Manage network security with pfSense OpenVPN and IPsec VPN
•
0 j'aime•136 vues
What is Open VPN? Refer this Handout from Tetranoodle Technologies course to know more about PfSense and its usage. For More Information visit Tetranoodle Technologies -- http://rite.ly/wa61 Website: https://courses.tetranoodle.com/ Facebook: https://www.facebook.com/tetranoodletech Twitter: https://twitter.com/TETRANOODLE Linkedin: https://www.linkedin.com/company/tetranoodle/ YouTube:https://www.youtube.com/channel/UCAiIK20nDamhq70NMnLG8wA Instagram: https://www.instagram.com/tetranoodle/ Udemy: https://www.udemy.com/user/manujaggarwal
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Tendances
Tendances (19)
Site-to-Site IPSEC VPN Between Cisco ASA and Pfsense

Site-to-Site IPSEC VPN Between Cisco ASA and Pfsense
Basic Cisco 800 Router Configuration for Internet Access

Basic Cisco 800 Router Configuration for Internet Access
MariaDB in Debian and Ubuntu: The next million users

MariaDB in Debian and Ubuntu: The next million users
Plus de Manuj Aggarwal
Plus de Manuj Aggarwal (6)
IaaS Cloud Computing With OpenStack - Master Class (Handout)

IaaS Cloud Computing With OpenStack - Master Class (Handout)
Dernier
Dernier (20)
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Manage network security with pfSense OpenVPN and IPsec VPN
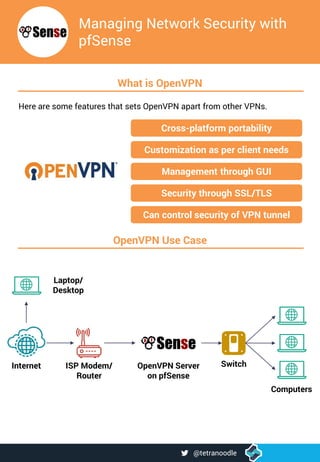
- 1. Managing Network Security with pfSense What is OpenVPN Here are some features that sets OpenVPN apart from other VPNs. Cross-platform portability Customization as per client needs Management through GUI Security through SSL/TLS Can control security of VPN tunnel OpenVPN Use Case ISP Modem/ Router Internet Switch Computers OpenVPN Server on pfSense Laptop/ Desktop @tetranoodle
- 2. Managing Network Security with pfSense IPsec VPN Tunnel Use Case Authentication Integrity Confidentiality IPsec Features Here are the key features of IPsec. ISP Modem/ Router Internet Switch 1 (WAN) Computers Switch 2 (LAN) Computers ISP Modem/ Router Site A 192.168.1.0/24 Site B 192.168.2.0/24 @tetranoodle