Manage Privacy, Security and Performance Across Cloud and On-Premises with Windows Server 2019
•
0 j'aime•31 vues
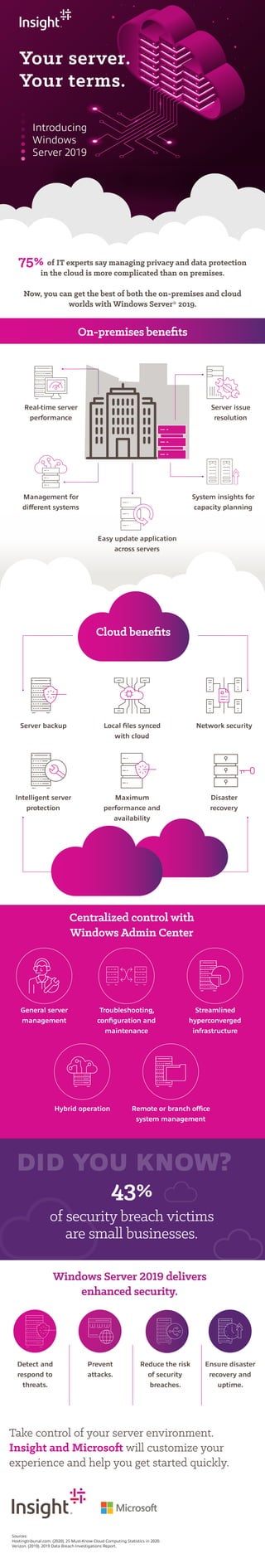
Windows Server 2019 allows for centralized control through Windows Admin Center for managing servers on-premises or in the cloud. It provides real-time performance insights, issue resolution, and management capabilities for different systems. Windows Server 2019 also enhances security through threat detection and prevention to reduce the risk of breaches while ensuring disaster recovery and uptime.
Signaler
Partager
Signaler
Partager
Recommandé
Contenu connexe
Tendances
Tendances (20)
Gain Visibility & Control of IT Assets in a Perimeterless World

Gain Visibility & Control of IT Assets in a Perimeterless World
Securing Your Business #3 - Role Of The Service Provider

Securing Your Business #3 - Role Of The Service Provider
Webcast Series #1: Continuous Security and Compliance Monitoring for Global I...

Webcast Series #1: Continuous Security and Compliance Monitoring for Global I...
Acronis Active Protection: A Way To Combat Ransomware Attack

Acronis Active Protection: A Way To Combat Ransomware Attack
Similaire à Manage Privacy, Security and Performance Across Cloud and On-Premises with Windows Server 2019
Similaire à Manage Privacy, Security and Performance Across Cloud and On-Premises with Windows Server 2019 (20)
Symantec Best Practices for Cloud Security: Insights from the Front Lines

Symantec Best Practices for Cloud Security: Insights from the Front Lines
Pros And Cons Of Cloud-Based Security Solutions.pptx

Pros And Cons Of Cloud-Based Security Solutions.pptx
Protect your hybrid workforce across the attack chain

Protect your hybrid workforce across the attack chain
Cloud Service Brief - dinCloud Hosted Virtual Desktop

Cloud Service Brief - dinCloud Hosted Virtual Desktop
glenn_amblercloud_security_ncc_event_22-may-2012_v1 (9)

glenn_amblercloud_security_ncc_event_22-may-2012_v1 (9)
Indonesia new default short msp client presentation partnership with isv

Indonesia new default short msp client presentation partnership with isv
Plus de Insight
Plus de Insight (20)
Infographic | The Growing Need for Fast, Secure Telehealth

Infographic | The Growing Need for Fast, Secure Telehealth
Infographic | 4 Reasons to Make the Switch to Chrome OS With Insight

Infographic | 4 Reasons to Make the Switch to Chrome OS With Insight
Take a Holistic Approach to Securing Connected Manufacturing

Take a Holistic Approach to Securing Connected Manufacturing
Infographic | Software Facilitates Smart(er) Manufacturing

Infographic | Software Facilitates Smart(er) Manufacturing
Infographic | How It Works: Community Wireless Broadband

Infographic | How It Works: Community Wireless Broadband
An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...

An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...
Welcome to the Future of Work: The Hybrid Workplace

Welcome to the Future of Work: The Hybrid Workplace
Building a Modern Workplace: The Value Add of Technology Optimization

Building a Modern Workplace: The Value Add of Technology Optimization
Manage Privacy, Security and Performance Across Cloud and On-Premises with Windows Server 2019
- 1. 75% of IT experts say managing privacy and data protection in the cloud is more complicated than on premises. Now, you can get the best of both the on-premises and cloud worlds with Windows Server® 2019. Introducing Windows Server 2019 Your server. Your terms. Centralized control with Windows Admin Center Take control of your server environment. Insight and Microsoft will customize your experience and help you get started quickly. 43% of security breach victims are small businesses. Real-time server performance Server issue resolution Management for different systems System insights for capacity planning Easy update application across servers Server backup Intelligent server protection Local files synced with cloud Maximum performance and availability Network security Disaster recovery On-premises benefits Cloud benefits DID YOU KNOW? Windows Server 2019 delivers enhanced security. Detect and respond to threats. Prevent attacks. Reduce the risk of security breaches. Ensure disaster recovery and uptime. General server management Troubleshooting, configuration and maintenance Streamlined hyperconverged infrastructure Hybrid operation Remote or branch office system management Sources: Hostingtribunal.com. (2020). 25 Must-Know Cloud Computing Statistics in 2020. Verizon. (2019). 2019 Data Breach Investigations Report.
