#AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
•
1 j'aime•2,628 vues
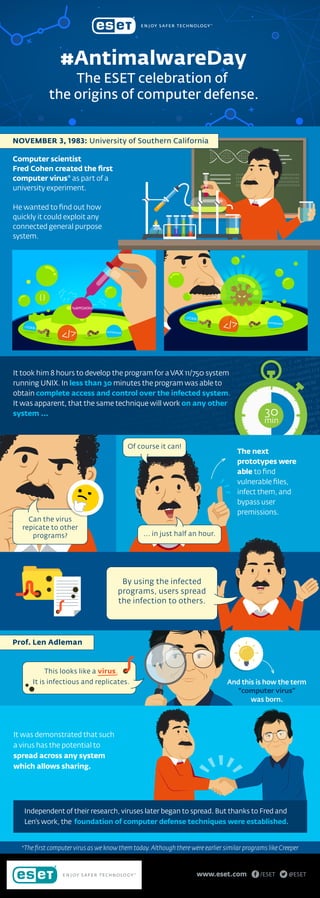
On November 3, 1983, Frederick Cohen, a student at the engineering school of the University of Southern California (USC), was sure that a malicious program could be used to exploit any connected system, but he wondered how long it would take for the code to do so. He prepared a prototype that – after eight hours of hard work on a VAX 11/750 system running Unix – was ready to be shown at the weekly security seminar he attended. It was his lecturer, Leonard Adleman, who baptized that program as a computer virus. Read more about #AntimalwareDay on WeLiveSecurity.com: https://goo.gl/QCSnc5
Signaler
Partager
Signaler
Partager
Contenu connexe
Tendances
Tendances (8)
Similaire à #AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
Similaire à #AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3 (20)
Biologically inspired defenses against computer viruses

Biologically inspired defenses against computer viruses
Plus de ESET
Plus de ESET (20)
How to implement a robust information security management system?

How to implement a robust information security management system?
AVAR Sydney 2014: Lemming Aid and Kool Aid: Helping the Community to Help Its...

AVAR Sydney 2014: Lemming Aid and Kool Aid: Helping the Community to Help Its...
ESET Quick Guide to the EU General Data Protection Regulation

ESET Quick Guide to the EU General Data Protection Regulation
Unpack your troubles*: .NET packer tricks and countermeasures

Unpack your troubles*: .NET packer tricks and countermeasures
ESET: #DoMore With Our Comprehensive Range of Business Products

ESET: #DoMore With Our Comprehensive Range of Business Products
ESET: Delivering Benefits to Medium and Large Businesses

ESET: Delivering Benefits to Medium and Large Businesses
Learn more about ESET and our soulutions for mobile platforms

Learn more about ESET and our soulutions for mobile platforms
Dernier
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...Medical / Health Care (+971588192166) Mifepristone and Misoprostol tablets 200mg
CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE

CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE9953056974 Low Rate Call Girls In Saket, Delhi NCR
MarTech Trend 2024 Book : Marketing Technology Trends (2024 Edition) How Data...

MarTech Trend 2024 Book : Marketing Technology Trends (2024 Edition) How Data...Jittipong Loespradit
Dernier (20)
%+27788225528 love spells in Colorado Springs Psychic Readings, Attraction sp...

%+27788225528 love spells in Colorado Springs Psychic Readings, Attraction sp...
Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...

Crypto Cloud Review - How To Earn Up To $500 Per DAY Of Bitcoin 100% On AutoP...
Payment Gateway Testing Simplified_ A Step-by-Step Guide for Beginners.pdf

Payment Gateway Testing Simplified_ A Step-by-Step Guide for Beginners.pdf
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...
Large-scale Logging Made Easy: Meetup at Deutsche Bank 2024

Large-scale Logging Made Easy: Meetup at Deutsche Bank 2024
%+27788225528 love spells in new york Psychic Readings, Attraction spells,Bri...

%+27788225528 love spells in new york Psychic Readings, Attraction spells,Bri...
Right Money Management App For Your Financial Goals

Right Money Management App For Your Financial Goals
call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️

call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️
CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE

CHEAP Call Girls in Pushp Vihar (-DELHI )🔝 9953056974🔝(=)/CALL GIRLS SERVICE
Architecture decision records - How not to get lost in the past

Architecture decision records - How not to get lost in the past
Shapes for Sharing between Graph Data Spaces - and Epistemic Querying of RDF-...

Shapes for Sharing between Graph Data Spaces - and Epistemic Querying of RDF-...
WSO2CON 2024 - Cloud Native Middleware: Domain-Driven Design, Cell-Based Arch...

WSO2CON 2024 - Cloud Native Middleware: Domain-Driven Design, Cell-Based Arch...
%in tembisa+277-882-255-28 abortion pills for sale in tembisa

%in tembisa+277-882-255-28 abortion pills for sale in tembisa
%in kempton park+277-882-255-28 abortion pills for sale in kempton park 

%in kempton park+277-882-255-28 abortion pills for sale in kempton park
%in Soweto+277-882-255-28 abortion pills for sale in soweto

%in Soweto+277-882-255-28 abortion pills for sale in soweto
MarTech Trend 2024 Book : Marketing Technology Trends (2024 Edition) How Data...

MarTech Trend 2024 Book : Marketing Technology Trends (2024 Edition) How Data...
#AntimalwareDay: The ESET Celebration of the Origins of Computer Defense in November 3
- 1. { } </> </CODE> %APPDATA% AUTORUN.INF </> </CODE> AUTORUN.INF #AntimalwareDay The ESET celebration of the origins of computer defense. 30 min It took him 8 hours to develop the program for aVAX 11/750 system running UNIX. In less than 30 minutes the program was able to obtain complete access and control over the infected system. It was apparent, that the same technique will work on any other system ... Computer scientist Fred Cohen created the first computer virus* as part of a university experiment. He wanted to find out how quickly it could exploit any connected general purpose system. NOVEMBER 3, 1983: University of Southern California Can the virus repicate to other programs? Of course it can! ... in just half an hour. The next prototypes were able to find vulnerable files, infect them, and bypass user premissions. And this is how the term “computer virus” was born. It was demonstrated that such a virus has the potential to spread across any system which allows sharing. The first computer virus as we know them today.Although there were earlier similar programs like Creeper www.eset.com @ESET/ESET This looks like a virus. It is infectious and replicates. Prof. Len Adleman Independent of their research, viruses later began to spread. But thanks to Fred and Len's work, the foundation of computer defense techniques were established. By using the infected programs, users spread the infection to others.
