diagram_sources.pptx
•Télécharger en tant que PPTX, PDF•
0 j'aime•7 vues
Authorization code authentication flow
Signaler
Partager
Signaler
Partager
Recommandé
Recommandé
Contenu connexe
Similaire à diagram_sources.pptx
Similaire à diagram_sources.pptx (20)
(DEV203) Amazon API Gateway & AWS Lambda to Build Secure APIs

(DEV203) Amazon API Gateway & AWS Lambda to Build Secure APIs
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
Keycloak for Science Gateways - SGCI Technology Sampler Webinar

Keycloak for Science Gateways - SGCI Technology Sampler Webinar
Client Initiated Backchannel Authentication (CIBA) and Authlete’s Approach

Client Initiated Backchannel Authentication (CIBA) and Authlete’s Approach
Microservice security with spring security 5.1,Oauth 2.0 and open id connect 

Microservice security with spring security 5.1,Oauth 2.0 and open id connect
Spring Social - Messaging Friends & Influencing People

Spring Social - Messaging Friends & Influencing People
Securing Serverless Workloads with Cognito and API Gateway Part I - AWS Secur...

Securing Serverless Workloads with Cognito and API Gateway Part I - AWS Secur...
Using ArcGIS with OAuth 2.0 - Esri DevSummit Dubai 2013

Using ArcGIS with OAuth 2.0 - Esri DevSummit Dubai 2013
Dernier
Call Girl Aurangabad Indira Call Now: 8617697112 Aurangabad Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Aurangabad Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Aurangabad understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7

(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Call Girl Bhosari Indira Call Now: 8617697112 Bhosari Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Bhosari Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Bhosari understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Bhosari Call Now 8617697112 Bhosari Escorts 24x7

(INDIRA) Call Girl Bhosari Call Now 8617697112 Bhosari Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Dernier (20)
VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking

VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking
Call Girls In Bangalore ☎ 7737669865 🥵 Book Your One night Stand

Call Girls In Bangalore ☎ 7737669865 🥵 Book Your One night Stand
CCS335 _ Neural Networks and Deep Learning Laboratory_Lab Complete Record

CCS335 _ Neural Networks and Deep Learning Laboratory_Lab Complete Record
chapter 5.pptx: drainage and irrigation engineering

chapter 5.pptx: drainage and irrigation engineering
The Most Attractive Pune Call Girls Budhwar Peth 8250192130 Will You Miss Thi...

The Most Attractive Pune Call Girls Budhwar Peth 8250192130 Will You Miss Thi...
Roadmap to Membership of RICS - Pathways and Routes

Roadmap to Membership of RICS - Pathways and Routes
Double Revolving field theory-how the rotor develops torque

Double Revolving field theory-how the rotor develops torque
(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7

(INDIRA) Call Girl Aurangabad Call Now 8617697112 Aurangabad Escorts 24x7
Call for Papers - African Journal of Biological Sciences, E-ISSN: 2663-2187, ...

Call for Papers - African Journal of Biological Sciences, E-ISSN: 2663-2187, ...
Call Girls Wakad Call Me 7737669865 Budget Friendly No Advance Booking

Call Girls Wakad Call Me 7737669865 Budget Friendly No Advance Booking
(INDIRA) Call Girl Bhosari Call Now 8617697112 Bhosari Escorts 24x7

(INDIRA) Call Girl Bhosari Call Now 8617697112 Bhosari Escorts 24x7
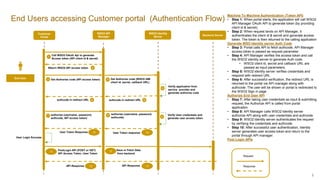
diagram_sources.pptx
- 1. 1 End Users accessing Customer portal (Authentication Flow) Customer Portal 1 3 Call WSO2 OAuth Api to generate Access token (API client id & secret) Return WSO2 API access token WSO2 API Manager WSO2 Identity Server authcode in redirect URL 4 , Verify application from service provider and generate authorize code authcode in redirect URL End User 5 Get Authorize code (WSO2 IAM client id, secret, callback URL) User Login Success Response Request Get Authorize code (API access token) 2 6 6 7 authorize (username, password, authcode, API access token) 8 authorize (username, password, authcode) User Token response Verify User credentials and generate user access token 9 PostLogin API (POST or GET) API Access Token, User Token Backend Server User Token Response 13 Save or Fetch Data from backend API Response 10 API Response Machine To Machine Authentication (Token API) • Step 1: When portal starts, the application will call WSO2 API Manager OAuth API to generate token (by providing client id & secret). • Step 2: When request lands on API Manager, it authenticates the client id & secret and generate access token. The token is then returned to the calling application Generate WSO Identity server Auth Code • Step 3: Portal calls API to fetch authcode. API Manager access token is passed as request parameter. • Step 4: API Manager verifies the access token and call the WSO2 identity server to generate Auth code. • WSO2 client id, secret and callback URL are passed as input parameters. • Step 5: WSO2 identity server verifies credentials and respond with redirect URL • Step 6: After successful verification, the redirect URL is returned to the portal via API manager along with authcode. The user will be shown or portal is redirected to the WSO2 Sign in page Authorize End User API • Step 7: After taking user credentials as input & submitting request, the Authorize API is called from portal application. • Step 8: API Manager calls WSO2 Identity server authorize API along with user credentials and authcode. • Step 9: WSO2 Identity server authenticates the request by verifying the credentials and authcode. • Step 10: After successful user authentication, Identity server generates user access token and return to the portal through API manager. Post Login APIs 10 11 12 13