The state of mobile app security
•
0 j'aime•57 vues
This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Tendances
Tendances (20)
Deutsche Telekom Partnering Operating Alliance Summit - Zimperium

Deutsche Telekom Partnering Operating Alliance Summit - Zimperium
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

How Aligned Are IT, Employees and Security Practices in Today's Mobile World?
Lookout Mobile Endpoint Security Datasheet (US - v2.5)

Lookout Mobile Endpoint Security Datasheet (US - v2.5)
Symantec Internet Security Threat Report 2014 - Volume 19

Symantec Internet Security Threat Report 2014 - Volume 19
Digital security update: 10 cybersecurity and privacy threats

Digital security update: 10 cybersecurity and privacy threats
Similaire à The state of mobile app security
Similaire à The state of mobile app security (20)
Infographic: Mobile is growing and so are security threats

Infographic: Mobile is growing and so are security threats
Mobile Application Security Testing, Testing for Mobility App | www.idexcel.com

Mobile Application Security Testing, Testing for Mobility App | www.idexcel.com
Protect Your Enterprise - Check Point SandBlast Mobile

Protect Your Enterprise - Check Point SandBlast Mobile
Mobile Security: Perceptions vs Device-harvested Reality

Mobile Security: Perceptions vs Device-harvested Reality
Dernier
Dernier (20)
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
The state of mobile app security
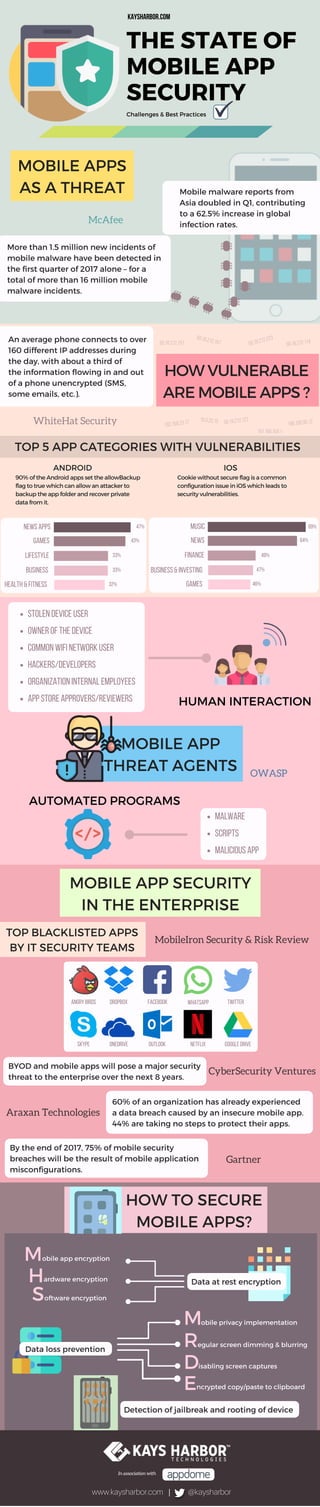
- 1. Data at rest encryption In association with Detection of jailbreak and rooting of device obile app encryption obile privacy implementation M M R D E H S ardware encryption egular screen dimming & blurring isabling screen captures ncrypted copy/paste to clipboard oftware encryption Challenges & Best Practices KAysharbor.com THE STATE OF MOBILE APP SECURITY MOBILE APP THREAT AGENTS MOBILE APP SECURITY IN THE ENTERPRISE TOP 5 APP CATEGORIES WITH VULNERABILITIES TOP BLACKLISTED APPS BY IT SECURITY TEAMS MOBILE APPS AS A THREAT HOW VULNERABLE ARE MOBILE APPS ? ANDROID IOS HUMAN INTERACTION AUTOMATED PROGRAMS 50.19.212.127 192.168.23.17 More than 1.5 million new incidents of mobile malware have been detected in the first quarter of 2017 alone – for a total of more than 16 million mobile malware incidents. BYOD and mobile apps will pose a major security threat to the enterprise over the next 8 years. By the end of 2017, 75% of mobile security breaches will be the result of mobile application misconfigurations. 60% of an organization has already experienced a data breach caused by an insecure mobile app. 44% are taking no steps to protect their apps. Araxan Technologies CyberSecurity Ventures MobileIron Security & Risk Review Gartner ANGRYBIRDS DROPBOX FACEBOOK WHATSAPP TWITTER SKYPE OneDrive OUTLOOK NETFLIX GOOGLEDRIVE MALWARE SCRIPTS MALICIOUSAPP An average phone connects to over 160 different IP addresses during the day, with about a third of the information flowing in and out of a phone unencrypted (SMS, some emails, etc.). 90% of the Android apps set the allowBackup flag to true which can allow an attacker to backup the app folder and recover private data from it. Cookie without secure flag is a common configuration issue in iOS which leads to security vulnerabilities. 50.18.212.157 Mobile malware reports from Asia doubled in Q1, contributing to a 62.5% increase in global infection rates. McAfee WhiteHat Security NEWSAPPS GAMES LIFESTYLE BUSINESS HEALTH&FITNESS 50.18.212.157 50.18.212.223 50.18.212.114 47% 69% 64%43% 33% 33% 32% 198.100.95.1210.0.20.15 191.168.154.1 MUSIC NEWS FINANCE BUSINESS&INVESTING GAMES 49% 47% 46% StolendeviceuseR Ownerofthedevice Commonwifinetworkuser HACKERS/DEVELOPERS Organizationinternalemployees Appstoreapprovers/reviewers OWASP HOW TO SECURE MOBILE APPS? Data loss prevention www.kaysharbor.com @kaysharbor|
