ECSM 2021 - Sfaturi pentru a te proteja în mediul online
•
0 j'aime•14 vues
Sfaturi pentru a te proteja în mediul online - Luna europeană a securității cibernetice 2021 Think Before U Click
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Contenu connexe
Tendances
Tendances (20)
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...
Don't ask, don't tell the virtues of privacy by design

Don't ask, don't tell the virtues of privacy by design
How to incrementally improve Sanctions Screening with AI

How to incrementally improve Sanctions Screening with AI
Similaire à ECSM 2021 - Sfaturi pentru a te proteja în mediul online
Similaire à ECSM 2021 - Sfaturi pentru a te proteja în mediul online (20)
DIgital Citizenship for Parents of Middle School Students

DIgital Citizenship for Parents of Middle School Students
MindMake - Online Safety Talking to your Kids Parental Control

MindMake - Online Safety Talking to your Kids Parental Control
Girls security abuse - social media - security tips.arise raabi - pdf

Girls security abuse - social media - security tips.arise raabi - pdf
Cyber Safety How Children Can Protect Themselves From Online Threats

Cyber Safety How Children Can Protect Themselves From Online Threats
Plus de One-IT
Plus de One-IT (20)
Centralizator întrebări și răspunsuri Digitalizare IMM.doc

Centralizator întrebări și răspunsuri Digitalizare IMM.doc
Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf

Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf
Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx

Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx
Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022

Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022
Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf

Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf
Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx

Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx
Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...

Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...
Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022

Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022
Cum te protejezi de tentativele de tip scam în business

Cum te protejezi de tentativele de tip scam în business
ECSM 2021- Informații importante despre amprenta ta digitală

ECSM 2021- Informații importante despre amprenta ta digitală
Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...

Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...
Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...

Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...
One-IT - prezentare GDPR-ul si Protectia datelor personale

One-IT - prezentare GDPR-ul si Protectia datelor personale
Dernier
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Dernier (20)
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
ECSM 2021 - Sfaturi pentru a te proteja în mediul online
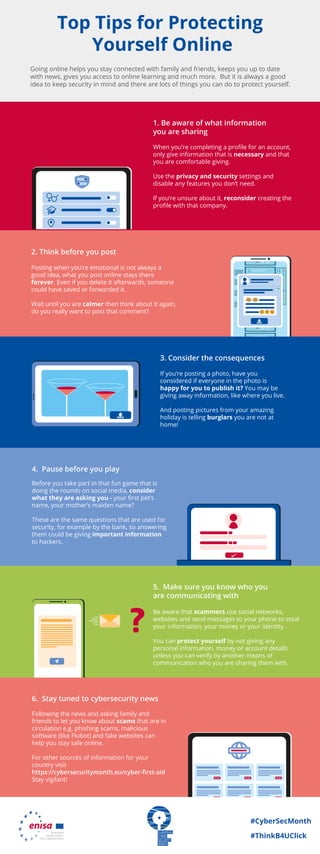
- 1. #CyberSecMonth #ThinkB4UClick ? When you’re completing a profile for an account, only give information that is necessary and that you are comfortable giving. Use the privacy and security settings and disable any features you don’t need. If you’re unsure about it, reconsider creating the profile with that company. 1. Be aware of what information you are sharing Posting when you’re emotional is not always a good idea, what you post online stays there forever. Even if you delete it afterwards, someone could have saved or forwarded it. Wait until you are calmer then think about it again, do you really want to post that comment? 2. Think before you post If you’re posting a photo, have you considered if everyone in the photo is happy for you to publish it? You may be giving away information, like where you live. And posting pictures from your amazing holiday is telling burglars you are not at home! 3. Consider the consequences Before you take part in that fun game that is doing the rounds on social media, consider what they are asking you - your first pet’s name, your mother’s maiden name? These are the same questions that are used for security, for example by the bank, so answering them could be giving important information to hackers. 4. Pause before you play Following the news and asking family and friends to let you know about scams that are in circulation e.g. phishing scams, malicious software (like Flubot) and fake websites can help you stay safe online. For other sources of information for your country visit https://cybersecuritymonth.eu/cyber-first-aid Stay vigilant! 6. Stay tuned to cybersecurity news Be aware that scammers use social networks, websites and send messages to your phone to steal your information, your money or your identity. You can protect yourself by not giving any personal information, money or account details unless you can verify by another means of communication who you are sharing them with. 5. Make sure you know who you are communicating with Going online helps you stay connected with family and friends, keeps you up to date with news, gives you access to online learning and much more. But it is always a good idea to keep security in mind and there are lots of things you can do to protect yourself. Top Tips for Protecting Yourself Online
