FirstPartner 2014 Mobile Data Security Market Map
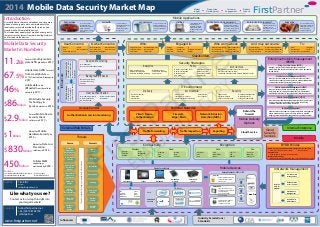
- 1. www.firstpartner.net Mobile Data Security Market in Numbers 11.2EB Forecast monthly mobile data traffic globally in 2017(1) $2.9Billion Sales of Mobile Device Security Client software in 2017 (2) 67.5% Mobile data traffic forecast from smartphones vs 25.7% from tablets & laptops in 2017 (1) $86Billion Worldwide Security Technology & Services market in 2016(3) $1Billion Market for Mobile Hardware Security by 2014 (4) $830Million Market for Data Loss Prevention solutions in 2014 (3) Introduction As mobile devices become ubiquitous and store more personal and corporate data, new methods will be required to secure information both stored on and transferrred to & from mobile devices. The tremendous popularity of mobile devices greatly increases security threats from data-stealing malware and lost and stolen devices. Mobile Applications mHealth mCommerce Utilities Public Sector & Government Enterprise & Corporate IT EducationAutomotive In car connectivity to provide telemetry functions from onboard systems including critical safety & security functions Sensitive medical information for in home care and mobile diagnostic & patient management Secure transaction and payment information transfer required from a variety of unamnaged devices Smart Meter & supply network remote management M2M deployments require resilience from hostile threats Deployments to a variety of mobile workers requires compliance in information access and storage security outside of the firewall Productivity & service applications requiring realtime access to Enterprise resources & information Secure environment for deployment of learning platforms to provide access to learning materials anywhere 46% Mobile data to be offloaded from the cellular network in 2017 (1) 450Million Cellular M2M connections worldwide by 2018 (3) iOS Android Windows Blackberry Linux QNX Bada Symbian OS Processor Core Embedded Security Mobile DevicesDevice form Factors Smartphone Tablet Notebook Embedded module Embedded system In Network Management Embedded Incorporated during equipment manufacture for remote OTA provisioning and management Virtual Software emulation of standards by code resident on device Physical Preprogrammed device for physical insertion into device Card OS Java Card VM Java Card Framework & APIs Applet Secure Elements - SIM / UICC Over The Air (OTA) Platform Authentication Access Control Performance Management Operations & Maintenance Trusted Service Management Influencers Industry Associations / Standards Security Strategies • Data loss prevention (DLP) • Device interrogation • Device controls • App policy • Geo-location control • Data encryption • User authentication • App blacklist Policy Architecture • Multiple Independent Level of Security (MILS) • Multiple Level Security (MLS) • Seperation Kernel between Above & Below OS Levels • Big Data Monitoring • Incident investigation • Real time collection & alerting Analytics • Malware analytics • Compliance reporting • App analytics Perimiter Network Client / Device Authentication Firewall - Edge / Main Network Intrusion Detection (NIDS) Stakeholders • Energy • Materials • Industrial • Consumer • Health Care • Financial • IT • Telecommunications • Utilities Engaged in: • Cloud services • Network & Telecom • IT Infrastructure And may outsource: • Project Management • Software Development • Help Desk & Support • VARs • Datacentres • Outsource Service Providers To: • Integrators • Carriers • Policy & Compliance • Service Delivery • Investment costs & Business justification Who worry about: • Reputational loss • Financial loss • Large Enterprise • Small & Medium Enterprises • National Corporates • Multi-national Corporates Who: Authentication & session monitoring Access Control Influencers Userconfidenceinsafety &reliabilityofboththeir session&anytransferred information Userabilitytogain access&complete sessionsquickly&easily UserExperienceIncreasedsecurity • Device fingerprinting • IP address checking • Cookies Background Checks • User behaviour • User session anomally detection Session Monitoring User Authentication • User name & password • 2 factor out of band • Hardware based • Risk or context based • Biometrics • Privacy • Trust • Transaction security • Fraud • Poor experience User Concerns: • Mass breaches • Loss of business • Regulatory compliance • Information loss • Access Security Owner Concerns: Mobile Content Management (MCM) Manages secure mobile access to enterprise content. These solution are extending to manage secure mobile collaborative environments including version control & sync. Enterprise Mobility Management (EMM) Formats Phishing “Man In The Middle” Protocol Threats Denial of Service Spyware Surveillance Ransomware Source Malware & Viruses NFC & proximity based hacking Cloud data privacy Accidental insider leakage Unsecure file transfer Data loss from lost /stolen devcies Insecure WiFi networks & rogue access Threats External Web Portals Internal Enterprise Mobile 2014 Mobile Data Security Market Map FirstPartnerMarket Insight Proposition Development Product Launch Customer Engagement www.firstpartner.net Tim Ellis Partner tellis@firstpartner.net +44 (0) 870 874 8700 @firstpartner hello@firstpartner.net Like what you see? Contact us for in-depth insight into your target markets! Contacts Author www.firstpartner.net Sources (1) Cisco VNI Global Mobile Forecast 2013 (2) Infonetics Research 04/2013 (3) Gartner 2013 (4) ABI Research 2014 Threatsareconstantlychangingaspreventionmethodsdevelop Malware import from physical device IT Environment Delivery • Business Processes • Information • Applications • Firewall / DMZ • Cloud (public / Private) • Administration & Provisioning Architecture • Virtualisation • Data Centres Security • Tokenisation • Digital certificates • Secure Code Execution • Credential Management • Digital Signatures • Strong Authentication Device security separation between Enterprise & Personal data BYOD Policies Behind the firewall Mobile Delivery Options Traffic Forwarding Traffic Inspection Reporting • Work zones (General & Classified) • Personal zone Acceptable use Employee Exit Strategy • Enforced removal of proprietary apps, information & access rights • Allowed apps & network access methods Bring Your Own Device (BYOD) Manages, secures and provides company controlled productivity and secure connectivity resources on personally owned devices. Mobile Application Management (MAM) Manages internal, public & purchased applications on enterprise devices throughout their lifecycle. Also includes applications blacklists to prevent their installation on devices. Identity Theft Enables remote asset audit & IT policy compliance management before network access is granted. These tools may provide ongoing automated patch management & reporting functions . Endpoint Management Mobile Device Management (MDM) Provides central administration of mobile asset use, enforces IT policies manages secure corporate network access using available preferred connectivity resources. Cloud Service Cloud Security Services Connectivity • DES/3DES • AES • DSA • SHA • WPA/WPA2 • IPSec • SSL / TLS • SSH • WiMAX Data • TrueCrypt • BitLocker • boxcryptor File • Cellular • Satellite • WiMAX • WiFi • Bluetooth • NFC Wireless Fixed • Ethernet • DSL • ISDN • Dial Up • USB • Firewire Encryption FirstPartner EVALUATION COPY
