Ransomware Explained
•
0 j'aime•103 vues
Ransomware attacks—a type of malware (a.k.a. malicious software)— are proliferating around the globe at a blistering pace. In this infographic, learn what to do if you fall prey to an attack, and how data can be protected with cloud backups and disaster recovery.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
Contenu connexe
Similaire à Ransomware Explained
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
Similaire à Ransomware Explained (20)
Are ransomware attacks the problem for web hosting firms?

Are ransomware attacks the problem for web hosting firms?
The Most Common Enterprise Malware and how to identify them

The Most Common Enterprise Malware and how to identify them
Corporations - the new victims of targeted ransomware

Corporations - the new victims of targeted ransomware
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About Ransomware
Advanced Threats in the Enterprise: Finding an Evil in the Haystack

Advanced Threats in the Enterprise: Finding an Evil in the Haystack
Panda Adaptive Defense 360 - Cyber Extortion Guide

Panda Adaptive Defense 360 - Cyber Extortion Guide
Dernier
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Dernier (20)
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu

Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Ransomware Explained
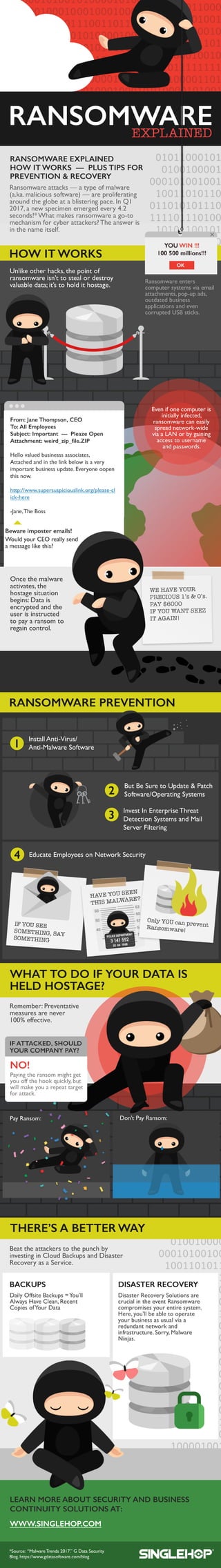
- 1. Unlikeotherhacks,thepointof ransomwareisn’ttostealordestroy valuabledata;it’stoholdithostage. HOW ITWORKS RANSOMWAREPREVENTION RANSOMWAREEXPLAINED HOW ITWORKS— PLUSTIPSFOR PREVENTION&RECOVERY Ransomwareenters computersystemsviaemail attachments,pop-upads, outdatedbusiness applicationsandeven corruptedUSBsticks. Ransomwareattacks— atypeofmalware (a.ka.malicioussoftware)— areproliferating aroundtheglobeatablisteringpace.InQ1 2017,anewspecimenemergedevery4.2 seconds!*Whatmakesransomwareago-to mechanismforcyberattackers?Theansweris inthenameitself. Beattheattackerstothepunchby investinginCloudBackupsandDisaster RecoveryasaService. PayRansom: DailyOffsiteBackups=You’ll AlwaysHaveClean,Recent CopiesofYourData Don’tPayRansom: poster poster poster RANSOMWARE WEHAVEYOUR PRECIOUS1’s&0’s. PAY$6000 IFYOUWANTSEEZ ITAGAIN! 1 2 3 4 IFYOUSEE SOMETHING,SAY SOMETHING HAVEYOUSEEN THISMALWARE? Remember:Preventative measuresarenever 100%effective. WHATTODOIFYOURDATAIS HELDHOSTAGE? DisasterRecoverySolutionsare crucialintheeventRansomware compromisesyourentiresystem. Here,you’llbeabletooperate yourbusinessasusualviaa redundantnetworkand infrastructure.Sorry,Malware NinjasNinjas. THERE’SABETTERWAY BACKUPS DISASTERRECOVERY *Source:“MalwareTrends2017.”GDataSecurity Blog.https://www.gdatasoftware.com/blog Evenifonecomputeris initiallyinfected, ransomwarecaneasily spreadnetwork-wide viaaLANorbygaining accesstousername andpasswords. Bewareimposteremails! WouldyourCEOreallysend amessagelikethis? Oncethemalware activates,the hostagesituation begins:Datais encryptedandthe userisinstructed topayaransomto regaincontregaincontrol. ButBeSuretoUpdate&Patch Software/OperatingSystems EducateEmployeesonNetworkSecurity InstallAnti-Virus/ Anti-MalwareSoftware InvestInEnterpriseThreat DetectionSystemsandMail ServerFiltering Payingtheransommightget youoffthehookquickly,but willmakeyouarepeattarget forattack. IFATTACKED,SHOULD YOURCOMPANYPAY? NO! RANSOMWAREEXPLAINED OnlyYOUcanpreventRansomware!
