ISACA State of Cyber Security 2017
•
2 j'aime•1,831 vues
A look at the state of the cyber security workforce.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Recommandé
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Contenu connexe
Tendances
Tendances (20)
Reinforcing the Revolution: The Promise and Perils of Digital Transformation

Reinforcing the Revolution: The Promise and Perils of Digital Transformation
Cyber-risk Oversight Handbook for Corporate Boards

Cyber-risk Oversight Handbook for Corporate Boards
Infographic - Three steps to stopping advanced email threats

Infographic - Three steps to stopping advanced email threats
Cybersecurity: Cyber Risk Management for Banks & Financial Institutions

Cybersecurity: Cyber Risk Management for Banks & Financial Institutions
Cybersecurity in the Cognitive Era: Priming Your Digital Immune System

Cybersecurity in the Cognitive Era: Priming Your Digital Immune System
Adapted from an ESG report - Outnumbered, Outgunned. 

Adapted from an ESG report - Outnumbered, Outgunned.
En vedette
En vedette (20)
COBIT 5 Infographic: Extracting Value From Information Chaos

COBIT 5 Infographic: Extracting Value From Information Chaos
The difference between Cybersecurity and Information Security

The difference between Cybersecurity and Information Security
Symantec Internet Security Threat Report 2014 - Volume 19

Symantec Internet Security Threat Report 2014 - Volume 19
Industrial Control System Cyber Security and the Employment of Industrial Fir...

Industrial Control System Cyber Security and the Employment of Industrial Fir...
Similaire à ISACA State of Cyber Security 2017
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attentionRamón Gómez de Olea y Bustinza
Similaire à ISACA State of Cyber Security 2017 (20)
Cybersecurity Talent : The Big Gap in Cyber Protection

Cybersecurity Talent : The Big Gap in Cyber Protection
Achieving Holistic Cybersecurity: 2016 Progress Report

Achieving Holistic Cybersecurity: 2016 Progress Report
ISACA and RSA CSX Presentation from the RSA 2015 Conference 

ISACA and RSA CSX Presentation from the RSA 2015 Conference
2013-ISC2-Global-Information-Security-Workforce-Study

2013-ISC2-Global-Information-Security-Workforce-Study
Prof m01-2013 global information security workforce study - final

Prof m01-2013 global information security workforce study - final
State-of-Cybersecurity-2022_WHPSC22_res_eng_0322.pdf

State-of-Cybersecurity-2022_WHPSC22_res_eng_0322.pdf
Study master of cyber security at australia with scholarship

Study master of cyber security at australia with scholarship
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attention
Dernier
Dernier (20)
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
ISACA State of Cyber Security 2017
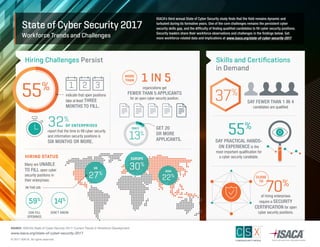
- 1. State of Cyber Security 2017 Workforce Trends and Challenges ISACA’s third annual State of Cyber Security study finds that the field remains dynamic and turbulent during its formative years. One of the core challenges remains the persistent cyber security skills gap, and the difficulty of finding qualified candidates to fill cyber security positions. Security leaders share their workforce observations and challenges in the findings below. Get more workforce-related data and implications at www.isaca.org/state-of-cyber-security-2017. Skills and Certifications in Demand Hiring Challenges Persist organizations get FEWER THAN 5 APPLICANTS for an open cyber security position. indicate that open positions take at least THREE MONTHS TO FILL. report that the time to fill cyber security and information security positions is SIX MONTHS OR MORE. 55% IN THE US: EUROPE 30% ASIA 22% HIRING STATUS US 27% Many are UNABLE TO FILL open cyber security positions in their enterprises: 1 IN 5 55% SAY PRACTICAL HANDS- ON EXPERIENCE is the most important qualification for a cyber security candidate. 59% DON’T KNOW 14% CAN FILL OPENINGS SOURCE: ISACA’s State of Cyber Security 2017: Current Trends in Workforce Development www.isaca.org/state-of-cyber-security-2017 © 2017 ISACA. All rights reserved. MORE THAN 32% OF ENTERPRISES GET 20 OR MORE APPLICANTS.13% ONLY 70% of hiring enterprises require a SECURITY CERTIFICATION for open cyber security positions. CLOSE TO 1 2 3 SAY FEWER THAN 1 IN 4 candidates are qualified 37%
