Consumer Attitudes in a Post-breach Era: The Geographical Gap
•
1 j'aime•915 vues
Ping Identity’s consumer survey on security perceptions and behavior revealed significant differences between residents of the U.S., France, Germany and the UK. Some are more carefree with their information, while others have less trust in brands.
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
2015 TRUSTe US Consumer Privacy Confidence Index – Infographic

2015 TRUSTe US Consumer Privacy Confidence Index – Infographic
Its 2019 - Should Pharma Still Be Scared of Digital?

Its 2019 - Should Pharma Still Be Scared of Digital?
TeleSign’s Findings on the Future of Digital Identity, Guillaume Bourcy

TeleSign’s Findings on the Future of Digital Identity, Guillaume Bourcy
TRUSTe 2014 US Consumer Confidence Privacy Report Consumer Opinion and Busine...

TRUSTe 2014 US Consumer Confidence Privacy Report Consumer Opinion and Busine...
Infographic: Philippines B2C E-Commerce Market 2019

Infographic: Philippines B2C E-Commerce Market 2019
Aligning Today's IT with the Future of Government - Peter Pin

Aligning Today's IT with the Future of Government - Peter Pin
Similaire à Consumer Attitudes in a Post-breach Era: The Geographical Gap
Similaire à Consumer Attitudes in a Post-breach Era: The Geographical Gap (20)
Moving beyond passwords - Consumer attitudes on online authentication

Moving beyond passwords - Consumer attitudes on online authentication
TeleSign Consumer Account Security Report 2015 FINAL

TeleSign Consumer Account Security Report 2015 FINAL
Delivering Imperatives of Modern Organizations Such As Cybersecurity and Open...

Delivering Imperatives of Modern Organizations Such As Cybersecurity and Open...
Consumer Mobile Policy & Security - Lightspeed & Kantar

Consumer Mobile Policy & Security - Lightspeed & Kantar
White Paper: The 2015 State of Consumer Privacy & Personalization

White Paper: The 2015 State of Consumer Privacy & Personalization
White Paper: The 2015 State of Consumer Privacy & Personalization

White Paper: The 2015 State of Consumer Privacy & Personalization
Chinese Social Credit Score: Utopian Big Data Bliss Or Black Mirror On Steroids?

Chinese Social Credit Score: Utopian Big Data Bliss Or Black Mirror On Steroids?
Data Privacy Compliance (Series: Corporate & Regulatory Compliance Bootcamp)

Data Privacy Compliance (Series: Corporate & Regulatory Compliance Bootcamp)
Adobe Digital Insights -- Diversity In Advertising 2019 (AUS)

Adobe Digital Insights -- Diversity In Advertising 2019 (AUS)
Plus de Ping Identity
Plus de Ping Identity (20)
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

Standard Based API Security, Access Control and AI Based Attack - API Days Pa...
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

Fishing for a CIAM Platform? 11 Question to Ask Before You Buy
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

Webinar: Three Steps to Transform Your Mobile App into a Security Factor
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass
GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance

GDPR & Customer IAM: The Real Winners Won’t Stop At Compliance
Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...

Gartner IAM London 2017 Session - Security, Standards & User Experience: The ...
Dernier
Dernier (20)
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu

Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu
Consumer Attitudes in a Post-breach Era: The Geographical Gap
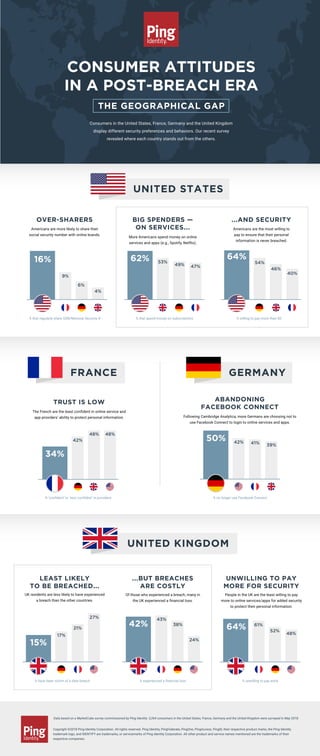
- 1. CONSUMER ATTITUDES IN A POST-BREACH ERA THE GEOGRAPHICAL GAP OVER-SHARERS Americans are more likely to share their social security number with online brands. % that regularly share SSN/National Security # % ‘confident’ or ‘very confident’ in providers % have been victim of a data breach % experienced a financial loss % unwilling to pay extra % no longer use Facebook Connect % that spend money on subscriptions % willing to pay more than $0 Consumers in the United States, France, Germany and the United Kingdom display different security preferences and behaviors. Our recent survey revealed where each country stands out from the others. Data based on a MarketCube survey commissioned by Ping Identity. 3,264 consumers in the United States, France, Germany and the United Kingdom were surveyed in May 2018. Copyright ©2018 Ping Identity Corporation. All rights reserved. Ping Identity, PingFederate, PingOne, PingAccess, PingID, their respective product marks, the Ping Identity trademark logo, and IDENTIFY are trademarks, or servicemarks of Ping Identity Corporation. All other product and service names mentioned are the trademarks of their respective companies. 16% 34% 9% 6% 4% 62% BIG SPENDERS — ON SERVICES... More Americans spend money on online services and apps (e.g., Spotify, Netflix). ...AND SECURITY Americans are the most willing to pay to ensure that their personal information is never breached. LEAST LIKELY TO BE BREACHED... UK residents are less likely to have experienced a breach than the other countries. ...BUT BREACHES ARE COSTLY Of those who experienced a breach, many in the UK experienced a financial loss. UNWILLING TO PAY MORE FOR SECURITY People in the UK are the least willing to pay more to online services/apps for added security to protect their personal information. TRUST IS LOW The French are the least confident in online service and app providers’ ability to protect personal information. ABANDONING FACEBOOK CONNECT Following Cambridge Analytica, more Germans are choosing not to use Facebook Connect to login to online services and apps. 64% 54% 46% 40% 53% 49% 47% 42% 48% 48% 42% 41% 39% 50% 15% 27% 21% 17% 42% 24% 38% 43% 64% 61% 52% 48% UNITED KINGDOM FRANCE UNITED STATES GERMANY
