5 Reasons Cyber Attackers Target Small and Medium Businesses
•
0 j'aime•996 vues
High-profile data breaches of corporate giants make the headlines. But 77% of cyber crime actually targets small and midsize enterprises (SMEs). Here's why SMEs are targets, and what you can do about it.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Estudio de Russell Reynolds Associates sobre ciberseguridad que explora la importancia de la relación entre el Chief Information Security Officer y el Consejo de Administración. Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Contenu connexe
Tendances
Estudio de Russell Reynolds Associates sobre ciberseguridad que explora la importancia de la relación entre el Chief Information Security Officer y el Consejo de Administración. Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Tendances (20)
Cost of Cybercrime Study in Financial Services: 2019 Report

Cost of Cybercrime Study in Financial Services: 2019 Report
Accenture Security Report 2016 Infographic for Insurance

Accenture Security Report 2016 Infographic for Insurance
Cyber-risk Oversight Handbook for Corporate Boards

Cyber-risk Oversight Handbook for Corporate Boards
Nearly 80 billion dollars were spent in 2016 to fight cybercrime

Nearly 80 billion dollars were spent in 2016 to fight cybercrime
Global CCISO Forum 2018 | Ondrej Krehel | The Era of Cyber Extortion and Rans...

Global CCISO Forum 2018 | Ondrej Krehel | The Era of Cyber Extortion and Rans...
"10 Tips To Keep Cybercriminals Out While Coronavirus Keeps You In" Infographic

"10 Tips To Keep Cybercriminals Out While Coronavirus Keeps You In" Infographic
#GlenLegal 2018 Conference Agenda - Scott Cairns - T-Systems Security Imperitive

#GlenLegal 2018 Conference Agenda - Scott Cairns - T-Systems Security Imperitive
Adapted from an ESG report - Seeing Is Securing - Protecting Against Advanced...

Adapted from an ESG report - Seeing Is Securing - Protecting Against Advanced...
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attention
En vedette
En vedette (11)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...
Asia Pacific & The Security Gap: Don't Stand Still

Asia Pacific & The Security Gap: Don't Stand Still
FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach

FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach
Proatively Engaged: Questions Executives Should Ask Their Security Teams

Proatively Engaged: Questions Executives Should Ask Their Security Teams
Similaire à 5 Reasons Cyber Attackers Target Small and Medium Businesses
Similaire à 5 Reasons Cyber Attackers Target Small and Medium Businesses (20)
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
Joint Presentation on The State of Cybersecurity ('15-'16) & Third Party Cyb...

Joint Presentation on The State of Cybersecurity ('15-'16) & Third Party Cyb...
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
Cybersecurity Myths for Small and Medium-Sized Businesses

Cybersecurity Myths for Small and Medium-Sized Businesses
How to assess your Cybersecurity Vulnerability_.pdf

How to assess your Cybersecurity Vulnerability_.pdf
How to assess your Cybersecurity Vulnerability_.pptx

How to assess your Cybersecurity Vulnerability_.pptx
BIZGrowth Strategies — Cybersecurity Special Edition 2023

BIZGrowth Strategies — Cybersecurity Special Edition 2023
Plus de FireEye, Inc.
Plus de FireEye, Inc. (12)
[Infographic] Healthcare Cyber Security: Threat Prognosis![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Healthcare Cyber Security: Threat Prognosis
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
FireEye Advanced Threat Protection - What You Need to Know

FireEye Advanced Threat Protection - What You Need to Know
Dernier
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Dernier (20)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
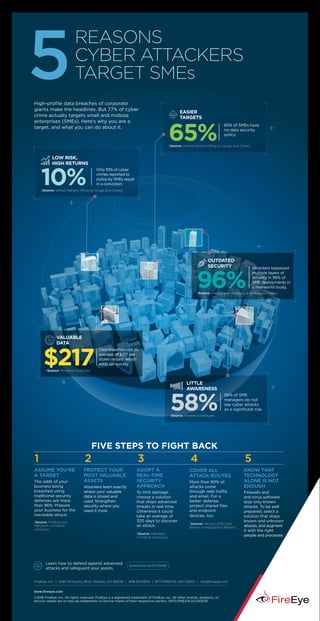
5 Reasons Cyber Attackers Target Small and Medium Businesses
- 1. FireEye, Inc. | 1440 McCarthy Blvd. Milpitas, CA 95035 | 408.321.6300 | 877.FIREEYE (347.3393) | info@fireeye.com www.fireeye.com ©2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.SMB.EN-US.042016 REASONS CYBER ATTACKERS TARGET SMEs5High-profile data breaches of corporate giants make the headlines. But 77% of cyber crime actually targets small and midsize enterprises (SMEs). Here's why you are a target, and what you can do about it. FIVE STEPS TO FIGHT BACK Learn how to defend against advanced attacks and safeguard your assets. DOWNLOAD WHITE PAPER + + PROTECT YOUR MOST VALUABLE ASSETS Attackers learn exactly where your valuable data is stored and used. Strengthen security where you need it most. KNOW THAT TECHNOLOGY ALONE IS NOT ENOUGH Firewalls and anti-virus software stop only known attacks. To be well prepared, select a solution that stops known and unknown attacks, and augment it with the right people and processes. ASSUME YOU’RE A TARGET The odds of your business being breached using traditional security defenses are more than 96%. Prepare your business for the inevitable attack. (Source: FireEye and Mandiant, a FireEye company) COVER ALL ATTACK ROUTES More than 90% of attacks come through web traffic and email. For a better defense, protect shared files and endpoint devices, too. (Source: Verizon 2015 Data Breach Investigations Report) ADOPT A REAL-TIME SECURITY APPROACH To limit damage, choose a solution that stops advanced threats in real time. Otherwise it could take an average of 320 days to discover an attack. (Source: Mandiant, a FireEye company) 1 2 3 4 5 + + + + (Source: United Nations Office on Drugs and Crime) LOW RISK, HIGH RETURNS 10% Only 10% of cyber crimes reported to police by SMEs result in a conviction. (Source: United Nations Office on Drugs and Crime) EASIER TARGETS 65% 65% of SMEs have no data security policy. LITTLE AWARENESS 58% 58% of SME managers do not see cyber attacks as a significant risk. (Source: Ponemon Institute) (Source: Ponemon Institute) VALUABLE DATA $217 Data breaches cost an average of $217 per stolen record, which adds up quickly. (Source: FireEye and Mandiant, a FireEye company) OUTDATED SECURITY Attackers bypassed multiple layers of security in 96% of SME deployments in a real-world study.96%
