Sept 2019 - DSO-LG Tooling Examples
•Télécharger en tant que PPTX, PDF•
0 j'aime•324 vues
This is obviously not everything in the industry. The slide gives you a taster of what's out there. Disclaimer: DevSecOps - London Gathering is not endorsing any of these products. Michael Man may have experience with some of them and is happy to share his view.
Signaler
Partager
Signaler
Partager
Recommandé
Managing Open Source in Application Security and Software Development Lifecycle

Managing Open Source in Application Security and Software Development LifecycleBlack Duck by Synopsys
Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...

Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...North Texas Chapter of the ISSA
Contenu connexe
Tendances
Managing Open Source in Application Security and Software Development Lifecycle

Managing Open Source in Application Security and Software Development LifecycleBlack Duck by Synopsys
Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...

Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...North Texas Chapter of the ISSA
Tendances (20)
Under-reported Security Defects in Kubernetes Manifests

Under-reported Security Defects in Kubernetes Manifests
Threat-Modeling-as-Code: ThreatPlaybook AppSecUSA 2018 Presentation

Threat-Modeling-as-Code: ThreatPlaybook AppSecUSA 2018 Presentation
Application Security Logging with Splunk using Java

Application Security Logging with Splunk using Java
Sec4dev 2021 - Catch Me If You can : Continuous Delivery vs. Security Assurance

Sec4dev 2021 - Catch Me If You can : Continuous Delivery vs. Security Assurance
BOMs Away - Why everyone needs a BOM (AppSec Cali 2019)

BOMs Away - Why everyone needs a BOM (AppSec Cali 2019)
Managing Open Source in Application Security and Software Development Lifecycle

Managing Open Source in Application Security and Software Development Lifecycle
Improving the quality of Cyber Security Hires via Pre-Interview Challenges 

Improving the quality of Cyber Security Hires via Pre-Interview Challenges
Shhh!: Secret Management Practices for Infrastructure as Code 

Shhh!: Secret Management Practices for Infrastructure as Code
Secure Application Development in the Age of Continuous Delivery

Secure Application Development in the Age of Continuous Delivery
Continuous and Visible Security Testing with BDD-Security

Continuous and Visible Security Testing with BDD-Security
Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...

Luncheon 2015-01-15 - Managing Security Requirements in Software Projects by ...
Why Security Engineer Need Shift-Left to DevSecOps?

Why Security Engineer Need Shift-Left to DevSecOps?
Security DevOps - Staying secure in agile projects // OWASP AppSecEU 2015 - A...

Security DevOps - Staying secure in agile projects // OWASP AppSecEU 2015 - A...
Similaire à Sept 2019 - DSO-LG Tooling Examples
Leverage DevOps & Agile Development to Transform Your Application Testing Pro...

Leverage DevOps & Agile Development to Transform Your Application Testing Pro...DevOps for Enterprise Systems
Similaire à Sept 2019 - DSO-LG Tooling Examples (20)
Filling your AppSec Toolbox - Which Tools, When to Use Them, and Why

Filling your AppSec Toolbox - Which Tools, When to Use Them, and Why
Cyber Security Conference - Praktiske erfaringer med Implementering af Cyber ...

Cyber Security Conference - Praktiske erfaringer med Implementering af Cyber ...
The automated (ethical) hacker in you - test automation day nl 2018

The automated (ethical) hacker in you - test automation day nl 2018
Leverage DevOps & Agile Development to Transform Your Application Testing Pro...

Leverage DevOps & Agile Development to Transform Your Application Testing Pro...
Leverage DevOps & Agile Development to Transform Your Application Testing Pro...

Leverage DevOps & Agile Development to Transform Your Application Testing Pro...
Leverage DevOps & Agile Development to Transform Your Application Testing Pro...

Leverage DevOps & Agile Development to Transform Your Application Testing Pro...
Application Security Testing for Software Engineers ,Developers and testers

Application Security Testing for Software Engineers ,Developers and testers
Continuous Application Security at Scale with IAST and RASP -- Transforming D...

Continuous Application Security at Scale with IAST and RASP -- Transforming D...
Plus de Michael Man
Plus de Michael Man (20)
5 things i wish i knew about sast (DSO-LG July 2021)

5 things i wish i knew about sast (DSO-LG July 2021)
DSO-LG 2021 Reboot: Policy As Code (Anders Eknert)

DSO-LG 2021 Reboot: Policy As Code (Anders Eknert)
DSO-LG March 2018: The mechanics behind how attackers exploit simple programm...

DSO-LG March 2018: The mechanics behind how attackers exploit simple programm...
DSO-LG Oct 2019: Modern Software Delivery: Supply Chain Security Critical (Ch...

DSO-LG Oct 2019: Modern Software Delivery: Supply Chain Security Critical (Ch...
Extract: DevSecOps - London Gathering (March 2019)

Extract: DevSecOps - London Gathering (March 2019)
Control Plane: Security Rationale for Istio (DevSecOps - London Gathering, Ja...

Control Plane: Security Rationale for Istio (DevSecOps - London Gathering, Ja...
Matt Turner: Istio, The Packet's-Eye View (DevSecOps - London Gathering, Janu...

Matt Turner: Istio, The Packet's-Eye View (DevSecOps - London Gathering, Janu...
Control Plane: Continuous Kubernetes Security (DevSecOps - London Gathering, ...

Control Plane: Continuous Kubernetes Security (DevSecOps - London Gathering, ...
Continuous Security: From tins to containers - now what!

Continuous Security: From tins to containers - now what!
The mechanics behind how attackers exploit simple programming mistakes ...

The mechanics behind how attackers exploit simple programming mistakes ...
Secret Management Journey - Here Be Dragons aka Secret Dragons

Secret Management Journey - Here Be Dragons aka Secret Dragons
Dernier
Dernier (20)
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Sept 2019 - DSO-LG Tooling Examples
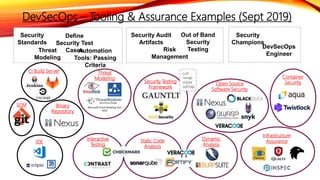
- 1. IDE Static Code Analysis SCM Dynamic Analysis Open Source Software Security Security Testing Framework Binary Repository Define Security Test CasesThreat Modeling Security Standards Automation Tools: Passing Criteria Risk Management Out of Band Security Testing Security Champions DevSecOps Engineer Security Audit Artifacts CI Build Server DevSecOps – Tooling & Assurance Examples (Sept 2019) curl nmap sslyze sqlmap Interactive Testing Threat Modeling Container Security Infrastructure Assurance
- 2. Dev Workstation Build Server Centralize Report (Vulnerability Management) Server SCM Static Code Analysis (SAST) Dynamic Testing (DAST) Interactive Testing (IAST) Open Source Component Security Manual Penetration Testing – Out of Band Scope: Application and Network layer – White/Black box Defect Management AUTOMATION INTEGRATION POINTS SECURITYASSURANCEMODEL Updated: May 2019 Container Security Infrastructure Scanning