Audit commands by shift
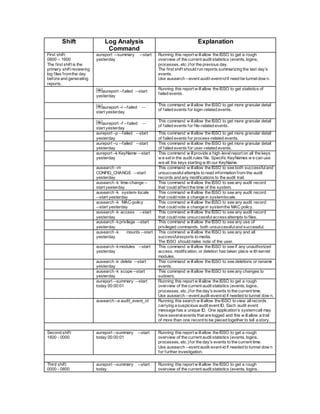
- 1. Shift Log Analysis Command Explanation First shift: 0800 – 1600 The first shift is the primary shift reviewing log files fromthe day before and generating reports. aureport --summary --start yesterday Running this report w illallow the ISSO to get a rough overview of the current audit statistics (events, logins, processes, etc.)for the previous day. The first shift should run reports summarizing the last day’s events. Use ausearch --event audit-event-id if need be tunneldow n. aureport --failed --start yesterday Running this report w illallow the ISSO to get statistics of failed events. aureport –l --failed -- start yesterday This command w illallow the ISSO to get more granular detail of failed events for login-related events. aureport –f --failed -- start yesterday This command w illallow the ISSO to get more granular detail of failed events for file-related events. aureport –p --failed --start yesterday This command w illallow the ISSO to get more granular detail of failed events for process-related events. aureport –u --failed --start yesterday This command w illallow the ISSO to get more granular detail of failed events for user-related events. aureport –k KeyName --start yesterday This command w illprovide a high-levelreport on all the keys w e set in the audit.rules file. Specific KeyNames w e can use are all the keys starting w ith our KeyName. ausearch –m CONFIG_CHANGE --start yesterday This command w illallow the ISSO to see both successfuland unsuccessfulattempts to read information from the audit records and any modifications to the audit trail. ausearch -k time-change -- start yesterday This command w illallow the ISSO to see any audit record that could affect the time of the system. ausearch -k system- locale --start yesterday This command w illallow the ISSO to see any audit record that could note a change in systemlocale. ausearch -k MAC-policy --start yesterday This command w illallow the ISSO to see any audit record that could note a change in systemthe MAC policy. ausearch -k access --start yesterday This command w illallow the ISSO to see any audit record that could note unsuccessfulaccessattempts to files. ausearch -kprivilege --start yesterday This command w illallow the ISSO to see any use of privileged commands, both unsuccessfuland successful. ausearch -k mounts --start yesterday This command w illallow the ISSO to see any and all successfulexports to media. The ISSO should make note of the user. ausearch -kmodules --start yesterday This command w illallow the ISSO to see if any unauthorized access, modification, or deletion has taken place w ith kernel modules. ausearch -k delete --start yesterday This command w illallow the ISSO to see deletions or rename events. ausearch -k scope --start yesterday This command w illallow the ISSO to see any changes to sudoers. aureport --summary --start today 00:00:01 Running this report w illallow the ISSO to get a rough overview of the current audit statistics (events, logins, processes, etc.)for the day’s events to the current time. Use ausearch --event audit-event-id if needed to tunnel dow n. ausearch –a audit_event_id Running this search w illallow the ISSO to view allrecords carrying a suspicious audit event ID. Each audit event message has a unique ID. One application’s systemcall may have severalevents that are logged and this w illallow a trail of more than one record to be pieced together to tell a story. Second shift: 1600 - 0000 aureport --summary --start today 00:00:01 Running this report w illallow the ISSO to get a rough overview of the current audit statistics (events, logins, processes, etc.)for the day’s events to the current time. Use ausearch --event audit-event-id if needed to tunnel dow n for further investigation. Third shift: 0000 - 0800 aureport --summary --start today Running this report w illallow the ISSO to get a rough overview of the current audit statistics (events, logins,
- 2. Shift Log Analysis Command Explanation processes, etc.)for the day’s events to the current time. Use ausearch --event audit-event-id if needed to tunnel dow n for further investigation. ausearch -ts today 00:00:01 --raw |aulast --stdin Running this report w illallow the ISSO to report on all bad log- ins for the day. All users found in this list should be emailed and asked if they had failed logins for that specific day. When they come in for w orkthe next day, they w illsee their email. Policy states that they are to reply back if they did not have the failed log-in attempt.
