Third-party Remote Support Threats Inforgraphic
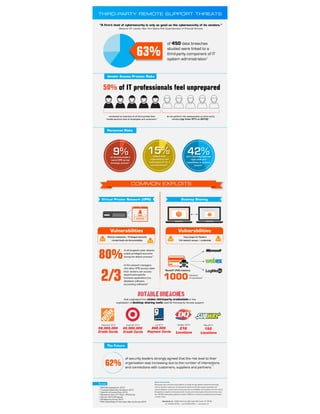
- 1. 62% About SecureLink Businesses rely on the SecureLink platform to bridge the gap between enterprise technology vendors and their customers. The SecureLink solution streamlines support operations and reduces liability for vendors while ensuring security, accountability, and compliance for their clients. Recognized as experts in third party vendor access and remote support, SecureLink serves more than 30,000 organizations globally. Founded in 2003, the company is privately owned and based in Austin, Texas. COMMON EXPLOITS THIRD-PARTY REMOTE SUPPORT THREATS Vendor Access Process Risks of 450 data breaches studied were linked to a third-party component of IT system administration ② of security leaders strongly agreed that the risk level to their organization was increasing due to the number of interactions and connections with customers, suppliers and partners. ① “A firm’s level of cybersecurity is only as good as the cybersecurity of its vendors.” Benjamin M. Lawsky, New York State's first Superintendent of Financial Services ① IBM CISO Assessment, 2014 ② Trustwave Global Security Report, 2013 ③ CyberArk All Access Pass, 2014 ④ Spiceworks Voice of IT Panel - VPN Survey ⑤ Gartner: 2014 CIO Agenda ⑥ EiQ Networks Survey, 2014 ⑦ PWC Global State of Information Security Survey, 2015 Sources: of the network managers who allow VPN access state their vendors can access department-specific business applications (i.e. database software, accounting software)④ “Backoff” (POS malware) of all targeted cyber attacks exploit privileged accounts during the attack process③ November 2013 40,000,000 Credit Cards July 2014 868,000 Payment Cards September 2014 56,000,000 Credit Cards May 2011 150 Locations October 2014 216 Locations 42%don’t feel they have the right skills and capabilities to prevent breach⑤ 9%of security leaders name CPO as top strategic partner① 15%believe their organizations are “well prepared” for a security breach⑥ Vulnerabilities Shared credentials / Privileged accounts Limited Audit and Accountability NOTABLE BREACHES 63% Personnel Risks The Future Virtual Private Network (VPN) Desktop Sharing conducted an inventory of all third parties that handle personal data of employees and customers⑦ do not perform risk assessments on third- party vendors (up from 47% in 2013)⑦ SecureLink, Inc. 12600 Hill Country Blvd. Suite 200, Austin, TX 78738 ofc: 512.637.8700 // fax: 512.637.8701 // securelink.com 50% of IT professionals feel unprepared infections of businesses② 1000 80% 2/3 Vulnerabilities Easy target for Hackers Full network access / credentials that originated from stolen third-party credentials or the exploitation of desktop sharing tools used for third-party remote support.
