Overview of Recorded Future Intel Cards
•
9 j'aime•6,633 vues
Recorded Future Intel Cards provide actionable threat intelligence data neatly curated by investigation topic and presented in a comprehensive single view, saving analysts time otherwise spent connecting the dots themselves. The six Intel Card types are IP Address, Domain, Hash, Vulnerability, Malware, and Threat Actor.
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
All about Firewalls ,IPS IDS and the era of UTM in a nutshell

All about Firewalls ,IPS IDS and the era of UTM in a nutshell
How to Spot and Combat a Phishing Attack - Cyber Security Webinar | ControlScan

How to Spot and Combat a Phishing Attack - Cyber Security Webinar | ControlScan
Threat Hunting - Moving from the ad hoc to the formal

Threat Hunting - Moving from the ad hoc to the formal
Security Operations Center (SOC) Essentials for the SME

Security Operations Center (SOC) Essentials for the SME
Empower Your Security Practitioners with Elastic SIEM

Empower Your Security Practitioners with Elastic SIEM
Cyber Security For Organization Proposal PowerPoint Presentation Slides

Cyber Security For Organization Proposal PowerPoint Presentation Slides
En vedette
En vedette (15)
Going Purple : From full time breaker to part time fixer: 1 year later 

Going Purple : From full time breaker to part time fixer: 1 year later
Incorporating the Data Lake into Your Analytic Architecture

Incorporating the Data Lake into Your Analytic Architecture
Threat Intelligence Tweaks That'll Take Your Security to the Next Level

Threat Intelligence Tweaks That'll Take Your Security to the Next Level
Proactive Defense: Understanding the 4 Main Threat Actor Types

Proactive Defense: Understanding the 4 Main Threat Actor Types
Using Canary Honeypots for Network Security Monitoring

Using Canary Honeypots for Network Security Monitoring
Palantir, Quid, RecordedFuture: Augmented Intelligence Frontier

Palantir, Quid, RecordedFuture: Augmented Intelligence Frontier
Applied Detection and Analysis Using Flow Data - MIRCon 2014

Applied Detection and Analysis Using Flow Data - MIRCon 2014
Developing Analytic Technique and Defeating Cognitive Bias in Security

Developing Analytic Technique and Defeating Cognitive Bias in Security
Information Virtualization: Query Federation on Data Lakes

Information Virtualization: Query Federation on Data Lakes
Similaire à Overview of Recorded Future Intel Cards
Similaire à Overview of Recorded Future Intel Cards (20)
INFORMATION SECURITY MANAGEMENT - Critique the employment of ethical hacking ...

INFORMATION SECURITY MANAGEMENT - Critique the employment of ethical hacking ...
Deep Learning based Threat / Intrusion detection system

Deep Learning based Threat / Intrusion detection system
Invesitigation of Malware and Forensic Tools on Internet 

Invesitigation of Malware and Forensic Tools on Internet
Insight Brief: Security Analytics to Identify the 12 Indicators of Compromise

Insight Brief: Security Analytics to Identify the 12 Indicators of Compromise
Lessons v on fraud awareness (digital forensics) [autosaved]![Lessons v on fraud awareness (digital forensics) [autosaved]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Lessons v on fraud awareness (digital forensics) [autosaved]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Lessons v on fraud awareness (digital forensics) [autosaved]
Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...

Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...
Digital Shadows and the NIST Cyber Security Framework

Digital Shadows and the NIST Cyber Security Framework
Dernier
Dernier (20)
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Overview of Recorded Future Intel Cards
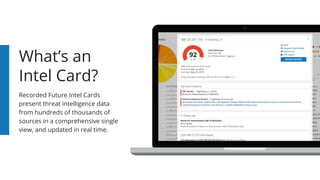
- 1. What’s an Intel Card? Recorded Future Intel Cards present threat intelligence data from hundreds of thousands of sources in a comprehensive single view, and updated in real time.
- 3. Time Is Crucial When it comes to cyber investigations, time management is critical. Security teams gain instant context around suspicious observables and indicators with Recorded Future Intel Cards — with one click. Intel Cards are organized in a consolidated view, dramatically increasing the speed and efficiency of threat research and analysis.
- 4. Intel Card Types Intel Cards are divided into six investigation types, with more on the way. The breadth of our real-time data collection and analysis is unrivaled. IP Address Domain Hash Vulnerability Threat Actor Malware
- 5. Data Exports Share Links Threat Lists Timelines Extensions Intel Card Features Intel Card data is harvested from hundreds of thousands of sources on the open, deep, and dark web, as well as threat feeds, technical collection, and security reporting. Risk Scores
- 6. Header When first accessing an Intel Card, you can observe the precise entity name along with its pseudonyms, the first and last date that reporting was observed, and the references related to the entity. You can also export the entity data.
- 7. Header When first accessing an Intel Card, you can observe the precise entity name along with its pseudonyms, the first and last date that reporting was observed, and the references related to the entity. You can also export the entity data.
- 8. Header When first accessing an Intel Card, you can observe the precise entity name along with its pseudonyms, the first and last date that reporting was observed, and the references related to the entity. You can also export the entity data.
- 9. Header When first accessing an Intel Card, you can observe the precise entity name along with its pseudonyms, the first and last date that reporting was observed, and the references related to the entity. You can also export the entity data.
- 10. Header When first accessing an Intel Card, you can observe the precise entity name along with its pseudonyms, the first and last date that reporting was observed, and the references related to the entity. You can also export the entity data.
- 11. Header Malware Intel Cards display the malware category in the header. Threat Actor Intel Cards display the country the hacker group is associated with, as well as any related usernames and email addresses.
- 12. Header Malware Intel Cards display the malware category in the header. Threat Actor Intel Cards display the country the hacker group is associated with, as well as any related usernames and email addresses.
- 13. Header Malware Intel Cards display the malware category in the header. Threat Actor Intel Cards display the country the hacker group is associated with, as well as any related usernames and email addresses.
- 14. Risk Score Risk score ratings are based on a set of risk rules and report the severity level of an entity from zero to 99. Each risk rule trigger is based on specific, collected evidence and is available for the IP Address, Hash, and Vulnerability Intel Cards.
- 15. Risk Score Risk score ratings are based on a set of risk rules and report the severity level of an entity from zero to 99. Each risk rule trigger is based on specific, collected evidence and is available for the IP Address, Hash, and Vulnerability Intel Cards.
- 16. Threat Lists A specific entity is listed here upon showing up in one or more threat lists. Updates are tracked by Recorded Future daily or even more frequently. Any removals of the specific entity from an external threat list are reflected in entity threat list rules.
- 17. Threat Lists A specific entity is listed here upon showing up in one or more threat lists. Updates are tracked by Recorded Future daily or even more frequently. Any removals of the specific entity from an external threat list are reflected in entity threat list rules.
- 18. Recent Event Timelines Primary timelines show an entity’s reporting in the last 60 days. Malware, Threat Actor, and Vulnerability Intel Cards may display a secondary timeline with reported cyber attack and exploit events. Most Threat Actor Intel Cards display two.
- 19. Recent Event Timelines Primary timelines show an entity’s reporting in the last 60 days. Malware, Threat Actor, and Vulnerability Intel Cards may display a secondary timeline with reported cyber attack and exploit events. Most Threat Actor Intel Cards display two.
- 20. Recent Event Timelines Primary timelines show an entity’s reporting in the last 60 days. Malware, Threat Actor, and Vulnerability Intel Cards may display a secondary timeline with reported cyber attack and exploit events. Most Threat Actor Intel Cards display two.
- 21. Targeting and Operations Threat Actor Intel Cards summarize methods, targets, and operations from cyber attack events. When the threat actor is directly reported as the attacker of an event, further information can be accessed by clicking any top related entity.
- 22. Targeting and Operations Threat Actor Intel Cards summarize methods, targets, and operations from cyber attack events. When the threat actor is directly reported as the attacker of an event, further information can be accessed by clicking any top related entity.
- 23. Related Entities (Context) Alternate entities that have been reported in relation to a primary entity are summarized in related entities lists. For Malware Intel Cards, related email addresses will be listed here, which can be helpful in identifying relevant online personas.
- 24. Related Entities (Context) Alternate entities that have been reported in relation to a primary entity are summarized in related entities lists. For Malware Intel Cards, related email addresses will be listed here, which can be helpful in identifying online personas.
- 25. Subdomains The Domain Intel Card type shows summaries of the parent domain, siblings, and DNS names within a domain. Once discovered by Recorded Future, every subdomain that shares the same registered domain name is listed here, along with its references.
- 26. Subdomains The Domain Intel Card type shows summaries of the parent domain, siblings, and DNS names within a domain. Once discovered by Recorded Future, every subdomain that shares the same registered domain name is listed here, along with its references.
- 27. Technical Profile and Enrichment Service Links Navigation links for enrichment services are included in an entity’s Intel Card profile. DomainTools, Shodan, and VirusTotal are among the resource links available.
- 28. Technical Profile and Enrichment Service Links Navigation links for enrichment services are included in an entity’s Intel Card profile. DomainTools, Shodan, and VirusTotal are among the resource links available.
- 29. Technical Profile and Enrichment Service Links Navigation links for enrichment services are included in an entity’s Intel Card profile. DomainTools, Shodan, and VirusTotal are among the resource links available.
- 30. Recent References and First Reference First and recent references provide context for threat investigations. A large increase in recent references may indicate an emerging threat or a new tactic/exploit.
- 31. Recent References and First Reference First and recent references provide context for threat investigations. A large increase in recent references may indicate an emerging threat or a new tactic/exploit.
- 32. Intel Card Extensions Recorded Future OMNI Intelligence Partners provide complementary information for our Intel Cards, maximizing the value of research.
- 33. How Do Teams Use Intel Cards? Rapidly research vulnerabilities with speed and confidence. Threat Intelligence Methodically automate correlation rules with dynamic risk scoring. Security Operations Effectively react to attacks with complete threat context. Incident Response
- 34. Consolidated Intelligence There are massive numbers of external threat intelligence sources, but attempting to find and collate information manually will prove inefficient at best and potentially fruitless. Our Intel Cards present this real-time threat intelligence in a single view, unifying thousands of data points — so you can increase productivity and be more effective in your role.
- 35. Request a Demo Confidently detect important incidents you would have otherwise missed using real-time threat intelligence. Request a demo of our Intel Cards now: www.recordedfuture.com
