Network security
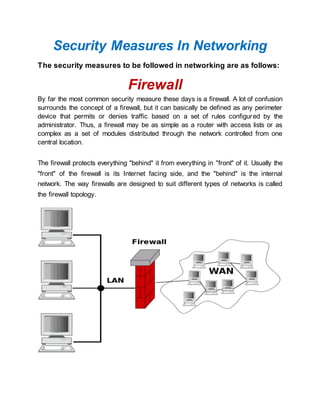
- 1. Security Measures In Networking The security measures to be followed in networking are as follows: Firewall By far the most common security measure these days is a firewall. A lot of confusion surrounds the concept of a firewall, but it can basically be defined as any perimeter device that permits or denies traffic based on a set of rules configured by the administrator. Thus, a firewall may be as simple as a router with access lists or as complex as a set of modules distributed through the network controlled from one central location. The firewall protects everything "behind" it from everything in "front" of it. Usually the "front" of the firewall is its Internet facing side, and the "behind" is the internal network. The way firewalls are designed to suit different types of networks is called the firewall topology.
- 2. These are packages meant for individual desktops and are fairly easy to use. The first thing they do is make the machine invisible to pings and other network probes. Most of them also let you choose what programs are allowed to access the Internet. Therefore, you can allow your browser and mail client, but if you see some suspicious program trying to access the network, you can disallow it. This is a form of egress filtering or outbound traffic filtering and provides very good protection against Trojan horse programs and worms. However, firewalls are no cure-all solution to network security woes. A firewall is only as good as its rule set, and there are many ways an attacker can find commonmisconfigurations and errors inthe rules. For example, if the firewall blocks all traffic except traffic originating from port 53 (DNS) so that everyone can resolve names, the attacker could then use this rule to his advantage. By changing the source port of his attack or scan to port 53, the firewall will allow all of his traffic through, because it assumes it is DNS traffic. Bypassing firewalls is a whole study in itself and one which is very interesting (especially to those with a passion for networking), because it normally involves misusing the way TCP and IP are supposed to work. That said, firewalls today are becoming very sophisticated and a well-installed firewall can severely thwart a would-be attacker's plans. It is important to remember that the firewall does not lookinto the data section of the packet. Thus, if you have a Web server that is vulnerable to a CGI exploit and the firewall is set to allow traffic to it, there is no way the firewall can stop an attacker from attacking the Web server. It does not look at the data inside the packet. That would be the job of an intrusion- detection system (covered in part three). Antivirus systems Everyone is familiar with the desktop version of antivirus packages like Norton Antivirus and McAfee. The way these operate is fairly simple -- when researchers find a new virus, they figure out some unique characteristic it has (maybe a registry key it creates or a file it replaces) and out of this they write the virus "signature."
- 3. The whole load of signatures for which your antivirus software scans is known as the virus "definitions." This is the reason why keeping your virus definitions up-to-date is very important. Many antivirus packages have an auto-update feature for you to download the latest definitions. The scanning ability of your software is only as good as the date of your definitions. In the enterprise, it is very common for administrators to install antivirus software onall machines, but there is no policy for regular updates of the definitions. This is meaningless protection and serves only to provide a false sense of security. With the recent spread of e-mail viruses, antivirus software at the mail server is becoming increasingly popular. The mail server will automatically scan any e-mail it receives for viruses and quarantine the infections. The idea is that since all mail passes through the mail server, this is the logical point to scan for viruses. Given that most mail servers have a permanent connection to the Internet, they can regularly download the latest definitions. On the downside, these can be evaded quite simply. If you zip up the infected file or Trojan, or encrypt it, the antivirus system may not be able to scan it. End users must be taught how to respond to antivirus alerts. This is especially true in the enterprise -- anattacker doesn't needto tryand bypass your fortress-like firewall if all he has to do is e-mail Trojans to a lot of people inthe company. It takes just one uninformed user to open the infected package to allow the hacker a backdoor to the internal network. It is advisable that the IT department gives a brief seminar on how to handle e-mail from untrusted sources and how to deal with attachments.
- 4. Intrusion-detection systems There are basicallytwo types of intrusion-detectionsystems (IDS): Host-basedIDS Network-basedIDS Host-based IDS: These systems are installed on a particular important machine (usually a server or some important target) and are tasked with making sure that the system state matches a particular set baseline. For example, the popular file-integrity checker Tripwire is run on the target machine just after it has been installed. It creates a database of file signatures for the system and regularly checks the current system files against their known safe signatures. If a file has been changed, the administrator is alerted. This works very well because most attackers will replace a common system file with a trojaned version to give them backdoor access.
- 5. Network-based IDS: These systems are more popular and quite easy to install. Basically, they consist of a normal network sniffer running in promiscuous mode. (In this mode, the network card picks up all traffic even if it is not meant for it.) The sniffer is attached to a database of known attack signatures, and the IDS analyzes each packet that it picks up to check for known attacks. For example, a common Web attack might contain the string /system32/cmd.exe? in the URL. The IDS will have a match for this in the database and will alert the administrator. Newer versions of IDS support active prevention of attacks. Instead of just alerting an administrator, the IDS can dynamically update the firewall rules to disallow traffic from the attacking IP address for some amount of time. Or the IDS can use "session sniping"to fool both sides of the connection into closing down so that the attack cannot be completed. Unfortunately, IDS systems generate a lot of false positives. A false positive is basically a false alarm, where the IDS sees legitimate traffic and for some reason matches it against an attack pattern. This tempts a lot of administrators into turning them off or even worse -- not bothering to read the logs. This may result in an actual attack being missed. IDS evasion is also not all that difficult for an experienced attacker. The signature is based on some unique feature of the attack, and so the attacker can modify the attack so that the signature is not matched. For example, the above attack string /system32/cmd.exe? could be rewritten in hexadecimal to look something like: '2f%73%79%73%74%65%6d%33%32%2f%63%6d%64%2e%65%78%65%3f' This might be totally missed by the IDS. Furthermore, an attacker could split the attack into many packets by fragmenting the packets. This means that each packet would only contain a small part of the attack, and the signature would not match. Even if the IDS is able to reassemble fragmented packets, this creates a time overhead and since the IDS has to run at near real-time status, they tend to drop packets while they are processing. IDS evasion is a topic for a paper on its own. The advantage of a network-based IDS is that it is very difficult for anattacker to detect. The IDS itself does not need to generate any traffic, and, in fact, many of them have a broken TCP/IP stack so that they don't have an IP address. Thus the attacker does not know whether the network segment is being monitored or not.
- 6. Patching and updating It is embarrassing and sad that this has to be listed as a security measure. Despite being one of the most effective ways to stop an attack, there is a tremendously laid-back attitude to regularly patching systems. There is no excuse for not doing this, and yet the level of patching remains woefully inadequate. Take, for example, the MS blaster worm that spread havoc recently. The exploit was known almost a month in advance and a patch had been released. Still, millions of users and businesses were infected. While administrators know that having to patch 500 machines is a laborious task, the way I look at it is that I would rather be updating my systems on a regular basis than waiting for disaster to strike and then running around trying to patch and clean up those 500 systems. In the enterprise, there is no "easy" way to patch large numbers of machines, but there are patch deployment mechanisms that take a lot of the burden away. Frankly, it is part of an admin's job to do this, and when a network is horribly fouled up by the latest worm, it just means that someone, somewhere didn't do his job well enough. Now that we've concluded a brief introduction to the types of threats faced in the enterprise, it is time to have a look at some of the tools that attackers use.
- 7. Keep in mind that a lot of these tools have legitimate purposes and are very useful to administrators as well. For example, I can use a network sniffer to diagnose a low-level network problem or I can use it to collect your password. It just depends which shade of hat I choose to wear. General network tools As surprisingas it might sound, some of the most powerful tools, especially in the beginning stages of an attack, are the regular network tools available with most operating systems. For example, an attacker will usually query the "whois" databases for information on the target. After that, he might use "nslookup" to see if he can transfer the whole contents of the DNS zone. This will let him identify high-profile targets such as Web servers, mail servers, and DNS servers. He might also be able to figure what different systems do based on their DNS name; for example, sqlserver.victim.com would most likely be a database server. Other important tools include trace route to map the network and ping to check which hosts are alive. You should make sure your firewall blocks ping requests and trace route packets.
- 8. Port scanners Most of you will know what port scanners are. Any system that offers TCP or UDP services will have an open port for that service. For example, if you're serving up Web pages, you'll likely have TCP port 80 open. FTP is TCP port 20/21, Telnet is TCP 23, SNMP is UDP port 161 and so on. A port scanner scans a host or a range of hosts to determine what ports are open and what service is running on them. This tells the attacker which systems can be attacked. For example, if I scan a Web server and find that port 80 is running an old Web server, like IIS/4.0, I can target this system with my collection of exploits for IIS 4. Usually the port scanning will be conductedat the start of the attack, to determine whichhosts are interesting. This is when the attacker is still footprinting the network -- feeling his way around to get an idea of what type of services are offered and what operating systems are in use. One of the best port scanners around is Nmap (http://www.insecure.org/nmap). Nmap runs on just about every operating system, is very versatile and has many features including OS fingerprinting, service version scanning and stealth scanning. Another popular scanner is Superscan (http://www.foundstone.com), which is only for the windows platform.
- 9. Network sniffers A network sniffer puts the computer's NIC (network interface card or LAN card) into promiscuous mode. In this mode, the NIC picks up all the traffic on its subnet regardless of whether it was meant for it or not. Attackers set up sniffers so that they can capture all the network traffic and pull out log-ins and passwords. The most popular network sniffer is TCPdump. It can be run from the command line, which is usually the level of access a remote attacker will get. Other popular sniffers are Iris and Ethereal. When the target network is a switched environment (a network which uses Layer 2 switches), a conventional network scanner will not be of any use. For such cases, the switched network sniffer Ettercap (http://ettercap.sourceforge.net) is very popular. It allows the attacker to collect passwords, hijack sessions, modify ongoing connections and kill connections. It can even sniff securedcommunicationslike SSL (Secure Sockets Layer, used for secure Web pages) and SSH1 (Secure Shell, a remote access service like telnet, but encrypted). There are also programs that allow an admin to detect whether any NICs are running in promiscuous mode.
- 10. Vulnerability scanners A vulnerability scanner is like a port scanner on steroids. Once it has identified which services are running, it checks the system against a large database of known vulnerabilities and then prepares a report on the security holes that are found. The software can be updated to scan for the latest securityholes. These tools are verysimple to use, so many script kiddies point them at a target machine to find out what they can attack. The most popular ones are Retina (http://www.eeye.com), Nessus (http://www.nessus.org) and GFI Lan Scan (http://www.gfi.com). These are very useful tools for administrators, as well, because they can scan their whole network and get a detailed summary of the holes that exist. Made by: Ayush Singh