Ransomware Infographic - Are you protected?
•
1 j'aime•2,428 vues
Ransomware has quickly emerged as one of the most dangerous cyber threats facing both organizations and consumers, with global losses now likely running to hundreds of millions of dollars. Adopting the Veritas unified approach to backup helps ensure you are protected, regardless of where your data resides. With the Desktop and Laptop Option (DLO) you can even protect user files on up to 130,000 desktops and laptops, Windows and Mac. Please feel free to download this infographic and share within your social networks.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
We are experiencing IT climate change. Inundated we are, daily, with a barrage of “Cloud-ready” solutions that promise to transform, supercharge or in some other way substantial improve your business. Truth is, we’ve all seen this movie before and there is no ending, only a story arch. Technologies come and go and our ability to maximize the return on these solutions is what we makes for a successful adoption. Ask yourself, with all of the promise of the public cloud, how much is hype vs. reality. More details in the presentation.
How to Extend Availability to the Application Layer Across the Hybrid Cloud -...

How to Extend Availability to the Application Layer Across the Hybrid Cloud -...Veritas Technologies LLC
The joint presentation session on Get trust and confidence to manage your data in hybrid-IT environments! with Mr Matsumoto, VP Fujitsu Cloud Service, Mr Takenoshita who is our end user, and Ryuta Takai, Director, Technology Sales of Veritas at Fujitsu Forum 2019 Tokyo on 17 May 2019. Get trust and confidence to manage your data in hybrid it environments japanese

Get trust and confidence to manage your data in hybrid it environments japaneseVeritas Technologies LLC
Recommandé
We are experiencing IT climate change. Inundated we are, daily, with a barrage of “Cloud-ready” solutions that promise to transform, supercharge or in some other way substantial improve your business. Truth is, we’ve all seen this movie before and there is no ending, only a story arch. Technologies come and go and our ability to maximize the return on these solutions is what we makes for a successful adoption. Ask yourself, with all of the promise of the public cloud, how much is hype vs. reality. More details in the presentation.
How to Extend Availability to the Application Layer Across the Hybrid Cloud -...

How to Extend Availability to the Application Layer Across the Hybrid Cloud -...Veritas Technologies LLC
The joint presentation session on Get trust and confidence to manage your data in hybrid-IT environments! with Mr Matsumoto, VP Fujitsu Cloud Service, Mr Takenoshita who is our end user, and Ryuta Takai, Director, Technology Sales of Veritas at Fujitsu Forum 2019 Tokyo on 17 May 2019. Get trust and confidence to manage your data in hybrid it environments japanese

Get trust and confidence to manage your data in hybrid it environments japaneseVeritas Technologies LLC
This presentation from the Gartner IT Infrastructure Operations & Cloud Strategies Conference is about the rise of the modern workload. Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...

Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...Veritas Technologies LLC
This includes two presentations on 360 data management, as well as how to take control over the most valuable asset in your enterprise - data. VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...

VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...Veritas Technologies LLC
In "Modernizing your organization's data protection approach," Yamen Alahmad provides insight to Veritas' strategy.Modernizing your organization's data protection approach, with Yamen Alahmad

Modernizing your organization's data protection approach, with Yamen AlahmadVeritas Technologies LLC
Contenu connexe
Plus de Veritas Technologies LLC
This presentation from the Gartner IT Infrastructure Operations & Cloud Strategies Conference is about the rise of the modern workload. Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...

Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...Veritas Technologies LLC
This includes two presentations on 360 data management, as well as how to take control over the most valuable asset in your enterprise - data. VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...

VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...Veritas Technologies LLC
In "Modernizing your organization's data protection approach," Yamen Alahmad provides insight to Veritas' strategy.Modernizing your organization's data protection approach, with Yamen Alahmad

Modernizing your organization's data protection approach, with Yamen AlahmadVeritas Technologies LLC
Plus de Veritas Technologies LLC (20)
VSD Paris 2018: Vertical Use Case - Banking, Finance, Insurance

VSD Paris 2018: Vertical Use Case - Banking, Finance, Insurance
Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...

Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...
VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...

VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...
VSD Zurich 2018: The Secret to Successful Digital Transformation

VSD Zurich 2018: The Secret to Successful Digital Transformation
Take Control Over Storage Costs with Intuitive Management and Simplicity

Take Control Over Storage Costs with Intuitive Management and Simplicity
VSD Seoul 2018: VMware Cloud Foundation on "The Future of Private Cloud"

VSD Seoul 2018: VMware Cloud Foundation on "The Future of Private Cloud"
VSD Seoul 2018: a Veritas customer case with Meritz Fire Insurance

VSD Seoul 2018: a Veritas customer case with Meritz Fire Insurance
VSD Seoul 2018: modern workload protection with NetBackup

VSD Seoul 2018: modern workload protection with NetBackup
Get your enterprise backup strategy ready for the digital world

Get your enterprise backup strategy ready for the digital world
Complete data management with Veritas, with Virgil Dobos

Complete data management with Veritas, with Virgil Dobos
Modernizing your organization's data protection approach, with Yamen Alahmad

Modernizing your organization's data protection approach, with Yamen Alahmad
Cloud fundamentals, with Kevin Ashby and Brett Samuel

Cloud fundamentals, with Kevin Ashby and Brett Samuel
Dernier
Dernier (20)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Ransomware Infographic - Are you protected?
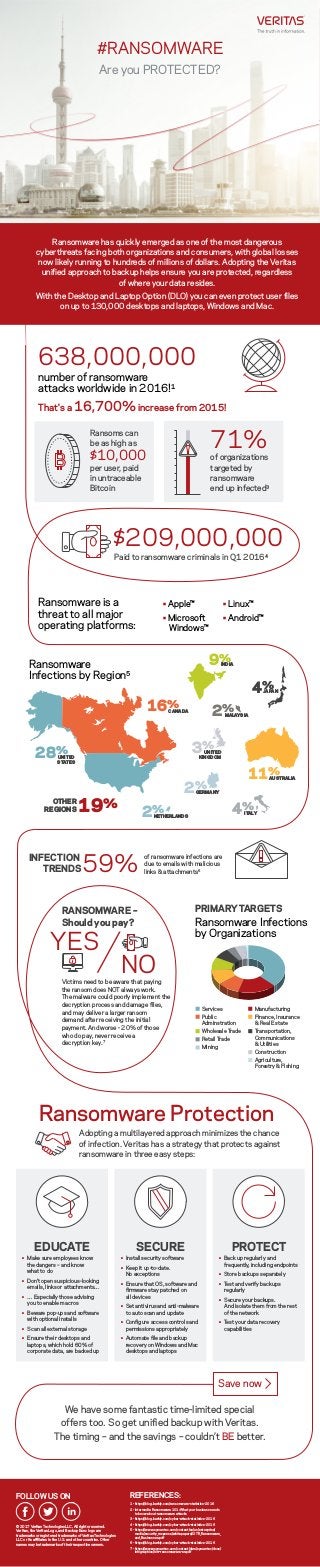
- 1. Ransomware Infections by Region5 #RANSOMWARE Are you PROTECTED? Ransomware has quickly emerged as one of the most dangerous cyberthreats facing both organizations and consumers, with global losses now likely running to hundreds of millions of dollars. Adopting the Veritas unified approach to backup helps ensure you are protected, regardless of where your data resides. With the Desktop and Laptop Option (DLO) you can even protect user files on up to 130,000 desktops and laptops, Windows and Mac. Adopting a multilayered approach minimizes the chance of infection. Veritas has a strategy that protects against ransomware in three easy steps: 638,000,000 number of ransomware attacks worldwide in 2016!1 Ransomware is a threat to all major operating platforms: PRIMARYTARGETS $209,000,000 Ransomware Protection That's a 16,700% increase from 2015! Ransoms can be as high as $10,000 per user, paid in untraceable Bitcoin Paid to ransomware criminals in Q1 20164 71% of organizations targeted by ransomware end up infected3 INFECTION TRENDS59% of ransomware infections are due to emails with malicious links & attachments6 Ransomware Infections by Organizations Services Public Adminstration Wholesale Trade Retail Trade Mining Manufacturing Finance, Insurance & Real Estate Transportation, Communications & Utilities Construction Agriculture, Forestry & Fishing Save now FOLLOW US ON © 2017 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and Backup Exec logo are trademarks or registered trademarks of Veritas Technologies LLC or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. REFERENCES: 1 - https://blog.barkly.com/ransomware-statistics-2016 2 - Intermedia Ransomware 101: What your business needs to know about ransomware attacks 3 - https://blog.barkly.com/cyber-attack-statistics-2016 4 - https://blog.barkly.com/cyber-attack-statistics-2016 5 - https://www.symantec.com/content/en/us/enterprise/ media/security_response/whitepapers/ISTR_Ransomware_ and_Businesses.pdf 6 - https://blog.barkly.com/cyber-attack-statistics-2016 7 - https://www.symantec.com/content/dam/symantec/docs/ infographics/istr-ransomeware-en.pdf We have some fantastic time-limited special offers too. So get unified backup with Veritas. The timing – and the savings – couldn’t BE better. EDUCATE • Make sure employees know the dangers – and know what to do • Don't open suspicious-looking emails, links or attachments… • … Especially those advising you to enable macros • Beware pop-ups and software with optional installs • Scan all external storage • Ensure their desktops and laptops, which hold 60% of corporate data, are backed up PROTECT • Back up regularly and frequently, including endpoints • Store backups separately • Test and verify backups regularly • Secure your backups. And isolate them from the rest of the network • Test your data recovery capabilities SECURE • Install security software • Keep it up-to-date. No exceptions • Ensure that OS, software and firmware stay patched on all devices • Set antivirus and anti-malware to auto scan and update • Configure access controls and permissions appropriately • Automate file and backup recovery on Windows and Mac desktops and laptops RANSOMWARE – Should you pay? YES NOVictims need to be aware that paying the ransom does NOT always work. The malware could poorly implement the decryption process and damage files, and may deliver a larger ransom demand after receiving the initial payment. And worse - 20% of those who do pay, never receive a decryption key.7 UNITED STATES 28% 19%OTHER REGIONS UNITED KINGDOM 3% CANADA16% AUSTRALIA11% JAPAN4% INDIA9% MALAYSIA2% ITALY4% NETHERLANDS2% GERMANY2% • Apple™ • Linux™ • Android™• Microsoft Windows™
