Verizon DBIR 2021
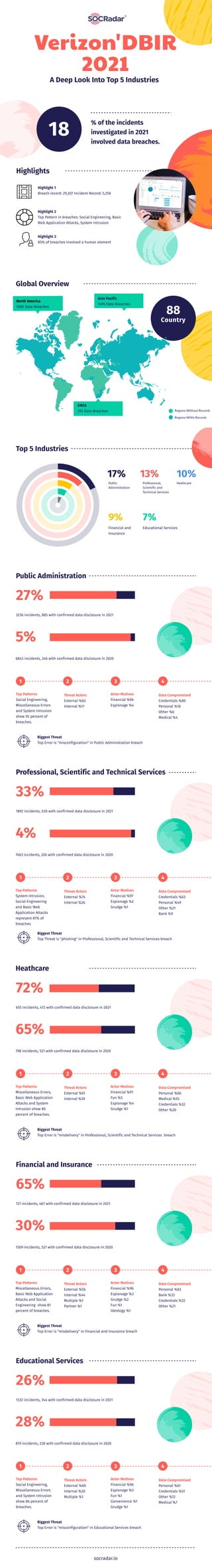
- 1. Highlight 1 Breach record: 29,207 Incident Record: 5,258 Highlight 2 Top Pattern in breaches: Social Engineering, Basic Web Application Attacks, System Intrusion % of the incidents investigated in 2021 involved data breaches. Highlights 18 Highlight 3 85% of breaches involved a human element Verizon'DBIR 2021 A Deep Look Into Top 5 Industries Global Overview North America 1080 Data Breaches Asia Pasific 1495 Data Breaches Country 88 EMEA 293 Data Breaches Regions Without Records Regions Witht Records Top 5 Industries 17% Public Administration 13% 9% 7% Professional, Scientific and Technical Services Financial and Insurance Educational Services 10% Heathcare Public Administration 27% 5% 3236 incidents, 885 with confirmed data disclosure in 2021 Top Patterns Social Engineering, Miscellaneous Errors and System Intrusion show 92 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %4 Threat Actors External %83 Internal %17 Data Compromised Credentials %80 Personal %18 Other %6 Medical %4 6843 incidents, 346 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misconfiguration" in Public Administration breach Professional, Scientific and Technical Services 33% 4% 1892 incidents, 630 with confirmed data disclosure in 2021 Top Patterns System Intrusion, Social Engineering and Basic Web Application Attacks represent 81% of breaches 1 2 3 4 Actor Motives Financial %97 Espionage %2 Grudge %1 Threat Actors External %74 Internal %26 Data Compromised Credentials %63 Personal %49 Other %21 Bank %9 7463 incidents, 326 with confirmed data disclosure in 2020 Biggest Threat Top Threat is "phishing" in Professional, Scientific and Technical Services breach Heathcare 72% 65% 655 incidents, 472 with confirmed data disclosure in 2021 Top Patterns Miscellaneous Errors, Basic Web Application Attacks and System Intrusion show 86 percent of breaches. 1 2 3 4 Actor Motives Financial %91 Fun %5 Espionage %4 Grudge %1 Threat Actors External %61 Internal %39 Data Compromised Personal %66 Medical %55 Credentials %32 Other %20 798 incidents, 521 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misdelivery" in Professional, Scientific and Technical Services breach Financial and Insurance 65% 30% 721 incidents, 467 with confirmed data disclosure in 2021 Top Patterns Miscellaneous Errors, Basic Web Application Attacks and Social Engineering show 81 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %3 Grudge %2 Fun %1 Ideology %1 Threat Actors External %56 Internal %44 Multiple %1 Partner %1 Data Compromised Personal %83 Bank %33 Credentials %32 Other %21 1509 incidents, 521 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misdelivery" in Financial and Insurance breach Educational Services 26% 28% 1332 incidents, 344 with confirmed data disclosure in 2021 Top Patterns Social Engineering, Miscellaneous Errors and System Intrusion show 86 percent of breaches. 1 2 3 4 Actor Motives Financial %96 Espionage %3 Fun %1 Convenience %1 Grudge %1 Threat Actors External %80 Internal %20 Multiple %1 Data Compromised Personal %61 Credentials %51 Other %12 Medical %7 819 incidents, 228 with confirmed data disclosure in 2020 Biggest Threat Top Error is "misconfiguration" in Educational Services breach socradar.io
