#BCMeeting2019: Rethinking Cybersecurity
•Télécharger en tant que PPTX, PDF•
0 j'aime•333 vues
Presentation provided at the Annual ICC Banking Commission Meeting by Sukand Ramachandran on 11 April 2019.
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
Physical Security Information Management (PSIM) Solution for the Government

Physical Security Information Management (PSIM) Solution for the Government
Data Leak Protection Using Text Mining and Social Network Analysis

Data Leak Protection Using Text Mining and Social Network Analysis
Master Class Cyber Compliance IE Law School IE Busines School

Master Class Cyber Compliance IE Law School IE Busines School
Risk Management and Security in Strategic Planning

Risk Management and Security in Strategic Planning
Similaire à #BCMeeting2019: Rethinking Cybersecurity
Similaire à #BCMeeting2019: Rethinking Cybersecurity (20)
Practical Guide to Managing Incidents Using LLM's and NLP.pdf

Practical Guide to Managing Incidents Using LLM's and NLP.pdf
Legal and Ethical Implications of Cybersecurity.pptx

Legal and Ethical Implications of Cybersecurity.pptx
Healthcare info tech systems cyber threats ABI conference 2016

Healthcare info tech systems cyber threats ABI conference 2016
IT 552 Module Five Assignment Rubric The purpose of t.docx

IT 552 Module Five Assignment Rubric The purpose of t.docx
The 7 Steps to Prevent IT-Caused Outages- A Comprehensive Approach

The 7 Steps to Prevent IT-Caused Outages- A Comprehensive Approach
NIST CSF review - Essential Protections (a K12 perspective)

NIST CSF review - Essential Protections (a K12 perspective)
Cybersecurity Assessment Framework - Slideshare.pptx

Cybersecurity Assessment Framework - Slideshare.pptx
case studies on risk management in IT enabled organisation(vadodara)

case studies on risk management in IT enabled organisation(vadodara)
Project 4 Threat Analysis and ExploitationTranscript (backgroun.docx

Project 4 Threat Analysis and ExploitationTranscript (backgroun.docx
Ch08 8 Information Security Process it-slideshares.blogspot.com

Ch08 8 Information Security Process it-slideshares.blogspot.com
Satori Whitepaper: Threat Intelligence - a path to taming digital threats

Satori Whitepaper: Threat Intelligence - a path to taming digital threats
Forging Partnerships Between Auditors and Security Managers

Forging Partnerships Between Auditors and Security Managers
Reorganizing Federal IT to Address Today's Threats

Reorganizing Federal IT to Address Today's Threats
Plus de International Chamber of Commerce - ICC
Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...

Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...International Chamber of Commerce - ICC
Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres

Reports from ICC BC Task Forces - Financial Crime Risk - Henri DambrieresInternational Chamber of Commerce - ICC
Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock

Reports from ICC BC Task Forces - Financial Crime Risk - Graham BaldockInternational Chamber of Commerce - ICC
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative International Chamber of Commerce - ICC
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative International Chamber of Commerce - ICC
ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...

ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...International Chamber of Commerce - ICC
Plus de International Chamber of Commerce - ICC (20)
Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...

Update on Incoterms® 2020, ICC Marketplace, ICC Digital Library and chambers ...
Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres

Reports from ICC BC Task Forces - Financial Crime Risk - Henri Dambrieres
Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock

Reports from ICC BC Task Forces - Financial Crime Risk - Graham Baldock
Documentary Credit Practices: Controversy & Guidance

Documentary Credit Practices: Controversy & Guidance
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative
ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative 

ICC Banking Commission Technical Meeting 17/10/2018 - Outreach initiative
ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...

ICC BANKING COMMISSION MIAMI MEETING 2018: Day 2 @ 16:00 Sustainability and T...
Dernier
VVIP Pune Call Girls Katraj (7001035870) Pune Escorts Nearby with Complete Sa...

VVIP Pune Call Girls Katraj (7001035870) Pune Escorts Nearby with Complete Sa...Call Girls in Nagpur High Profile
Dernier (20)
Malad Call Girl in Services 9892124323 | ₹,4500 With Room Free Delivery

Malad Call Girl in Services 9892124323 | ₹,4500 With Room Free Delivery
Lundin Gold April 2024 Corporate Presentation v4.pdf

Lundin Gold April 2024 Corporate Presentation v4.pdf
VIP Kolkata Call Girl Serampore 👉 8250192130 Available With Room

VIP Kolkata Call Girl Serampore 👉 8250192130 Available With Room
Dharavi Russian callg Girls, { 09892124323 } || Call Girl In Mumbai ...

Dharavi Russian callg Girls, { 09892124323 } || Call Girl In Mumbai ...
High Class Call Girls Nagpur Grishma Call 7001035870 Meet With Nagpur Escorts

High Class Call Girls Nagpur Grishma Call 7001035870 Meet With Nagpur Escorts
Best VIP Call Girls Noida Sector 18 Call Me: 8448380779

Best VIP Call Girls Noida Sector 18 Call Me: 8448380779
Dividend Policy and Dividend Decision Theories.pptx

Dividend Policy and Dividend Decision Theories.pptx
Solution Manual for Principles of Corporate Finance 14th Edition by Richard B...

Solution Manual for Principles of Corporate Finance 14th Edition by Richard B...
VVIP Pune Call Girls Katraj (7001035870) Pune Escorts Nearby with Complete Sa...

VVIP Pune Call Girls Katraj (7001035870) Pune Escorts Nearby with Complete Sa...
TEST BANK For Corporate Finance, 13th Edition By Stephen Ross, Randolph Weste...

TEST BANK For Corporate Finance, 13th Edition By Stephen Ross, Randolph Weste...
Independent Call Girl Number in Kurla Mumbai📲 Pooja Nehwal 9892124323 💞 Full ...

Independent Call Girl Number in Kurla Mumbai📲 Pooja Nehwal 9892124323 💞 Full ...
20240417-Calibre-April-2024-Investor-Presentation.pdf

20240417-Calibre-April-2024-Investor-Presentation.pdf
#BCMeeting2019: Rethinking Cybersecurity
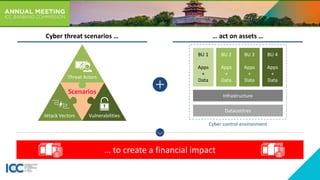
- 1. Scenarios Threat Actors Attack Vectors Vulnerabilities Cyber threat scenarios … … act on assets … … to create a financial impact Datacentres Infrastructure BU 1 Apps + Data BU 2 Apps + Data BU 3 Apps + Data BU 4 Apps + Data Cyber control environment
- 2. NIST is an industry standard framework for categorising Cyber controls Governance Outlines key governance processes that must be in place to manage cybersecurity environments, centered around strategy, policy and audit Identify Assists in developing controls required to identify where a cybersecurity event may take place, and understand the risk to systems, people, assets, data, and capabilities Protect Outlines appropriate safeguards to ensure delivery of critical infrastructure services, and supports the ability to limit or contain the impact of a potential cybersecurity event Detect Defines the appropriate activities to identify the occurrence of a cybersecurity event, driving to timely discovery of cybersecurity events Respond Includes appropriate activities to take action regarding a detected cybersecurity incident, including how to contain the impact of a potential cybersecurity incident. Recover Identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident Explains how to manage and minimise supply chain and third party dependency risks that organisations have less control over Supply chain/dep. management
- 3. Estimating the impact of cybersecurity events … … enables clear communication of impact/mitigations Taking a methodology we're comfortable with … Expected Loss = Likelihood of Default x Impact given Default Likelihood of success x Financial Impact = Exposure ThreatIntensity (ThreatActors+AttackVectors) Vulnerability (as a function of controls) …and applying it to different types of cyber risk Allows estimation of loss impacts on assets … … and how to reduce impact through cyber mitigations
- 4. Call To Action! We need alignment on taxonomy … ...and to use similar methodologies
