[Infographic] M-Trends 2016
•
0 j'aime•752 vues
M-Trends 2016 provides trends, statistics and case studies to illustrate how advanced threat actors have evolved over the past year. The annual report was compiled by consultants at Mandiant and is based on hundreds of incident response investigations in more than 30 industry sectors. View the infographic to get the latest cover attacker trends and industry targets. For more information on Mandiant consulting services, visit www.fireeye.com/services.html.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
En vedette
En vedette (10)
WUD 2009 - User Experience Design a telefony komórkowe

WUD 2009 - User Experience Design a telefony komórkowe
Plus de FireEye, Inc.
Plus de FireEye, Inc. (20)
Asia Pacific & The Security Gap: Don't Stand Still

Asia Pacific & The Security Gap: Don't Stand Still
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...
[Infographic] Healthcare Cyber Security: Threat Prognosis![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Healthcare Cyber Security: Threat Prognosis
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach

FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach
Dernier
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Dernier (20)
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
[Infographic] M-Trends 2016
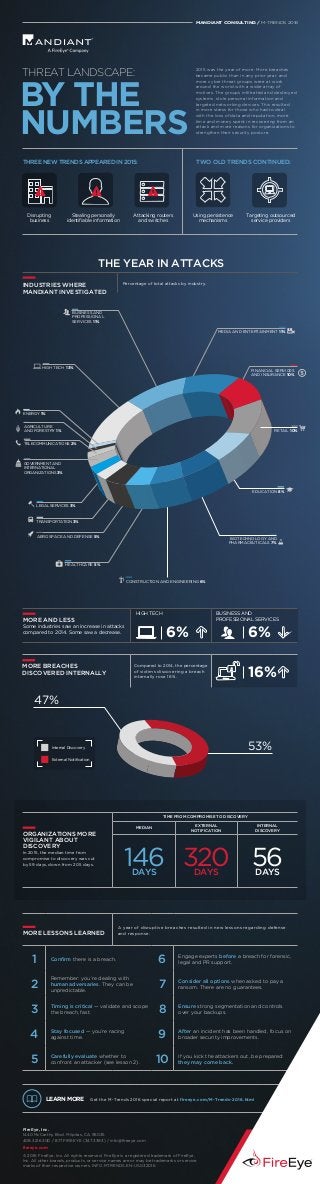
- 1. 2015 was the year of more. More breaches became public than in any prior year, and more cyber threat groups were at work around the world with a wider array of motives. The groups infiltrated and destroyed systems, stole personal information and targeted networking devices. This resulted in more stress for those who had to deal with the loss of data and reputation, more time and money spent in recovering from an attack and more reasons for organizations to strengthen their security posture. BY THE NUMBERS THREAT LANDSCAPE: MANDIANT CONSULTING / M-TRENDS 2016 ENERGY 1% AGRICULTURE AND FORESTRY 1% HIGH TECH 13% GOVERNMENT AND INTERNATIONAL ORGANIZATIONS 3% LEGAL SERVICES 3% TRANSPORTATION 3% BUSINESS AND PROFESSIONAL SERVICES 11% MEDIA AND ENTERTAINMENT 11% FINANCIAL SERVICES AND INSURANCE 10% RETAIL 10% EDUCATION 8% BIOTECHNOLOGY AND PHARMACEUTICALS 7% CONSTRUCTION AND ENGINEERING 6% HEALTHCARE 5% AEROSPACE AND DEFENSE 5% TELECOMMUNICATIONS 2% ORGANIZATIONS MORE VIGILANT ABOUT DISCOVERY In 2015, the median time from compromise to discovery was cut by 59 days, down from 205 days. TIME FROM COMPROMISE TO DISCOVERY MEDIAN EXTERNAL NOTIFICATION INTERNAL DISCOVERY 146DAYS 320DAYS 56DAYS MORE LESSONS LEARNED A year of disruptive breaches resulted in new lessons regarding defense and response. 1 Confirm there is a breach. 6 Engage experts before a breach for forensic, legal and PR support. 2 Remember: you’re dealing with human adversaries. They can be unpredictable. 7 Consider all options when asked to pay a ransom. There are no guarantees. 3 Timing is critical — validate and scope the breach, fast. 8 Ensure strong segmentation and controls over your backups. 4 Stay focused — you’re racing against time. 9 After an incident has been handled, focus on broader security improvements. 5 Carefully evaluate whether to confront an attacker (see lesson 2). 10 If you kick the attackers out, be prepared: they may come back. LEARN MORE Get the M-Trends 2016 special report at fireeye.com/M-Trends-2016.html FireEye, Inc. 1440 McCarthy Blvd. Milpitas, CA 95035 408.321.6300 / 877.FIREEYE (347.3393) / info@fireeye.com fireeye.com © 2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.MTRENDS.EN-US.032016 Disrupting business Stealing personally identifiable information Attacking routers and switches THREE NEW TRENDS APPEARED IN 2015: Using persistence mechanisms Targeting outsourced service providers TWO OLD TRENDS CONTINUED: THE YEAR IN ATTACKS 47% 53% External Notification Internal Discovery MORE BREACHES DISCOVERED INTERNALLY Compared to 2014, the percentage of victims discovering a breach internally rose 16%. 16% INDUSTRIES WHERE MANDIANT INVESTIGATED Percentage of total attacks by industry. MORE AND LESS Some industries saw an increase in attacks compared to 2014. Some saw a decrease. HIGH TECH BUSINESS AND PROFESSIONAL SERVICES 6%6%
