MCAS High Level Architecture May 2021
•Télécharger en tant que PPTX, PDF•
3 j'aime•2,653 vues
High level architecture of Microsoft Cloud App Security see the following video for more information: https://youtu.be/omRP3EPJzmA
Signaler
Partager
Signaler
Partager
Recommandé
Here's the slide deck from my session titled "Secure your Access to Cloud Apps using Microsoft Defender for Cloud Apps" which was presented on the Modern Workplace Conference Paris 2022 Virtual event. Secure your Access to Cloud Apps using Microsoft Defender for Cloud Apps

Secure your Access to Cloud Apps using Microsoft Defender for Cloud AppsVignesh Ganesan I Microsoft MVP
Recommandé
Here's the slide deck from my session titled "Secure your Access to Cloud Apps using Microsoft Defender for Cloud Apps" which was presented on the Modern Workplace Conference Paris 2022 Virtual event. Secure your Access to Cloud Apps using Microsoft Defender for Cloud Apps

Secure your Access to Cloud Apps using Microsoft Defender for Cloud AppsVignesh Ganesan I Microsoft MVP
Contenu connexe
Tendances
Tendances (20)
Microsoft Intune - Empowering Enterprise Mobility - Presented by Atidan 

Microsoft Intune - Empowering Enterprise Mobility - Presented by Atidan
An introduction to Office 365 Advanced Threat Protection (ATP)

An introduction to Office 365 Advanced Threat Protection (ATP)
Introduction to Microsoft Enterprise Mobility + Security

Introduction to Microsoft Enterprise Mobility + Security
Overview of Microsoft Enterprise Mobility & Security(EMS)

Overview of Microsoft Enterprise Mobility & Security(EMS)
SCCM Intune Windows 10 Co Management Architecture Decisions

SCCM Intune Windows 10 Co Management Architecture Decisions
Power of the cloud - Introduction to azure security

Power of the cloud - Introduction to azure security
Similaire à MCAS High Level Architecture May 2021
Similaire à MCAS High Level Architecture May 2021 (20)
Softchoice & Microsoft: Public Cloud Security Webinar

Softchoice & Microsoft: Public Cloud Security Webinar
microsoft-cybersecurity-reference-architectures (1).pptx

microsoft-cybersecurity-reference-architectures (1).pptx
Xylos Clients Day - Public cloud and security go hand in hand, if you approac...

Xylos Clients Day - Public cloud and security go hand in hand, if you approac...
Fundamentals of Microsoft 365 Security , Identity and Compliance

Fundamentals of Microsoft 365 Security , Identity and Compliance
Combatting Cyberthreats with Microsoft Defender 365 - CollabDays Finland 2023

Combatting Cyberthreats with Microsoft Defender 365 - CollabDays Finland 2023
Identity-Driven Security with Forsyte I.T. Solutions - Demos and Discovery

Identity-Driven Security with Forsyte I.T. Solutions - Demos and Discovery
3 Modern Security - Secure identities to reach zero trust with AAD

3 Modern Security - Secure identities to reach zero trust with AAD
Build a complete security operations and compliance program using a graph dat...

Build a complete security operations and compliance program using a graph dat...
Building Automated Governance Using Code, Platform Services & Several Small P...

Building Automated Governance Using Code, Platform Services & Several Small P...
AWS Webcast - Top 3 Ways to Improve Web App Security

AWS Webcast - Top 3 Ways to Improve Web App Security
Nicholas DiCola | Secure your IT resources with Azure Security Center

Nicholas DiCola | Secure your IT resources with Azure Security Center
Dernier
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Dernier (20)
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
MCAS High Level Architecture May 2021
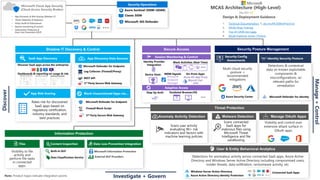
- 1. Microsoft Endpoint Manager Azure AD App Proxy Beyond User VPN Block Activities (Real-Time) Visibility to file activity and perform file tasks in connected apps. • App Discovery & Risk Scoring (Shadow IT) • Threat Detection & Response • Policy Audit & Enforcement • Session monitoring & control • Information Protection & Data Loss Prevention (DLP) Microsoft Cloud App Security (Cloud Access Security Broker) Technical Documentation 5. aka.ms/MCASBestPractices MCAS Ninja Training Top 20 CASB Use Cases MCAS Explainer Series (15mins) Visibility and control over extensive attack surface in OAuth apps Detections for anomalous activity across connected SaaS apps, Azure Active Directory and Windows Server Active Directory including compromised users, insider threats, data exfiltration, ransomware activity, etc. Investigate + Govern Manage + Control Rates risk for discovered SaaS apps based on regulatory certification, industry standards, and best practices Discover Multi-cloud security posture + recommended mitigations Detections & contextual data on known exploitable components & misconfigurations, w/ relevant paths for remediation
Notes de l'éditeur
- As of 5/4/2021: 94 risk factors, 20 Out of the Box Threat Protection policies, 17744 cloud apps in app catalog, 207 sensitive information types