decrease of 2% from the previous year Attacks and incident response • Reconnaissance activity from 4% to 10% • Crafted attacks on targeted victims more common Other 5% Known Bad Source 3% Evasion Attempts 3% DoS / DDoS 5% Application Specific Attack 7% Reconaissance 10% Anomalous Activity 20% Network Manipulation 18% Web Application Attack 15% Service Specific Attack 14% Attacks by type 6% 32%of all Malware attacks are in the Financial Services sector Malware attacks have reduced 2% year-on-year in this sector The Financial Services sector has one of the lowest Malware attack rates. of Incident Response Engagements came from the Financial Services industry. The sector’s sensitivity to attacks has driven the prevalence of formal incident response processes and procedures. The sector’s response rate is twice that of the next most active sector, Business Services (16%)
- 2. dimensiondata.com/globalthreatreport #GlobalThreatReport Threat intelligence defined 2. Raw information collected based on requirements 3. Information processed exploited 4. Intelligence analysis production 1.Consumer needs, planning, requirements direction 5. Dissemination of product to consumer Attacks have shifted from application to user 7 / 10 vulnerabilities relate to end-user systems Users connected to public network using personal, and often more vulnerable devices End-user exploits spike after weekends / holidays when users reconnect End-user systems often have unpatched vulnerabilities • 76% of vulnerabilities + 2 years old • 9% of those +10 years old The user is the perimeter 7/10 Vulnerabilities targeted in exploit kits Cybercrime is $$ $ $$ $Software exploit kits sold in hacking forums hackers take advantage of unpatched flaws install malicious software on vulnerable devices Increased focus on Adobe Flash since security on Java and Internet Explorer improved in 2014. Java Adobe Acrobat Internet Explorer Adobe Flash Firefox Windows Silverlight Others 2013 2014 110 100 90 80 70 60 50 40 30 20 10 0 Changing profile of cybercriminals Organised crime groups with considerable resources and expertise Attacks motivated by: • profit • botnet infrastructure • extortion • fame/notoriety • hacktivism Incident response threat intelligence • Incident response capabilities maturing at a slow pace. • 74% of organisations have no formal incident response plan. Average incident response time Organisations with no vulnerability management programme take nearly 200 days to patch vulnerabilities with CVSS score of 4.0 or more The threat intelligence cycle Our approach to successful threat intelligence helps numerous enterprises stay protected
